Controlling User Access to IMAP and POP
Controlling User Access to IMAP and POP
As with Outlook Web Access, there are three primary methods of choosing who can use your IMAP and POP servers: controlling which Internet Protocol (IP) addresses are allowed to connect, specifying which authentication methods the server supports, and identifying which users are allowed to use the specified protocols.
Choosing an Authentication Method
Exchange s IMAP and POP servers support two authentication methods: basic authentication and the Simple Authentication and Security Layer (SASL, first described in Chapter 2, Security Protocols and Algorithms ). This is a change from Microsoft Exchange 2000 Server, which allowed the use of integrated Windows authentication with POP3 and IMAP4. You can set these methods in the Access tab of the virtual server (VS) Properties dialog box. Simply click Authentication and you ll open the dialog box shown in Figure 15-1. Choose the authentication method you want to use; remember that if you enable basic authentication without requiring Secure Sockets Layer/Transport Layer Security (SSL/TLS), anyone who can gain access to your network or the network the client is using can easily sniff the username and password that the client supplies .
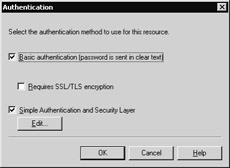
Figure 15-1: You can enable basic or SASL-based authentication separately for each POP or IMAP virtual server.
If you choose to enable SASL, clicking Edit in the Authentication dialog box displays the Acceptable SASL Mechanisms dialog box (see Figure 15-2). This dialog box lets you specify which SASL authentication methods your server will accept. Although at present Exchange Server 2003 only supports NTLM, in the future Microsoft or third parties might add more SASL methods, which is what this dialog box is intended to expose.
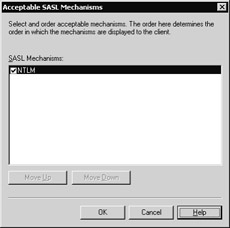
Figure 15-2: You can specify which SASL mechanisms can be used and how they re ordered.
Controlling Access by IP Address
You can control the connection behavior of the virtual servers in a couple of different ways. First, you can use the controls in the General tab of the VS Properties dialog box to control what IP address and port it listens on. For example, you could configure the POP and IMAP services on a front-end server so that they don t accept requests from clients on the internal local area network (LAN). You might also choose to restrict POP and IMAP access to users with a demonstrated business need; after all, Outlook Web Access works very well for most users, and for organizations that have deployed Microsoft Office Outlook 2003; remote procedure call (RPC) over Hypertext Transfer Protocol (HTTP) is a terrific solution from both performance and security standpoints. In fact, Microsoft and many other large companies leave IMAP and POP turned off.
Second, you can use Connection on the Access tab of the VS Properties dialog box to restrict connections by specifying individual IP addresses, IP ranges, or Domain Name System (DNS) domain names . You can apply restrictions that allow only the listed computers to connect or that allow any machine other than those listed to connect. Either way, the virtual server refuses connection requests according to the list you provide.
Regulating Who Can Use the Protocol Server
You might want to control or restrict which users can use POP or IMAP on your servers. There are four ways you can do this, all of which are fairly straightforward. Each method provides a different degree of selectivity. From the most specific to the least specific, your options are as follows :
-
Enable or disable IMAP or POP access for an individual user You can use Active Directory Users and Computers to modify individual users protocol settings. In Chapter 14, Securing Outlook Web Access, we examined how to do this for HTTP access. The process is the same for IMAP and POP: open the user s Properties dialog box, click the Exchange Advanced tab, and click Protocol Settings. In the resulting Protocols dialog box, select the protocol of interest and click Settings. You can then use the Enable For Mailbox check box to control whether the protocol is active for that mailbox or not.
-
Enable or disable IMAP or POP for a group of users To do this, you ll need to stamp a value into the protocolSettings attribute of each affected user s account properties in Active Directory. Microsoft Knowledge Base article 252459 contains some sample code that explains ( sort of) the format of this attribute; it s a string value where the name of the protocol ( HTTP , IMAP4 , POP3 , and NNTP are legal values) is followed by the § character and either 0 (meaning the protocol is disabled) or 1 (meaning that it is enabled). You can optionally append more § characters and more options, including message format specifiers that control the default character set and message format. (There s a script in Chapter 16 that describes how to enable or disable Outlook Mobile Access and Exchange ActiveSync for individual users; you can use that same script with the protocolSettings attribute, and a properly formed value string to bulk-enable or bulk-disable users.)
-
Turn off IMAP or POP on a particular server You can do this by stopping the default virtual servers: launch Exchange System Manager, open the target server s Protocols container, find the virtual server you want to stop, right-click it, and select Stop from the shortcut menu. This stops the services until the next reboot; if you want them turned off permanently, use the Services Control Panel icon to disable the Microsoft Exchange IMAP4 and Microsoft Exchange POP3 services. Actually, the IMAP4 and POP3 services are implemented as dynamic-link libraries (DLLs) that run within IIS, but for ease of management they show up as though they were stand-alone services. Remember, it s always a good idea to reduce the attack surface of your servers as much as possible by turning off unnecessary services.
Tip The easiest way to generate the value of the protocolSettings attribute is to use the process just described to modify one user s protocol settings to match your requirements. Once you ve done that, you can use the ADSIEdit snap-in to inspect the value of protocolSettings to make sure that you get the value right in your script.
-
Block the selected protocols at the network boundary IMAP uses Transmission Control Protocol (TCP) port 143 for normal traffic and port 995 for Secure Sockets Layer (SSL) + IMAP; POP uses ports 110 and 993. If you block these ports, you ll shut off inbound traffic, denying your clients the ability to use the selected protocols from the outside world. Microsoft does this on its network in conjunction with not running the services in the first place. Of course, you can always create an additional POP or IMAP virtual server and assign it a nonstandard port number. This provides a small degree of security through obscurity, but it s a hassle for your clients and likely isn t worth the effort.
EAN: 2147483647
Pages: 189