Managing Built-in Groups and User Rights
Windows 2000 creates four types of built-in groups: local, domain local, global, and system. Each type of built-in group has a predetermined set of user rights. Everyone assigned to the group automatically possesses those rights.
Built-in Local Groups
Member servers, stand-alone servers, and computers running Windows 2000 Professional have built-in local groups that give rights to perform tasks on a single computer. Table 9-1 shows the built-in local groups.
Table 9-1. Built-in local groups
| Local Group | Description |
|---|---|
| Administrators | Members can perform all administrative tasks on the computer. The built-in Administrator account that's created when the operating system is installed is a member of the group. When a stand-alone server or a computer running Windows 2000 Professional joins a domain, the Domain Admins group is made part of this group. |
| Backup Operators | Members can log on to the computer, back up and restore the computer's data, and shut down the computer. Members cannot change security settings. There are no default members in the group. |
| Guests | Members can perform only tasks for which an administrator has granted rights. Members can use only those resources for which an administrator has specifically granted permission. |
| Power Users | Members can create and modify user accounts and install programs on the local computer but cannot view other users' files. |
| Replicator | Do not add user accounts of actual users to this group. If necessary, you can add a "dummy" user account to this group to permit you to log on to Replicator services on a domain controller to manage replication of files and directories. |
| Users | Members of this group can log on to the computer, access the network, save documents, and shut down the computer. Members cannot install programs or make system changes. When a member server or Windows 2000 Professional machine joins a domain, the Domain Users group is added to this group. |

TIP
If you don't want members of the Domain Users group to have access to a particular workstation or member server, remove Domain Users from that computer's local Users group. Similarly, if you don't want the members of Domain Admins to administer a particular workstation or member server, remove Domain Admins from the local Administrators group.
Built-in Domain Local Groups
The Windows 2000 built-in domain local groups provide users with rights and permissions to perform tasks on domain controllers and in Active Directory. The domain local groups have predefined rights and permissions that are granted to users and global groups that you add as members. Table 9-2 shows the most commonly used of the built-in domain local groups.
Table 9-2. Commonly used built-in domain local groups
| Domain Local Group | Description |
|---|---|
| Account Operators | Members can create, delete, and manage user accounts and groups. Members cannot modify the Administrators group or any of the Operators groups. |
| Administrators | Members are automatically granted every right and permission on all domain controllers and the domain itself. The Administrator account, Enterprise Admins group, and Domain Admins group are members. |
| Backup Operators | Members can back up and restore data on all domain controllers using Windows 2000 Backup. |
| Guests | Members can perform only tasks for which an administrator has granted rights. Members can use only those resources for which an administrator has specifically granted permission. The Guest User and Domain Guests groups are members by default. |
| Print Operators | Members can manage all aspects of printer operation and configuration in the domain. |
| Server Operators | Members can perform most administrative tasks on domain controllers, except the manipulation of security options. |
| Users | Members can log on to the computer, access the network, save documents, and shut down the computer. Members cannot install programs or make system changes. The Domain Users group is a member by default. |
![]()
REAL WORLD Just Who Is Everyone?
In Windows NT, all domain users are members of the Everyone group. This group is controlled by the operating system and appears on any network with Windows NT servers. In Windows 2000, the equivalent group is called Authenticated Users. Unlike Everyone, Authenticated Users contains no anonymous users or guests. The Everyone group survives as a special identity. You don't see it when you administer groups, and it cannot be placed in a group. When a user logs on to the network, the user is automatically added to Everyone. You can't see or change the membership of the special identities, which also include the Network and Interactive groups.
Built-in Global Groups
Built-in global groups are created to encompass common types of accounts. By default, these groups do not have inherent rights; an administrator must assign all rights to the group. However, some members are added to these groups automatically, and you can add more members based on the rights and permissions you assign to the groups. Rights can be assigned directly to the groups or by adding the built-in global groups to domain local groups. Table 9-3 describes the built-in global groups that are commonly used.
Table 9-3. Commonly used built-in global groups
| Global Group | Description |
|---|---|
| Domain Admins | This group is automatically a member of the domain local Administrators group, so members of Domain Admins can perform administrative tasks on any computer in the domain. The Administrator account is a member of this group by default. |
| Domain Computers | All controllers and workstations in the domain are members. |
| Domain Controllers | All domain controllers in the domain are members. |
| Domain Guests | The Guest account is a member by default. This group is automatically a member of the domain local Guests group. |
| Domain Users | All domain users and the Administrator account are members. The Domain Users group is automatically a member of the domain local Users group. |
| Enterprise Admins | This group is for users who are to have administrative rights for the entire network. Enterprise Admins is automatically a member of the domain local Administrators group in the domain in which it is created. You will need to add it to the domain local Administrators group for other domains. |
| Group Policy Admins | Members can create and modify group policy for the domain. |

TIP
If you have users who should have fewer rights and/or permissions than the typical user, add these users to Domain Guests and remove them from Domain Users.
Defining User Rights
What users can and cannot do depends on the rights and permissions that have been granted to them. Rights generally apply to the system as a whole. The ability to back up files or to log on to a server, for example, is a right that the administrator giveth or taketh away. Rights can be assigned individually, but most often they are characteristics of groups, and a user is assigned to a particular group on the basis of the rights that the user needs.
Permissions indicate the access that a user (or group) has to specific objects such as files, directories, and printers. For example, the question of whether a user can read a particular directory or access a network printer is a permission. Permissions are discussed at length later in this chapter.
Rights, in turn, are divided into two types: privileges and logon rights. Privileges include such things as the ability to run security audits or force shutdown from a remote system—obviously not things that are done by most users. Logon rights are self-explanatory; they involve the ability to connect to a computer in specific ways. Rights are automatically assigned to the built-in groups in Windows 2000, although they can be assigned to individual users as well as groups. Assignment by group is preferred, so whenever possible, you should assign rights by group membership to keep administration simple. When membership in groups defines rights, rights can be removed from a user by simply removing the user from the group. Tables 9-4 and 9-5 list the logon rights and privileges and the groups to which they are assigned by default.
Table 9-4. Logon rights assigned to groups by default
| Name | Description | Groups Assigned the Right by Default |
|---|---|---|
| Access this computer from the network | Permits connection to the computer through the network. | Administrators, Power Users, Everyone |
| Logon as a batch job | Allows logging on using a batch-queue. | Administrators |
| Logon as a service | Allows logging on as a service using a specific user account and security context. | None |
| Logon locally | Permits logon at the computer's keyboard. | Administrators, Account Operators, Backup Operators, Print Operators, Server Operators |
Table 9-5. Privileges assigned to groups by default
| Privilege | Description | Groups Assigned the Privilege by Default |
|---|---|---|
| Act as part of the operating system | Allows a process to authenticate as any user. A process that requires this privilege should use the LocalSystem account, which already includes this privilege. | None |
| Add workstations to domain | Allows a user to add new workstations to an existing domain. | Administrators |
| Backup files and directories | Allows backing up the system; overrides specific file and folder permissions. | Administrators, Backup Operators |
| Bypass traverse checking | Allows a user to go through directory trees (folder structures) even if the user doesn't have permission to access the directories being passed through. | Everyone |
| Change the system time | Allows the setting of the computer's internal clock | Administrators, Power Users |
| Create a pagefile | Allows the creation and modification of a pagefile. | Administrators |
| Create a token object | Allows a process to create a token that can be used to access any local resource. A process that requires this privilege should use the LocalSystem account, which already includes this privilege. | None |
| Create permanent shared objects | Allows a process to create a directory object. Used by kernel-mode components to extend the Windows 2000 object namespace. Components running in kernel mode already have this privilege. | None |
| Debug programs | Allows the user to attach a debugger to a process. | Administrators |
| Enable computer and user accounts to be trusted for delegation | Permits user to set the Trusted for Delegation setting on an object. | Administrators |
| Force shutdown from a remote system | Allows the shutdown of a computer from a remote location on the network. | Administrators |
| Generate security audits | Allows a process to make entries in a security log. | None |
| Increase quotas | Allows a process with write property access to another process to increase the processor quota assigned to that process. | None |
| Increase scheduling | Allows the use of Task Manager to change the priority scheduling priority of a process. | Administrators, Power Users |
| Load and unload device drivers | Install and remove device drivers. | Administrators |
| Lock pages in memory | Allows a process to keep data in physical memory. This is an obsolete privilege that can have a seriously negative effect on system performance. Do not use it. | None |
| Manage auditing and security log | Allows a user to specify auditing options and to view and clear the security log in Event Viewer. Audit Directory Service Access must be turned on for object access auditing to be performed. (See Chapter 10.) Administrators can always view and clear the security log. | Administrators |
| Modify firmware environment variables | Allows the configuration of nonvolatile RAM on computers that support such function. | Administrators |
| Profile a single process | Allows performance sampling on a process. | Administrators, Power Users |
| Profile system performance | Allows performance sampling of the system. | Administrators |
| Remove computer from docking station | Allows the removal of a laptop from a docking station using the Windows 2000 interface. | Administrators, Users |
| Replace a process level token | Allows the replacement of the default token associated with a subprocess. | None |
| Restore files and directories | Allows restoring files and folders to a system; overrules specific file and folder permissions. | Administrators, Backup Operators |
| Shut down the system | Shuts down Windows 2000. | Administrators, Backup Operators, Everyone, Power Users, Users |
| Synchronize directory service data | Allows a user to initiate a synchronization of Active Directory. | Administrators |
| Take ownership of files or other objects | Allows a user to take ownership of any security object including files and folders, printers, registry keys, and processes. Overrules specified permissions. | Administrators |
Assigning User Rights to a Group
Rights are assigned and removed most easily at a domain level using group policy. Suppose you have a group of users whom you want to allow to log on locally to Windows 2000 Servers, but you don't want them to be members of any of the groups that have this logon right by default. One way to approach this situation would be to create a group called Logon Rights, add the users to the group, and assign the right to logon locally to the Logon Rights group. To assign a right to a particular group, follow these steps:
- Open Active Directory Users and Computers from the Administrative Tools menu. Right-click the domain name and select Properties.
- Click the Group Policy tab and then click the Edit button. Open Computer Configuration, and then open Windows Settings. Under Security Settings, click Local and then User Rights Assignment (Figure 9-4).
- In the details pane, double-click Log On Locally.
- Place a check mark next to Define These Policy Settings and then click Add.
- Enter the name of the group to be granted this right (or click Browse to search for the group). Click OK twice and close Domain Security Policy.
Figure 9-4. User rights listed under group policy.
The same process can remove rights, except that you'd click Remove in step 4. Rights can also be assigned to an individual user using this method.
Assigning Rights Locally
Rights can be assigned or removed locally, though you must bear in mind that a defined domain-level policy will override a local policy setting. To assign a policy locally, follow these steps:
- Open Local Security Policy from the Administrative Tools menu.
- Under Security Settings, click Local Settings and then User Rights Assignment (Figure 9-5). As you can see, the local setting is shown in addition to the effective setting. (Effective policy is the policy in effect after domain policy settings are applied.)
- In the detail pane, double-click the policy you want to assign to open the Local Security Policy Setting dialog box.
- Click Add to select a group (or individual) in the Select Users Or Groups dialog box. Highlight the group, click Add, and then click OK.
Figure 9-5. Local policy settings.
As you can see in Figure 9-6, the policy setting Deny Logon Locally has been assigned to the Graphic Artists group. The policy is shown as local only—that is, there is no domain policy in effect. The net result is that members of the Graphic Artists group will not be able to log on to this local computer. Their ability to log on or not log on to other computers in the domain is neither specified nor affected.
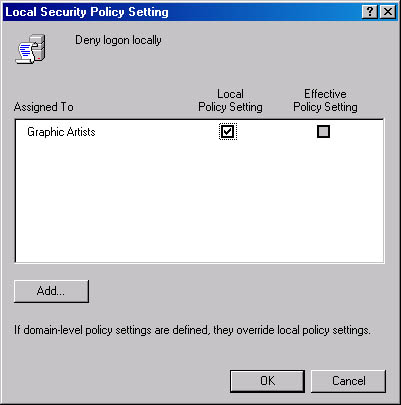
Figure 9-6. Defining the local policy that denies local logon.
Figure 9-7 shows another local policy window. In this case, the right to Enable Computer And User Accounts To Be Trusted For Delegation is assigned to Domain Admins through a domain-level policy. A domain-level policy applies whether the local policy is defined or not. Group Policy is covered in more detail later in this chapter.
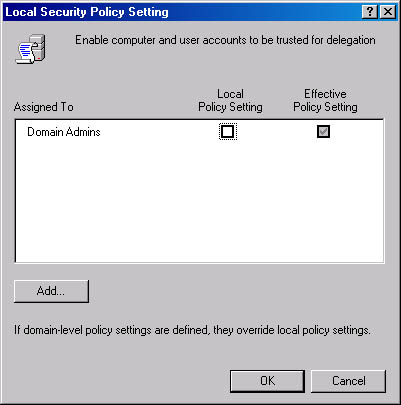
Figure 9-7. Domain-level policy as the effective policy.
EAN: 2147483647
Pages: 366