Overview of Group Policy
| In a nutshell, group policy allows an administrator to apply settings to users and computers on the network in a managed and granular fashion. Specifically, the tasks listed in Table 20.1 can be managed through group policy.
As Table 20.1 implies, some group policy settings apply to computers, and some apply to users. Logon and logoff scripts would only apply to users when they log on and off the network. Startup and shutdown scripts would only apply to computers. This is only one way that group policy is broken down into logical parts. The next section discusses in more detail the different components that make up group policy. Group Policy ElementsEach user or computer policy has three main sections: Software Settings, Windows Settings, and Administrative Templates. Each individual policy element is stored in one of these three areas in either the user or computer policy group. Software SettingsPolicy elements under this section relate to the installation, update, or removal of software on computers on the network. Software policies enabled in the computer configuration apply to all users who log on to the workstation affected by the policy. This is useful to make an application available to all users of a workstation. Software policies enabled in the user configuration apply to the users identified in the group policy object (GPO) no matter which workstation they use. If a user needs to have an application available to her wherever she logs in, you would set the policy element in the user configuration. Windows SettingsPolicy elements under this section relate to scripts, security settings, folder redirection, and many other settings stored in this area. There is a significant difference in the settings between the computer configuration and user configuration. Table 20.2 lists and describes some of the policy elements and whether they apply to users or computers.
Administrative TemplatesPolicy settings in this section generally apply to the environment the user or computer account operates in. Settings applied through Administrative Templates are stored in the computer's Registry: User configuration settings are placed in the HKEY_CURRENT_USER (HKCU) hive, and computer configuration settings are placed in the HKEY_LOCAL_MACHINE (HKLM) hive. Settings in the computer configuration apply to all users who log on to the workstation, and settings in the user configuration apply to the user no matter which workstation in the domain he uses. Group Policy Scope and Order of ApplicationOne of the most important features of group policy is that more than one policy can be applied depending on the domain configuration. This aids in the management and planning of policy for the entire network while affording a level of granularity not possible prior to Active Directory. Each group of settings is bundled into a GPO. The GPO contains not only the computer and user policy settings but also the security settings and filters that determine whether the policy gets applied to a specific user or computer. Specific rules determine the order in which policy elements are applied: local, site, domain, and organizational unit (OU). The following list describes the function of each:
Note Group policy can be applied only to organizational units, not containers. This is why the SBS wizards do not place user and computer objects into the Users and Computers containers. When users or computers are added manually in Active Directory and placed into these containers, the only GPOs that will be applied are the Local, Site, and Domain GPOs. No further fine-tuning of group policy can then take place. If settings conflicts occur between multiple GPOs, the settings in the most recently applied GPO take precedence. Figure 20.1 shows the processing order of GPOs in the SBS environment. Figure 20.1. Group Policy processing order.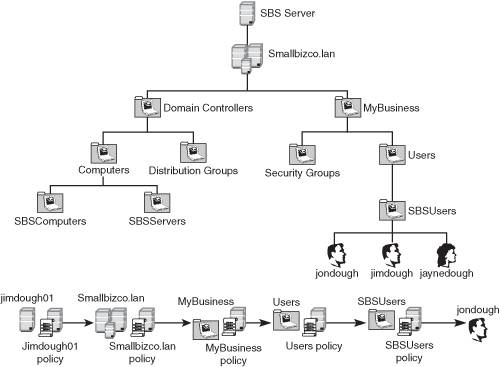 Group Policy FilteringBesides achieving some level of granularity in group policy assignment by assigning policies at different OU levels, you can also further control the application of group policy by security group and Windows Management Instrumentation (WMI) filters. In general, this level of granularity is probably not needed in the SBS environment, but it's nice to know it's available to you should you need it. Note WMI filtering of group policy was introduced with Windows XP. Windows 2000 workstations do not understand WMI filtering and as a result will not process any policy objects that have a WMI filter attached. Group Policy InheritanceGroup policy inheritance can be thought of in the same way as NTFS security inheritance. Policies that are set at a higher level in the processing order apply to objects later in the processing order. In some ways, this is really a misnomer because policies set at the domain level aren't really "inherited" by the lower-level objects. If a lower-level object does not override the settings, those settings will remain. Overriding Group Policy Processing OrderThere may be times when you want to have a domain-level policy apply no matter what settings are applied at the OU level. To achieve this, you would need to mark the policy object as Enforced. When a policy object is enforced, no subsequent policy settings can override settings contained in the enforced object. For example, a system administrator has set a policy in a domain GPO that sets all user desktop backgrounds to be a specific image file. Another administrator creates an OU GPO that sets the desktop background to be a different image file. Because the OU policy processes after the domain policy, the image set in the OU policy is what appears on the desktop of user objects within that OU. If the main administrator wants to have the domain GPO apply no matter what settings are changed in the OU GPO, the administrator can set the domain GPO as Enforced. Then when the OU GPO is processed, if any settings conflict between the OU GPO and the domain GPO, the settings in the domain GPO will still apply. Note Setting a GPO as Enforced only applies to settings defined in that GPO. A subsequent policy object can change any policy items that are undefined in a GPO that has been set as Enforced. |
EAN: 2147483647
Pages: 253