SSL
| Encryption is the process of rendering a sequence of data unreadable. Typically this process utilizes one or more data strings known as keys. Public key encryption is a method of scrambling data using one key, key A, in such a way that it can later be unscrambled, but only with the use of a second key, key B. Data encrypted using key A is decryptable with key B. Data encrypted with key B is decryptable only with key A. One of the keys is handed out freely to the general public (the "public key") and the other is kept a closely guarded secret (the "private key"). Those who wish to communicate with you securely obtain your public key and use it to encrypt messages. Upon receipt of the encrypted message, you use your private key to decrypt the message and perhaps compose a response. CertificatesCertificates are the way you inform the Web-browsing public that you are who you say you are. A certificate is nothing more than a public/private key pair obtained from some trusted source. Because a key pair is nothing more than a long sequence of numbers , it is possible to construct a functioning key for yourself without much difficulty. However, unless you are using a commercially signed certificate, most client browsers will display some kind of warning message to their users when they begin SSL communication. You use the private key provided by the certificate authority to encrypt some data. When a client requests a secure connection, you respond with the following items:
The client uses the public key of the certificate authority to decrypt the message which you transmitted. The decrypted message contains your public key. Next, you send the client a message which you have encrypted using your private key. The message contains some data encrypted using your public key. Using your trusted public key that it obtained the first step, it decrypts the message you just sent. It encrypts the plain text message and compares the result with the contents of the second message. If they match, the client will conclude you are who you say you are, and business can commence. Commercial certificates can be purchased from
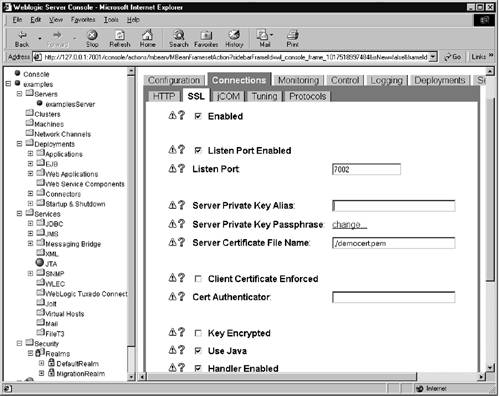
Once they have been purchased and installed in the directory tree, you are ready to begin configuring SSL. Configuring SSLIn 6.x, the SSL configuration pane is accessed by clicking on the particular server for which you wish to perform configuration, then clicking on the SSL tab. In 7.x, the SSL tab is found under the connections tab. (See Figure 11-1.) Figure 11-1. Server 7.x SSL Tab Either way, there are four fields of interest:
By default, the server does not require clients to have certificates of their own. However, you can override this and deny communication to any client that lacks a valid certificate. To do so, check the "Client Certificate Enforced" box in the SSL tab. |
EAN: 2147483647
Pages: 134