Section 4.5. Transparent Data Encryption in Oracle Database 10g Release 2
4.5. Transparent Data Encryption in Oracle Database 10g Release 2When you store both the encryption key and the encrypted data in the database, another potential security hole opens upif the disks containing the entire database are stolen, the data becomes immediately vulnerable. One way around this problem is to encrypt all the data elements and store the keys separately on a different location away from the disk drives where the data resides. If your database is completely isolated, you may not feel that you need to encrypt its data. However, you may still want to protect the data in case of a disk theft. One solution would be to create a view to show the decrypted value. In this case, if the key is stored elsewhere, a physical disk theft will not make the data vulnerable. This approach works, but it requires an extensive and elaborate setup. To address these types of situations, Oracle has introduced a new feature known as Transparent Data Encryption (TDE ), available starting with Oracle Database 10g Release 2. TDE uses a combination of two keysone master key stored outside the database in a wallet and one key for each table. The same key is used for all rows in a table, and a unique key is generated for each table (as illustrated in Figure 4-7). Figure 4-7. The Transparent Data Encryption model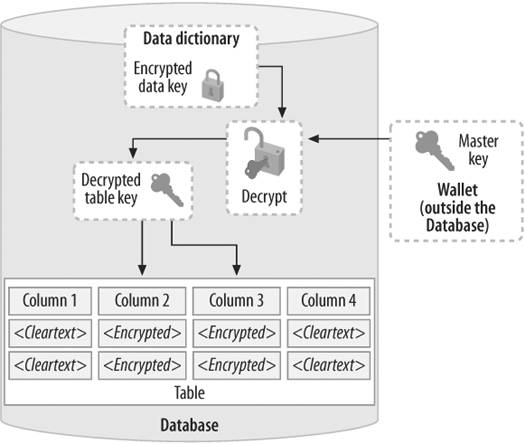 With TDE, you may define a subset of columns as encrypted. For example, if a table has four columns, as shown in the figure, and columns 2 and 3 are encrypted, Oracle will generate a key and use it to encrypt those columns. On the disk, columns 1 and 4 will be stored as cleartext, and the other two as encrypted text. When a user selects encrypted columns, Oracle transparently retrieves the key from the wallet, decrypts the columns, and shows them to the user. If the data on the disk is stolen, it cannot be retrieved without the keys, which reside in the wallet encrypted by the master key, which is not stored as cleartext itself. The result is that the thief can't decrypt the data, even if he steals the disks or copies the files.
To take advantage of TDE, add an ENCRYPT clause (available in Oracle Database 10g Release 2 only) to your table creation statement for each column to be encrypted: /* File on web: cr_accounts.sql */ CREATE TABLE accounts ( acc_no number not null, first_name varchar2(30) not null, last_name varchar2(30) not null, SSN varchar2(9) ENCRYPT USING 'AES128', acc_type varchar2(1) not null, folio_id number ENCRYPT USING 'AES128', sub_acc_type varchar2(30), acc_open_dt date not null, acc_mod_dt date, acc_mgr_id number );Here I have decided to encrypt the columns SSN and FOLIO_ID using AES 128-bit encryption. The ENCRYPT USING clause in the column definition instructs Oracle to intercept the cleartext values, encrypt them, and then store the encrypted format. When a user selects from the table, the column value is transparently decrypted.
4.5.1. Setting Up TDEBefore you start using TDE, you have to set up the wallet where the master key is stored and secure it. Here is a step-by-step approach to wallet management.
4.5.2. Adding TDE to Existing TablesIn the example in the previous section, you saw how to use TDE while creating a new table. You can encrypt a column of an existing table, as well. To encrypt the column SSN of the table ACCOUNTS, specify: ALTER TABLE accounts MODIFY (ssn ENCRYPT); This operation does two things:
The encryption is then performed inside the database. By default, the AES (with 192-bit key) algorithm is used for the encryption. You can choose a different algorithm by specifying it in the command. For instance, to choose 128-bit AES encryption, you would specify: ALTER TABLE accounts MODIFY (ssn ENCRYPT USING 'AES128'); You can choose AES128, AES256, or 3DES168 (168-bit Triple DES algorithm) as parameters. After encrypting a column, let's look at the table: SQL> DESC accounts Name Null? Type --------- ----- ------------ ACC_NO NUMBER ACC_NAME VARCHAR2(30) SSN VARCHAR2(9) ENCRYPT Note the clause ENCRYPT after the datatype. To find the encrypted columns in the database, search the new data dictionary view DBA_ENCRYPTED_COLUMNS. What about the performance impact of TDE? There is no overhead when working with non-encrypted columns. You can expect to see a small amount of overhead when accessing encrypted columns. If encryption is no longer required, you can turn it off for that column by specifying: ALTER TABLE account MODIFY (ssn DECRYPT); 4.5.3. Performing TDE Key and Password ManagementWhat if someone discovers your TDE keys somehow? You can simply re-create the encrypted values by issuing a simple command. While you are at it, you may also want to choose a different encryption algorithm such as AES256. You can do both by issuing: ALTER TABLE accounts REKEY USING 'aes256'; If someone discovers the wallet password, you can change it using a graphical tool called Oracle Wallet Manager. From the command line, type owm, which brings up the tool as shown in Figure 4-8. From the top menu, choose Wallet Figure 4-8. Oracle Wallet Manager 4.5.4. Adding SaltEncryption is all about hiding data, and sometimes encrypted data is easier to guess if there is repetition in the cleartext. For example, a table that contains salary information is quite likely to contain repeated values, and, in that case, the encrypted values will also be the same. Even if an intruder can't decrypt the actual values, she will be able to tell which entries have the same salary, and this information may be valuable. To prevent such a thing from happening, salt is added to the data, which makes the encrypted value different even if the input data is the same. TDE, by default, applies salt. In some cases, patterns of data may improve your database performance, and adding salt may degrade it. With certain indexes, for example, a pattern may establish the b-tree structure and make the searching of LIKE predicates faster, as in the following query: SELECT ... FROM accounts WHERE ssn LIKE '123%'; In this case, b-tree indexes will have to travel along only one branch to get the data, because all account numbers start with the digits 123. If salt is added, the actual values will be stored all over the b-tree structure, making index scans more expensive, and the optimizer will most likely choose a full table scan. In such cases, you will have to remove the salt from the indexed columns. You can do so by specifying: ALTER TABLE accounts MODIFY (ssn ENCRYPT NO SALT); Removing the salt does not significantly affect the security, so the risk of vulnerability probably does not outweigh the performance benefits of indexing.
|

 Open and choose the wallet location you have specified. You will have to supply the password of the wallet. After that, choose Wallet
Open and choose the wallet location you have specified. You will have to supply the password of the wallet. After that, choose Wallet