Breaking the Code
Saul left the hospital by the front entrance and walked over to sit down at a fountain. With the new information Saul had about the wireless network at the hospital, he knew he could at least start working on getting access to the management console of the access points. He knew he could locate the APs quickly by associating with the wireless network and running a port scan on the network. Nmap was free and worked well in situations like these, even though it tended to misidentify AP-1000 access points as an Apple Airport Base Station. He already knew they were Lucent; all he needed to know now was the actual wired IP address of the APs.
The real problem would come when he tried to log in to the management console of the access points once he did have the IP addresses. He knew the default username and password for the Lucent AP-1000 series was normally admin and public , respectively. But what were the chances that the hospital had not changed the passwords? Of course he would try those, but he could not believe that they would be left at their defaults.
He knew that his only other option would be to sniff the traffic on the network long enough and hope that he could pick up the appropriate username and password. I need to ensure that the administrators try to log in to one of the access points so I can get the password quicker, Saul thought to himself. If I can get someone to call in a problem to one of the access points, maybe the administrators will have to log in and find out what the problem is.
Saul thought about his options for a few minutes and then grabbed the apple from his backpack to snack . The day was definitely getting warmer as he sat on the edge of the fountain. Suddenly it occurred to Saul that the best way to cause a problem without actually breaking something or compromising his work was to use software to disassociate any clients from the access point in the area.
He knew that it was easy enough to spoof the MAC address of other clients and that by doing so he could disassociate the legitimate clients from the wireless network. His laptop was already loaded with software that could continuously scan wireless networks for association and data packets from wireless clients. A database is created that contains all of the client MAC addresses and continuously disassociates those clients from their connection on the access point. This would create a temporary denial of wireless service in the area. If Saul did this a few times for just a couple of minutes each, the administrators would have to check out the problem. He hoped this would work.
Saul pulled out his laptop and booted into Linux. First, he needed to run Nmap against the wireless network. This would require him to connect fully to the network by associating with a wireless access point. Since he already had the WEP key from his earlier scans , he configured his PCMCIA wireless card for the hospital s network and set himself up to receive DHCP information.
The connection took only seconds and Saul found himself with a working IP address on the wireless network. Saul ran the command nmap -v -sS -O 192.168.1.0/24 on his laptop and waited for the results. Hopefully the stealth mode option would help him stay undetected.
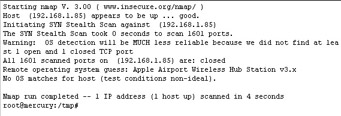
Nmap Scan of the AP-1000
Saul was able to find five access points using Nmap. He wrote the IP addresses down on a scrap piece of paper he had in his backpack and brought up a tool based on a wireless toolkit, called Radiate, that would disrupt the wireless network. Just a few minutes at a time, Saul thought to himself. That s all I need. Once the administrators get a few complaints, they ll be forced to check out the problem.
Before he disrupted the network, though, he knew he should try some basic brute force activities just to see if security was really that lax at the hospital. Trying the defaults wasn t working for Saul on any of the access points he had discovered so he began trying common sense words instead. Brute forcing isn t glamorous and Saul knew he could be at this all day with no success, so after just a few attempts, he decided to go with his plan and disrupt the wireless network.
Running the program was easy. It was run from a normal root user shell prompt under a Linux kernel. The only real stipulation was that the laptop be within a reasonable distance of the access point. He watched the output to the screen intently as multiple IP addresses on the wireless network were being displayed as spoofed and disassociated. The information on the screen was more for gauging the progress of the program. Since the program dumped this same information to a text file, Saul knew he could review it later.
Saul let the program run for only a few minutes and then shut it down. After giving the users about five minutes of time to use the network, he ran the program again and watched the screen as those users were once again denied access to their network. He ran this same routine a couple of more times before closing out his prompt and opening up a network analyzer window.
Ethereal is a cross-platform network analyzer. The network analyzer would sniff packets off the network and store them in a file for review. Saul could also watch the packets as they were collected in real time. He knew he needed that username and password in order to get into the access points at a later time.
With the sniffer running, Saul didn t have to wait long until he saw an attempt to log in to one of the access points. The username and password pair wasn t the default for an AP-1000, but it wasn t too hard. Someone logged in to the access point at 192.168.1.85 using the username sysadmin and the password st.james . The connection didn t last long, but knowing that he shouldn t try to access the management console today, Saul decided to pack up and go home for the day.
Along with the wireless information he had collected about the network, Saul had discovered several different IP addresses on the network that appeared to have database ports running. Any of these could have been the patient database, but they also could have been an inventory database for the cafeteria inside the hospital. He knew he would have to check out each individual database to see what information they contained. But that could wait until later, when he was looking for usernames and passwords.
EAN: N/A
Pages: 105
- Step 1.1 Install OpenSSH to Replace the Remote Access Protocols with Encrypted Versions
- Step 1.2 Install SSH Windows Clients to Access Remote Machines Securely
- Step 3.1 Use PuTTY as a Graphical Replacement for telnet and rlogin
- Step 3.4 Use PuTTYs Tools to Transfer Files from the Windows Command Line
- Step 6.3 X11 Forwarding