Basic Security Concepts, Strengths, and Vulnerabilities of Security Topologies
Basic Security Concepts, Strengths, and Vulnerabilities of Security TopologiesThe concepts of security topologies are based on securing the communication between devices on the network. Topologies consist of security zones that are created using hardware devices. This section provides an overview of how firewalls are used to segment the network into security zones and create various security topologies. It will also help you understand basic security concepts, strengths, and vulnerabilities of security topologies and be able to explain the strengths and vulnerabilities of these topologies. Security ZonesTo understand security zones, we must first discuss the major types of firewall architectures or security topologies. They are as follows :
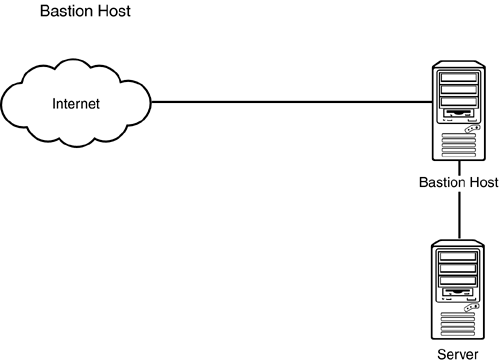
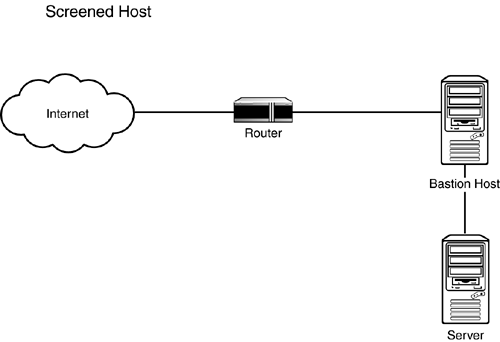
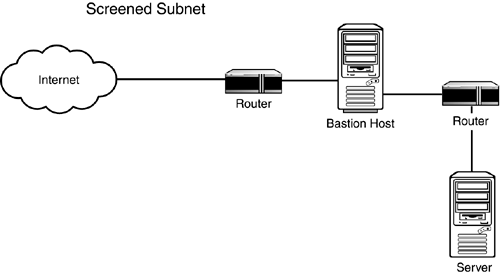
Bastion HostA bastion host is the first line of security that a company allows to be addressed directly from the Internet. Figure 6.2 shows how a bastion host works. It is designed to screen the rest of its network from security exposure. It is the device that the firewall software is installed on, and it supports packet filtering, proxy, and hybrid firewall applications, such as a dual- homed host, where there are two NICs. A bastion host can be a router running access lists or a PC running an operating system that supports some kind of routing rules definition or traffic-filtering mechanism. Bastion hosts can also be used for Web, email, FTP, or DNS servers. Figure 6.2. A bastion host. Bastion host solutions are most common to small networks or remote locations. Because each host has a specific role, all unnecessary services and protocols should be uninstalled . The server's operating system and software also needs to be hardened . This process is discussed in Chapter 7. Screened Host GatewayA screened host gateway is implemented using a screening router and a bastion host. The bastion host is on the private network and communicates directly with a border router. The screening router blocks traffic by packet filtering; it may also block traffic on specific ports, as shown in Figure 6.3. The bastion host serves as a choke point through which all traffic flows. This network design includes an application gateway. Traffic coming in from the Internet gets filtered through the router based on what is allowed. If it is allowed, the traffic gets forwarded to the application gateway. The application gateway then redirects it to the appropriate server or a workstation. The process works essentially backwards for outgoing communications. Figure 6.3. A screened host gateway. Compared to bastion host, the screened host gateway is more likely to let certain types of offending traffic in. In the case of a bastion host, all rules are configured on one device. With application gateways, two devices need to be configured. This leaves room for error. Another reason why this could be less secure is because the packet filter is configured quite liberally, usually allowing "all or none." The requests are then forwarded to the application gateway, where the majority of the filtering is done. If configured properly, this is a good solution because two devices would have to be compromised. Screened Subnet GatewayThe third type is called a screened subnet gateway . Screened subnet gateway architecture includes two screened host gateway devices that isolate the LAN from the Internet. Essentially, this is an isolated subnet between the Internet and the internal network, as shown in Figure 6.4. Figure 6.4. A screened subnet gateway. With a screened subnet, two local subnet IP addresses are needed. Both the Internet and the private network have access to the screened subnet, but neither can access each other. Therefore, one subnet is needed for the internal network and one is needed for the screened subnet. This type of setup is recommended because traffic is controlled more finely and it isolates the internal network by more than one layer of security. Public inbound traffic is allowed only in the DMZ subnet. Outbound traffic flows through the DMZ, which creates anonymity for the requesting clients on the LAN. Disadvantages of this architecture are complex implementation and possible breaches when packets are allowed from the borderline firewall through the DMZ and into the internal network. This topology is by far the most flexible and secure, where one can completely eliminate direct outside-to-inside communications and conduct everything through a strictly controlled area called a DMZ. DMZA demilitarized zone (DMZ) is a small network between the internal network and the Internet that provides a layer of security and privacy. This configuration is described in the previous screened subnet gateway section. Both internal and external users have limited access to the servers in this area. Often Web and mail servers are placed in the DMZ. Because these devices are exposed to the Internet, it is important that they are hardened and patches are kept current. See Table 6.1 for a list of the most common services and ports that are run on servers inside the DMZ.
Table 6.1. Commonly Used Ports
IntranetAn intranet is a portion of the internal network that uses Web-based technologies. The information is stored on Web servers and accessed using browsers. Although Web servers are used, they don't necessarily have to be accessible to the outside world. This is possible because the IP addresses of the servers are reserved for private, internal use. We will go over private IP addresses in the "NAT" section, later in this chapter. If the intranet can be accessed from public networks, it should be through a VPN for security reasons. ExtranetAn extranet is the public portion of the company's IT infrastructure that allows resources to be used by authorized partners and resellers that have proper authorization and authentication. This type of arrangement is commonly used for business-to-business relationships. Because an extranet can provide liability for a company, care must be taken to ensure that VPNs and firewalls are configured properly and that security policies are strictly enforced. VLANsVLAN is short for virtual local area network , and its purpose is to unite network nodes logically into the same broadcast domain regardless of their physical attachment to the network. VLANs provide a way to limit broadcast traffic in a switched network. This creates a boundary and, in essence, creates multiple, isolated LANs on one switch. Because switches operate on layer 2 of the OSI model, if data is to be passed from one VLAN to another, a router is required.
Frame tagging is the technology used for VLANs. The 802.1Q standard defines a mechanism that encapsulates the frames with headers, which then tags them with a VLAN ID. VLAN-aware network devices look for these tags in frames and make appropriate forwarding decisions. A VLAN is basically a software solution that allows creating unique tag identifiers to be assigned to different ports on the switch. For more information on frame tagging and VLANs, see the "Need to Know More?" section at the end of the chapter. The most notable benefit of using a VLAN is that it can span multiple switches. Because users on the same VLAN don't have to be associated by physical location, they can be grouped by department or function. Here are the benefits that VLANs provide:
Keep in mind that using a VLAN is not to be considered an absolute safeguard against security infringements. It does not provide the same level of security as a router. A VLAN is a software solution and cannot take the place of a well- subnetted or routed network. It is possible to make frames hop from one VLAN to another. This takes skill and knowledge on the part of an attacker, but it is possible. NATNetwork Address Translation (NAT) acts as a liaison between an internal network and the Internet. It allows multiple computers to connect to the Internet using one IP address. In this situation, the internal network uses a private IP address. Special ranges in each IP class are used specifically for private addressing. These addresses are considered nonroutable on the Internet. Here are the private address ranges:
For smaller companies, NAT can be used in the form of Windows Internet Connection Sharing (ICS), where all machines share one Internet connection, such as a dial-up modem. NAT can also be used for address translation between multiple protocols, which improves security and provides for more interoperability in heterogeneous networks.
TunnelingTunneling involves one network sending its data through the connection of another network. It works by encapsulating a network protocol within packets carried by the public network. A common approach to tunneling is Point-to-Point Tunneling Protocol (PPTP) technology, which embeds its own network protocol within the TCP/IP packets carried by the Internet. Layer 2 Tunneling Protocol (L2TP) can also be used. Tunneling should not be used as a substitute for encryption. The strongest level of encryption possible needs to be used within the VPN. The downside of tunneling is that for the firewall to establish the tunnel, a set of rules needs to be configured to permit such activity. Once the VPN tunnel is created, it is considered a channel that has already passed security checks. In addition, when encryption is used within a tunnel, it is not possible to filter the packets because the firewall does not see the encrypted contents. Practice Questions
|
EAN: 2147483647
Pages: 162