12.5 Applying WISDOM to WLAN Security
12.5 Applying WISDOM to WLAN Security
WISDOM, as proposed by James F. Ransome in his doctoral dissertation [1], provides three tiered security options with proper hardware, software, and security requirements to secure a WLAN at a corresponding security level equivalent to the wired network with which it connects. There is a significant need for a comprehensive taxonomic network security model, integrating wired and wireless, addressing the characteristics and security requirements of these converged technologies, both individually and collaboratively. The three security levels of WISDOM ”basic, intermediate, and advanced ”are presented in the following sections.
12.5.1 WISDOM Basic Security Measures
WISDOM Basic Security is defined as the minimum security requirements for WLANs attached to a converged network. WISDOM Basic Security also requires that the WLAN security management considerations described earlier be implemented as part of its layered approach. Key design features and components for WISDOM Basic Security are as follows :
-
Wireless client adapter and software. Provides the hardware and software necessary for wireless communications to the AP
-
Wireless AP. Provides initial IP protocol filtering between the WLAN and wired network
The 20 WISDOM Basic Security vulnerability, threat, and mitigation elements are described in Table 12.1. The WISDOM Basic Security topology is shown in Figure 12.1.
| Vulnerability | Threat | Mitigation |
|---|---|---|
| AP Secure Set Identifier (SSID) broadcast. This is the name of the wireless network. Although a unique name is not required, most system administrators will want to change the SSID from the default name that comes installed on the AP. In order for the AP to communicate with the station, both station and AP must have matching SSIDs. | The broadcast of the SSID to the world from the AP can be used by a hacker as a first step in gaining the information required to exploit a WLAN. If a WLAN is not configured to operate as a closed system, it will respond to clients with the "Any" SSID assigned or broadcast the SSID to the clients at large, resulting in an unacceptable exploitation risk. Although an equipped adversary can capture the SSID identity parameter over the wireless interface, it should be changed to prevent unsophisticated adversary attempts to connect to the wireless network. | Change AP SSID factory default, set as a "closed" system. A closed system is one that does not respond to clients with the "Any" SSID assigned, nor does it broadcast the SSID to the clients at large. Instead, as the client scans for APs in a range with which to associate, it expects the correct management frame containing the SSID that matches its own configuration. |
| AP default setting of "no encryption." You should always use 802.11b's built-in WEP encryption. Only a determined hacker with the proper equipment and software will be able to crack the key. | An AP default setting of "no encryption" will result in data transmitted in the clear, which will increase the ease of monitoring and/or compromise. As a result, any person with a laptop, PC card, and range-extended antenna may be able to see and access the WLAN. | Change the AP encryption setting from 40-bit to 128-bit encryption. Encryption settings should be set for the strongest encryption available in the product, depending on the security policy of the organization. Typically, APs have only a few encryption settings available: none, 40-bit shared key, and 128-bit shared key (with 128-bit being the strongest). Encryption as used in WEP, simple stream cipher generation, and exclusive-OR processing does not pose an additional burden on the computer processors performing the function. Although encryption with the largest cryptographic key space is normally recommended because of its greater effectiveness, this is not true for 802.11 WEP because of poor cryptographic design using IVs and a flawed algorithm; however, high encryption levels are recommended nonetheless. |
| AP shared key authentication. Shared key authentication supports authentication of station devices accessing the network as either a member of those who know a shared secret key or a member of those who do not. Shared key authentication accomplishes this with the use of the WEP privacy mechanism. Therefore, this authentication scheme is only available if the WEP option is implemented. | Shared key authentication presents greater risk because many vendors use default shared keys that could be exploited by unauthorized devices to gain unauthorized access to the network. When using shared key authentication, make sure that the keys are unique. | Ensure that shared key authentication is not enabled. Use other alternatives to authentication, such as username and password, instead of shared key. |
| AP Ethernet MAC access control lists (ACLs). While an AP or group of APs can be identified by an SSID, a client computer can be identified by the unique MAC address of its 802.11 network card. The MAC address is the physical address of the radio in the AP. You can find this label attached to the device. | MAC addresses can be spoofed because they are passed as cleartext from a wireless NIC to an AP and can be easily captured. This can result in unauthorized access to the WLAN. Malicious users can spoof a MAC address by changing the actual MAC address on their computers to a MAC address that has access to the wireless network. A MAC address is a hardware address that uniquely identifies each computer (or attached device) on a network. Networks use the MAC address to help regulate communications between different computer NICs on the same network subnet. Many 802.11 product vendors provide capabilities for restricting access to the WLAN based on MAC ACLs that are stored and distributed across many APs. The MAC ACL grants or denies access to a computer using a list of permissions designated by each specific MAC address; however, the Ethernet MAC ACL does not represent a strong defense mechanism by itself. | Ensure limitation or nonuse of MAC ACLs for authentication to the WLAN. To increase the security of an 802.11 network, each AP can be programmed with a list of MAC addresses associated with the client computers allowed to access the AP. If a client's MAC is not in this list, the client will not be allowed to associate with the AP. |
| AP ad hoc mode. Ad hoc mode is used when you are setting up a wireless NIC solely for the purpose of communicating with other wireless NICs in a peer-to-peer fashion. When two stations are close enough together to communicate and their network adapters are set to ad hoc mode, the stations form a basic service set (BSS). | Wireless devices can run in either "infrastructure" or "ad hoc" mode. Ad hoc, or peer-to-peer, networks use a different mode in the wireless NIC to permit wireless clients to communicate directly with each other, rather than communicating through a wireless hub. Ad hoc networks carry significant potential dangers because they are a system of interconnected computers that exist beyond the security control of the WLAN. Peer-to-peer ad hoc network connections between devices with WLAN cards do not require an access point or any form of authentication from other stations with which it connects. Although ad hoc networks can be a convenient feature for users to transfer files between stations or connect to shared network printers, they present an inherent security risk where a station in ad hoc mode opens itself to a direct attack from a hacker who can download files from the victim's station or use the authorized station as a conduit to the entire network. A wired-side network monitor is not capable of detecting these risky networks because they never touch the wired network. | Ensure that ad hoc mode has been disabled. This will mitigate the possibility of computers connected to the WLAN that are beyond its security control. |
| AP user password. | Login to the AP by unauthorized users is possible if no password is required. Although you must use the default password when you first open the configuration pages of the AP, immediately change the password to avoid a security breach because a default password is generally known or readily available. | Implement strong AP user passwords with both alphanumeric and special characters and a minimum password length of eight characters . In addition, password expirations should be set at 30 days. |
| AP placement. Some APs and associated software come with basic tools to optimize placement of APs; however, with multiple APs in large areas, this process becomes rather difficult. It is important to keep the range of the AP within the physical boundaries of the complex that the WLAN is housed in to mitigate the risk of unauthorized interception of signals. | APs incorrectly placed inside buildings can be susceptible to interception by unauthorized users. It is important to consider the range of the AP when deciding where to place an AP in a WLAN environment. If the range extends beyond the physical boundaries of the office building walls, the extension creates a security vulnerability. An individual outside of the building, perhaps someone "war-driving," could eavesdrop on network communications by using a wireless device that picks up the RF emanations . | Use a site survey tool to measure the range of AP devices, both inside and outside of the building where the wireless network is located, to ensure that coverage does not extend beyond the intended coverage area. Site survey tools that can be used to measure and secure AP coverage are commercially available. The tools, which some vendors include with their products, measure the received signal strength from the APs. These measurements can be used to map out the coverage area and are especially useful for identifying and controlling the coverage range inside a building or room to help prevent the wireless signals from extending beyond the intended coverage area. Organizations could additionally use directional antennas to control emanations. |
| AP administrative password. The default AP administrative password is generally known and/or readily available; hence, it is inherently insecure . | Login to an AP by an unauthorized user is possible if no password is required or the default password is not changed. This can lead to unauthorized access to and/ or control of the AP. On some APs, the factory default configuration does not require a password (i.e., the password field is blank). Unauthorized users can easily gain access to the device if there is no password protection. | Implement strong AP administrative passwords. Ensure that a strong (i.e., an alphanumeric and special character string at least eight characters in length) administrative password is used on all AP administrative passwords. Also, change the passwords on a regular basis, preferably every 30 days. |
| AP reset function. This function returns the AP settings to their default settings. This function will also cancel out existing security functions on an AP. | The reset function allows an individual to negate any security settings administrators have configured in the AP by returning the AP to its default factory settings. An individual can reset the configuration to the default settings simply by inserting a pointed object (such as a pen) into the reset hole and pressing it. If a malicious user gains physical access to the device, that individual can exploit the reset feature and cancel out any security settings on the device. The default settings generally do not require an administrative password, for example, and may disable encryption. The reset function, if configured to erase basic operational information such as IP address or keys, can further result in a network DoS, because APs may not operate without these settings. | Ensure that the required security settings (i.e., "encryption enabled") are in place and haven't been negated by inadvertent or intentional use of the reset function. Having physical access controls in place to prevent unauthorized users from resetting APs can mitigate the threats. |
| AP default shared key. Many vendors use identical shared keys in their factory settings. This default setting is easily exploited. | Using a default shared key setting is a security vulnerability because many vendors use identical shared keys in their factory settings. The manufacturer may provide one or more keys to enable shared key authentication between the device trying to gain access to the network and the AP. A malicious user may know the default shared key and use it to gain access to the network. | Change the default shared key setting to another key to mitigate the risk. For example, the shared key could be changed to "456812" instead of using a factory default shared key of "111111." No matter what their security level, organizations should change the shared key from the default setting because it is easily exploited. |
| AP channel cross-over. Interference can dramatically affect the performance of any WLAN. In general, interference is either caused by radio devices operating in the same bands or by thermal noise, or both. For a single AP, thermal noise is the only source of interference. With multiple cells , however, there is interference from adjacent channels and cochannels. The overall impact of this interference depends on the number of available frequency channels and cell deployment. | Vendors commonly use default channels in their APs. When implementing an AP, it is possible that a different wireless network AP that is using a channel within five channels of the new AP could cause DoS attacks from radio interference. If two or more APs are located near each other, but are on different networks, a DoS can also result from radio interference between the two APs. DoS attacks can result in degradation or loss of service. | Ensure that the AP channel is configured for at least five channels difference from all other nearby APs on different networks. If a nearby AP(s) is using the same channel or a channel within five channels of itself, then choose a channel that is in a different range. |
| Encryption key length. The RC4 algorithm and its implementation by the WEP protocol have weaknesses that can be exploited. There are two weaknesses in the algorithm: (1) it contains a large number of inherently weak keys, and (2) part of the key can be exposed to an attacker if he or she can observe enough encrypted traffic. | 40-bit encryption algorithms are trivial to crack, which can lead to the compromise of data transited over the WLAN; however, 40-bit encryption is better than none. The 40-bit algorithm that is part of WEP is particularly vulnerable to attack because of its inherent design flaws. | When possible, enable 128-bit encryption or higher. The key sizes advertised by the manufacturers of WLAN equipment can be confusing; many vendors advertise 64-and 128-bit WEP support, but actual key space is limited to 40 and 104 bits because the IV uses up 24 bits of the advertised space in original WEP implementations . |
| WLAN eavesdropping. Eavesdropping is when the attacker simply monitors transmissions for message content. An example of this attack is a person listening into the transmissions on a LAN between two workstations or tuning into transmissions between a wireless handset and a base station. | Eavesdropping on wireless network communications could come from either inside or outside the network if AP range extends beyond building boundaries (e.g., eavesdropping could occur from such areas as parking lots outside of buildings). Eavesdropping can result in acquisition of information that optimizes someone's ability to gain unauthorized access and/or control of the network. |
|
| Bridge-to-bridge eavesdropping. APs may also provide a "bridging" function. Bridging connects two or more networks together and allows them to communicate to exchange network traffic. Bridging involves either a point-to-point or a multi-point configuration. In a point-to-point architecture, two LANs are connected to each other via the LANs' respective APs. In multi-point bridging, one subnet on a LAN is connected to several other subnets on another LAN via each subnet AP. | Eavesdropping can result in acquisition of information that optimizes an attacker's ability to gain unauthorized access to and/or control of the network. Enterprises may use bridging to connect LANs between different buildings on corporate campuses. Bridging AP devices are typically placed on top of buildings to achieve greater antenna reception . The typical distance over which one AP can be connected wirelessly to another by means of bridging is approximately two miles. This distance can leave a particularly large area in which an adversary can place equipment to intercept unprotected traffic. |
|
| Media Access Control (MAC) spoofing. A common and easy form of an identity theft is to "spoof" the MAC address of an authorized user. An unauthorized user can change the MAC address of his or her station to enter the network as the authorized user. | Absence of MAC filtering can result in unauthorized access and/or control of the network. An unauthorized user can change the MAC address of his or her station to enter the network as the authorized user. MAC spoofing can also be used to defeat wired-side monitors that search for rogue access points by probing the network for unauthorized MAC addresses. An employee can hide rogue access points from these network scanners by changing the MAC address of the access point to the MAC address of an authorized station. The rogue access point attached to the enterprise network can appear as an authorized station. MAC filtering occurs at Layer 2 of the OSI reference model, which means that traffic bound for any address is ultimately attempting to breach Layer 3 in order to gain wider access to network resources. If the filtering is on Layer 2, none of the processing of the extraneous bits is required. Logging of access attempts is also important so that the administrator is alerted to potential attempts to hack the network. | Apply MAC filters. Upon attempting to associate with the AP, the MAC filter will recognize the untrusted MAC and prevent traffic from traversing the AP to the trusted network. The client may still be able to associate to the AP, but the traffic is stopped . |
| Rogue (unauthorized) access points. Because an adversary doesn't require physical access to be attached to a WLAN, it is easier to obtain access through unauthorized devices attached to wireless networks than those that are wired. An otherwise secure WLAN can be made insecure by the attachment of a rogue access point that is beyond the security control of the network. | Rogue (unauthorized) access points connected to the network often lack standard security controls, can bypass otherwise good security controls on a network, and can circumvent an enterprise's security, thus resulting in unauthorized access to and/or control of the network. When an employee or hacker connects a rogue access point to a network, the rogue AP allows just about anyone with an 802.11-equipped device onto the corporate network, very close to mission-critical resources. |
|
| Filtering controls. Care must be taken in setting up the filtering rules, enforcing them properly, and testing their effectiveness. Poorly implemented protocol filters can result in intermittent access, no access, and/or no security. | Simple Network Management Protocol (SNMP), Internet Control Message Protocol (ICMP), and other protocols can be exploited without the proper filtering controls in place. Absence of proper filtering controls can result in unauthorized access and/or control of the network. SNMP has become the de facto standard for Internet work management. Because it is a simple solution, requiring little code to implement, vendors can easily build SNMP agents to their products. SNMP is extensible, allowing vendors to easily add network management functions to their existing products. SNMP also separates the management architecture from the architecture of the hardware devices, which broadens the base of multivendor support. ICMP is an extension to the Internet Protocol (IP) defined by RFC 792. ICMP supports packets containing error, control, and informational messages. The PING command, for example, uses ICMP to test an Internet connection. | Implement AP protocol filtering. Limit all but the most common protocols. Limited protocols include SNMP to limit access device configurations and ICMP to prevent the use of large packets to mount DoS attacks. |
| Security patches/upgrades. All technology, either existing or newly deployed, should have the latest security patches and upgrades installed in a timely manner. The lack of patches and upgrades make the associated technology subject to the same vulnerability that the patch or upgrade was intended to fix or protect against. | Vulnerabilities exist when security patches and upgrades are not kept up to date. The more time their deployment is delayed, the longer the exposure to risk. | Ensure that the latest security patches and upgrades are installed on all of the hardware and software components of the WLAN. |
| SNMP agents. SNMP controls read/write privileges to APs. If an unauthorized user were to gain access, they could write data to the AP, resulting in a data integrity breach. | Some wireless APs use SNMP agents, which allow network management software tools to monitor the status of wireless APs and clients. The default SNMP community string that SNMP agents commonly use is the word "public" with assigned "read" or "read and write" privileges. Using this well-known default string leaves devices vulnerable to attack. If an unauthorized user were to gain access with read/write privileges, that user could write data to the AP, resulting in a data integrity breach. | Change the default SNMP parameter. If SNMP is not required on the network, the organization should disable SNMP altogether. |
| Dynamic Host Control Protocol (DHCP) server. A DHCP server will not necessarily know which wireless devices have access, so the server will automatically assign the laptop a valid IP address. A malicious user could easily gain unauthorized access on the network through the use of a laptop with a wireless NIC. | Automatic network connections involve the use of a DHCP server, and the DHCP server automatically assigns IP addresses to devices that associate with an AP when traversing a subnet. For example, a DHCP server is used to manage a range of TCP/IP addresses for client laptops or workstations. After the range of IP addresses is established, the DHCP server dynamically assigns addresses to workstations as needed. The server assigns the device a dynamic IP address as long as the encryption settings are compatible with the WLAN. The threat with DHCP is that a malicious user could easily gain unauthorized access on the network through the use of a laptop with a wireless NIC. Because DHCP servers will not necessarily know which wireless devices have access, the server will automatically assign the laptop a valid IP address. |
|
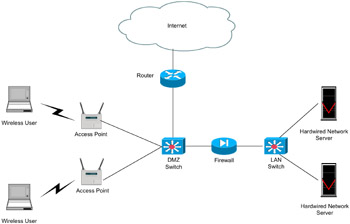
Figure 12.1: WISDOM Basic Security topology.
12.5.2 WISDOM Intermediate Security Measures
WISDOM Intermediate Security is designed for WLANs in a converged network that contains proprietary or very sensitive data. WISDOM Intermediate Security also requires that the WLAN security management considerations and those required for WISDOM Basic Security described earlier be implemented as part of its layered approach. WISDOM Intermediate Security uses a vendor-neutral solution, specifically RADIUS, for centralized user management and domain/directory authentication, and a dynamic keying model using EAP and 802.1 x called LEAP to provide moderate security risk mitigation for threats against integrity and confidentiality in a WLAN environment. RADIUS reduces or even eliminates WEP vulnerabilities to attacks on integrity and confidentiality, and it allows the administrator to centrally manage MAC addresses with a central database for authentication and key management. This greatly reduces the burden of work for administrators.
The use of RADIUS avoids the need to manually program a static MAC address into each AP to which users require access. It centralizes user management and domain/directory authentication, which makes it possible to create dynamic user-and session-specific keys instead of static keys for WEP encryption. It also provides accounting reports that detail user access and authentication. These reports assist in tracking user access to resources and attempts to gain unauthorized access. Drawbacks to implementing RADIUS include the use of additional equipment, software, administrative key management, and training.
The WISDOM Intermediate Security topology (see Figure 12.2) allows users to connect to the WLAN using their regular domain authentication credentials. In addition, the vulnerabilities associated with WEP (specifically, the key-scheduling and weak-key problems) are eliminated. This design places the RADIUS server on the inside of the network, which requires the administrator to allow RADIUS traffic through the firewall. This design uses a Cisco Secure ACS server as the RADIUS server.
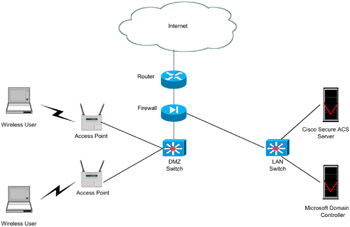
Figure 12.2: WISDOM Intermediate Security topology.
This approach also focuses on a framework for providing centralized authentication and dynamic key distribution. A proposal jointly submitted to the IEEE by Cisco Systems, Microsoft, and other organizations introduced an end-to-end framework using 802.1 x and EAP, called LEAP, to provide this enhanced functionality. Central to this proposal are two main elements:
-
EAP allows wireless client adapters that may support different authentication types to communicate with different back-end servers such as RADIUS.
-
IEEE 802.1 x , is a standard for port-based network access control
When these features are implemented, a wireless client that associates with an AP cannot gain access to the network until the user performs a network logon. When the user enters a username and password into a network logon dialog box or its equivalent, the client and a RADIUS server perform a mutual authentication, with the client authenticated by the supplied username and password. The RADIUS server and client then derive a client-specific WEP key to be used by the client for the current logon session. The process for this sequence of events is explained later. User passwords and session keys are never transmitted in the clear over the wireless link.
The WLAN access points will be connected to Layer 2 access switches. RADIUS and DHCP servers will be simulated as being located in the server module of the wired network. Security in the design is maintained by preventing network access in the event of a RADIUS service failure. Because most of the mitigation against security risks will rely on the RADIUS service, this behavior is required. If the DHCP servers are unavailable to the WLAN, the wireless clients will not be able to establish IP connectivity with the wired network, and management of the solution will be hindered. The wireless clients and APs use LEAP to authenticate the WLAN client devices and end users against the RADIUS servers.
Because the LEAP process does not support One-Time Password (OTP), a significant security hole is introduced into the network because attackers can attempt to brute force attack the LEAP authentication process. This requires that users choose strong passwords and that the administrator set account lockouts after a small number of incorrect login attempts. This configuration can be made at the RADIUS server. For scalability and manageability purposes, the WLAN client devices are configured to use the DHCP protocol for IP configuration. DHCP occurs after the device and end user are successfully authenticated via LEAP. After successful DHCP configuration, the wireless end user is allowed access to the corporate network. Filtering in place at the first Layer 3 switch prevents the wireless network from accessing portions of the wired network, as dictated by an organization's security policy.
LEAP provides two significant benefits over basic WEP. The first benefit is the mutual authentication scheme as described previously. This scheme effectively eliminates man-in-the-middle attacks introduced by rogue access points and RADIUS servers. The second benefit is centralized management and distribution of the encryption keys used by WEP. Even if the WEP implementation of RC4 had no flaws, there would still be the administrative difficulty of distributing static keys to all of the APs and clients in the network. Each time a wireless device was lost, the network would need to be rekeyed to prevent the lost system from gaining unauthorized access. The process is as follows: (1) a wireless client associates with an access point; (2) the access point blocks all attempts by the client to gain access to network resources until the client logs on to the network; (3) the user on the client supplies a username and password in a network logon dialog box or its equivalent; and (4) using 802.1 x and EAP, the wireless client and a RADIUS server on the wired LAN perform a mutual authentication through the access point.
With the Cisco authentication type of LEAP enabled, the RADIUS server sends an authentication challenge to the client. The client uses a one-way hash, also called a message digest, of the user-supplied password to respond to the challenge and sends that response to the RADIUS server. Using information from its user database, the RADIUS server creates its own response and compares that to the response from the client. When the RADIUS server authenticates the client, the process repeats in reverse, enabling the client to authenticate the RADIUS server. When mutual authentication is successfully completed, the RADIUS server and the client determine a WEP key that is distinct to the client. The client loads this key and prepares to use it for the logon session. The RADIUS server then sends the WEP key, called a session key, over the wired LAN to the access point. Next, the access point encrypts its broadcast key with the session key and sends the encrypted key to the client, which uses the session key to decrypt it; the client and access point activate WEP and use the session and broadcast WEP keys for all communications during the remainder of the session. Both the session key and broadcast key are changed at regular intervals, as configured in the RADIUS server.
WISDOM Intermediate Security eliminates the known WEP vulnerabilities to integrity and confidentiality attacks; greatly reduces the burden and vulnerability of administrators who have to manually program a static MAC address into each AP to which users require access; provides centralized user management and domain/directory authentication, which makes it possible to create dynamic user-and session-specific keys instead of static keys used for WEP encryption; and creates accounting reports that detail user access and authorization that can help in tracking who has been using the resources when someone might be attempting to gain unauthorized access. The 18 WISDOM Intermediate Security vulnerability, threat, and mitigation elements are described in Table 12.2. Key design features and components for WISDOM Intermediate Security are as follows:
-
Wireless client adapter and software. This is a software solution that provides the hardware and software necessary for wireless communications to the AP; it provides mutual authentication to the AP via LEAP.
-
Wireless AP. This mutually authenticates wireless clients via LEAP.
-
Layer 2 switch. This provides Ethernet connectivity between the WLAN APs and the wired network.
-
Layer 3 switch. This routes and switches production network data from one module to another and provides additional policy enforcement via protocol-level filtering for wireless traffic
-
DHCP server. This delivers IP configuration information for wireless LEAP clients.
-
RADIUS server. This delivers user-based authentication for wireless clients and access-point authentication to the wireless clients. It authenticates wireless users terminating on the VPN gateway, and optionally talks to an OTP server.
-
OTP server. This authorizes one-time password information relayed from the RADIUS server.
-
CISCO LEAP implementation software. This includes Cisco AP350 or AP340 with firmware 11.10T; Cisco Aironet 350 or 340 client adapter firmware 42523; Cisco Aironet Client Utility 501001; Cisco Aironet Drivers 8.01.06; and Cisco Secure ACS Server (CSACS) v2.6 or later. This will provide for EAP allows wireless client adapters that may support different authentication types to communicate with different back-end servers such as RADIUS and IEEE 802.1 x and provides for port-based network access control.
| Vulnerability | Threat | Mitigation |
|---|---|---|
| Password attack. An attacker who obtains some sensitive password-derived data, such as a hashed password, performs a series of computations using every possible guess for the password. Because passwords are typically small by cryptographic standards, the password can often be determined by brute force. Depending on the system, the password, and the skills of the attacker, such an attack can be completed in days, hours, or perhaps only a few seconds. A password database should always be kept secret to prevent a dictionary attack on the data. Obsolete password methods also permit dictionary attack by someone who eavesdrops on the network. Strong password policy enforcement methods prevent this occurrence. | Because LEAP does not support one-time passwords (OTPs), the user-authentication process is susceptible to password attacks. | Audit selected passwords for weakness and adherence to a good password usage policy that limits the number of tries for a logon before locking out the account. |
| WEP integrity and confidentiality attacks. WEP is designed to handle integrity and confidentiality through the Integrity Check Value (ICV), where both the frame and ICV are encrypted. Both the WEP ICV and its encryption algorithm are flawed and, hence, subject to exploitation. | WEP vulnerabilities result in WLAN susceptibility to integrity and confidentiality attacks. | Use RADIUS to mitigate or eliminate this vulnerability through the central management of MAC addresses and central database for authentication and key management. |
| Static MAC addresses. | MAC addresses are easily sniffed by an attacker because they must appear in the clear even when WEP is enabled, and wireless cards permit the changing of their MAC address via software. | Use RADIUS to avoid the need to manually program a static MAC address into each AP that processes user logon requests . This will centralize user management and domain/directory authentication, which makes it possible to create dynamic user-and session-specific keys instead of static keys for WEP encryption. Furthermore, it provides accounting reports that detail each user access and authentication attempt. |
| Unauthorized access. The very nature of wireless networks make them more susceptible to unauthorized access than wired networks. Because wireless is broadcast in nature, anyone within range of a wireless card can intercept the packets being sent out without interrupting the flow of data between wireless card and base station, which permits an attacker to gain access beyond the physical security perimeter. | Uncontrolled wireless access can allow attackers to read e-mail, sniff passwords, gain administrative access to machines, plant access to machines, plant Trojan horses or backdoors, and use wireless access points to launch other attacks. | Use RADIUS reports to assist in tracking user access to resources and attempts to gain unauthorized access. |
| Unauthenticated access. Authentication is a key element of network security control. Anonymous or unauthenticated access to a network can result in compromise, theft, or unauthorized destruction or modification of data. | Unauthenticated access can provide an opportunity for an unauthorized user to gain access to network, data, and resources. |
|
| AP User Password. | Login to the AP by unauthorized user is possible if no password is required. Although you must use the default password when you first open the configuration pages of the AP, immediately change the password to avoid a security breach because a default password is generally known or readily available. | Implement a strong AP user password with both alphanumeric and special characters and a minimum password length of eight characters. In addition, password expirations should be set at 30 days. |
| WEP IV weaknesses. To avoid encrypting two ciphertexts with the same key stream, an Initialization Vector (IV) is used to augment the shared secret key and to produce a different RC4 key for each packet. The IV is also included in the packet, but both of these measures are implemented incorrectly, resulting in poor security. | Attacks against WEP rely on exploiting multiple weak IVs in a stream of encrypted traffic. | Implement LEAP to enable WEP key hashing. The IV and WEP key are hashed to produce a unique packet key (called a temporal key ), which is then combined with the IV and XORed with the plaintext. This scenario prevents the weak IVs from being used to derive the base WEP key because the weak IVs allow only you to derive the per-packet WEP key. In order to prevent attacks caused by IV collisions, the base key should be changed before the IVs repeat. Because IVs on a busy network can repeat in a matter of hours, mechanisms such as LEAP should be used to perform the rekey operation. |
| Static WEP key. The weakness of most WLANs is their use of a single static WEP key that is shared among more than one user. In practice, many installations use a single key that is shared between all mobile stations and access points for ease of administration. From a security point of view, this practice results in unnecessary risk and is an unacceptable security practice. | The use of a static WEP key results in many users in a wireless network potentially sharing the identical key for long periods because of the lack of any key management provisions in the WEP protocol. If a computer such as a laptop were lost or stolen, the key could become compromised along with all of the other computers sharing that key. Moreover, because every station uses the same key, a large amount of traffic may be rapidly available to an eavesdropper for analytic attacks. | Implement LEAP. By employing a dynamic WEP encryption key for every user and enabling that key to change frequently, the LEAP security solution greatly diminishes the risk from this vulnerability. LEAP augments 802.11b WEP by creating a per-user, per-session , dynamic WEP key tied to the network logon, thereby addressing the limitations of static WEP. |
| Cleartext WEP IV. The WEP IV is sent in cleartext and is subject to sniffer exploitation to determine the key stream and use it to decrypt the ciphertext . | The IV in WEP is a 24-bit field sent in the cleartext portion of a message. The 24-bit string, used to initialize the key stream generated by the RC4 algorithm, is a relatively small field when used for cryptographic purposes. Reuse of the same IV produces identical key streams for the protection of data, and the short IV guarantees that they will repeat after a relatively short time (typically 5 to 7 hours) in a busy network. Moreover, the 802.11 standard does not specify how the IVs are set or changed, and individual wireless NICs from the same vendor may all generate the same IV sequences, or some wireless NICs may possibly use a constant IV. As a result, hackers can record network traffic, determine the key stream, and use it to decrypt the ciphertext. | Implement LEAP. The LEAP security solution changes the IV on a per-packet basis so that hackers can find no predetermined sequence to exploit. This capability, coupled with the reduction in possible attack windows , greatly mitigates exposure to hacker attacks because of frequent key rotation. In particular, this makes it difficult to create table-based attacks based on the knowledge of the IVs seen on the wireless network. |
| IV and RC4 encryption key weaknesses. The RC4 algorithm and its implementation by the WEP protocol have weaknesses that can be exploited. There are several weaknesses in the algorithm: it contains a large number of inherently weak keys, part of the key can be exposed to attackers if they can observe enough encrypted traffic, and there is a random generation issue for the keys. | The ability of an eavesdropper knowing 24 bits of every packet key, combined with a weakness in the RC4 key schedule, leads to a deadly analytic attack that recovers the key after intercepting and analyzing only a relatively small amount of traffic. This attack has been perfected to the point that scripts are commonly available on the Internet for such purposes. | Implement LEAP. LEAP changes the IV on a per-packet basis so that hackers can find no predetermined sequence to exploit. This capability, coupled with the reduction in possible attack windows, greatly mitigates exposure to hacker attacks because of frequent key rotation. In particular, this makes it difficult to create table-based attacks based on the knowledge of the IVs seen on the wireless network. The original shared-secret secure-key derivation is used to construct responses to the mutual challenges. It undergoes irreversible one-way hashes that make password-replay attacks impossible . The hash values sent over the wire are valid for one-time use only at the start of the authentication process. |
| WEP cryptographic integrity. WEP provides no cryptographic integrity protection and uses a noncryptographic Cyclic Redundancy Check (CRC) to check the integrity of packets and acknowledges packets with the correct checksum. This can result in an unintended "side channel" attack and susceptibility to a specific CRC active attack. | WEP provides no cryptographic integrity protection, and the 802.11 MAC protocol uses a noncryptographic CRC to check the integrity of packets, and acknowledges packets with the correct checksum. The combination of noncryptographic checksums with stream ciphers is dangerous and often leads to unintended "side channel" attacks, as is the case for WEP. An active attack permits the attacker to decrypt any packet by systematically modifying the packet and CRC sending it to the AP, noting whether the packet is acknowledged or not. | Implement LEAP. LEAP changes the IV on a per-packet basis so that hackers can find no predetermined sequence to exploit. This capability, coupled with the reduction in possible attack windows, greatly mitigates exposure to hacker attacks because of frequent key rotation. In particular, this makes it difficult to create table-based attacks based on the knowledge of the IVs used on the wireless network. The original shared-secret secure-key derivation is used to construct responses to the mutual challenges. It undergoes irreversible one-way hashes. |
| Broadcast monitoring. If an access point is connected to a hub rather than a switch, any network traffic across that hub can potentially be broadcast over the wireless network. | 802.11 WLANs are susceptible to broadcast monitoring. An unauthorized user can monitor traffic, using a laptop NIC in promiscuous mode when an access point is connected to a hub instead of a switch. Hubs generally broadcast all network traffic to all connected devices, which leaves the traffic vulnerable to unauthorized monitoring. For example, if a wireless access point were connected to an Ethernet hub, a device that was monitoring broadcast traffic could pick up data intended for wireless clients. | Ensure that switches are used instead of hubs for connections to wireless access points. |
| Replay attacks against WEP. WEP is susceptible to an IV replay attack where an attacker sends a known plaintext to an observable wireless client, then sniffs the wireless client for ciphertext and subsequently compares the plaintext and the ciphertext to derive the key system. On average, a random selection of IVs will lead to IV reuse in around 5,000 packets. | The message integrity check (MIC) protects WEP frames from tampering. The MIC is based on a seed value, destination MAC, source MAC, and payload (e.g., any changes to these will affect the MIC value). The MIC is included in the WEP-encrypted payload. MIC uses a hashing algorithm to derive the resulting value. This is an improvement of the CRC-32 checksum function that is performed by standards-based WEP. With CRC-32, it is possible to compute the bit difference of two CRCs based on the bit difference of the messages over which they are taken. In other words, flipping bit n in the message results in a deterministic set of bits in the CRC that must be flipped to produce a correct checksum on the modified message. Because flipping bits carries through after an RC4 decryption, this allows the attacker to flip arbitrary bits in an encrypted message and correctly adjust the checksum so that the resulting message appears valid. | Implement LEAP. |
| IP spoofing. The attack is based on the fact that Internet communication between distant computers is routinely handled by routers, which find the best route by examining the destination address, but generally ignore the origination address. The origination address is only used by the destination machine when it responds back to the source. In a spoofing attack, the intruder sends messages to a computer indicating that the message has come from a trusted system. To be successful, the intruder must first determine the IP address of a trusted system and then modify the packet headers so that it appears as if the packets are coming from the trusted system. The attacker is fooling (spoofing) the distant computer into believing that it is a legitimate member of the network. The goal of the attack is to establish a connection that will allow the attacker to gain root access to the host, allowing the creation of a backdoor entry path into the target system. | WLANs are susceptible to IP spoofing. A hacker can use IP spoofing to gain unauthorized access to the network and computers. The intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host. To engage in IP spoofing, a hacker must first use a variety of techniques, such as social engineering, to find an IP address of a trusted host and then modify the packet headers so that it appears that the packets are coming from that host. | Implement RFC 2827 filtering on the Layer 3 switch. After authenticating with RFC 2827, filtering on the Layer 3 switch restricts any spoofing to the local subnet range. Hackers cannot perform IP spoofing without first authenticating to the WLAN. |
| Address Resolution Protocol (ARP) spoofing. ARP spoofing is a method of exploiting the interaction of IP and Ethernet protocols. It is only applicable to Ethernet networks supporting IP. It involves constructing forged ARP replies. By sending forged ARP replies, a target could be made to send frames destined for computer A to instead go to computer B. Computer A will have no idea this redirection took place. The process of updating a target computer's ARP cache with a forged entry is referred to as " poisoning ." | ARP is a TCP/IP-based protocol used to convert an IP address into a physical address (called a Data Link Control [DLC]) such as an Ethernet address. A host wishing to obtain a physical address broadcasts an ARP request onto the TCP/IP network. A host on the network that has the IP address in the request will reply with its physical hardware address. After authenticating, ARP spoofing attacks can be launched in the same manner as in a wired environment to intercept other users' data. | Implement LEAP for authentication control. Hackers cannot perform ARP spoofing without first authenticating to the WLAN. |
| Unauthorized network topology discovery. Network topology discovery is part of the reconnaissance process for an adversary planning for unauthorized access to a network or an attack. | Unauthorized topology discovery can occur in the same way that is possible in the wired network. Network topology can aid an adversary in the attack planning phase when this information is not otherwise available. | Implement LEAP. Unauthorized users cannot perform network discovery if they are unable to authenticate. |
| Wireless packet sniffers. The effort by which intruders can penetrate a wireless network is now being made easier with the release of several wireless sniffer software applications that allow intruders to passively collect data for real time or later analysis. Such analysis can lead to the compromise of the network. AirSNORT is an application that utilizes known WEP flaws to extract the WEP key and allow unauthorized network access. NetStumbler is a full-featured wireless sniffer that logs an extensive array of information about any wireless network it happens to encounter: the MAC address of the access point, network name, SSID, the manufacturer, channel in use, signal strength, and whether WEP is enabled, to name a few. An intruder looking to attack a target wireless network can use all of this information. | Wireless packet sniffers can take advantage of any of the known WEP attacks to derive the encryption key. | Implement LEAP. These threats are mitigated by the WEP enhancements and key rotation provided by LEAP. |
| Man-in-the-middle attacks. A man-in-the-middle attack security breach is when a malicious user intercepts, and possibly alters, data traveling along a network. Security auditing tools such as dsniff, sshmitm, and webmitm are capable of performing active man-in-themiddle attacks against encrypted SSH and HTTPS traffic. A rogue access point can utilize this default behavior to compel clients to connect to a node performing active man-in-the-middle attacks against sensitive traffic. | WLANs are susceptible to man-in-the-middle attacks. The man-in-the-middle or TCP hijacking attack is a well-known attack where an attacker sniffs packets from a network and modifies them. Next, the hacker inserts them back into the network traffic stream. There are a few programs/ source codes available for doing a TCP hijack . TCP hijacking is an exploit that targets the victim's TCP-based applications such as Telnet, rlogin, ftp, mail application, Web browser, etc. An attacker can grab unencrypted confidential information from a victim's network-based TCP application and can further degrade the authenticity and integrity of the data. | Implement LEAP. The mutual authentication nature of LEAP combined with the MIC prevents a hacker from inserting himself into the path of wireless communications. LEAP ensures mutual authentication between a wireless client and a back-end RADIUS server (Access Control Server 2000 v2.6). Communication between the access point and the RADIUS server is via a secure channel. This eliminates man-in-the-middle attacks by rogue access points and RADIUS servers. |
The WISDOM Intermediate Security topology is shown in Figure 12.2.
12.5.3 WISDOM Advanced Security Measures
WISDOM Advanced Security is designed for high-level security WLANs in a converged network that are subject to regulations or legal security requirements such as the Health Insurance Portability and Accountability Act (HIPAA) of 1996 (U.S. Department of Health and Human Services, 2002) for health care systems, and the Gramm -Leach-Bliley Act (GLBA) of 1999 (U.S. Federal Trade Commission, 2002) for financial data, sensitive and secure government systems, or those systems involved in financial transactions. WISDOM Advanced Security also requires that the WLAN security management considerations and those required for WISDOM Intermediate Security described earlier be implemented as part of its layered approach. WISDOM Advanced Security uses an Internet Protocol Security (IPSec) VPN design to provide high-security risk mitigation for Option Three.
Because of its widespread use and popularity on wired networks, IPSec is frequently recommended in the literature as a solution for overcoming the inadequate standards-based security mechanism built into 802.11 in wireless networks. Another option, the Point-to-Point Tunneling Protocol (PPTP), is popular in some Microsoft-dominated networks because it is built into many Microsoft products. IPSec is generally recommended over PPTP for VPN because IPSec is much more resilient in temperamental networking environments such as wireless. Also, because IPSec encrypts and authenticates traffic as needed, the overhead on the network is noticeably less than it is with PPTP, which also makes it possible to temporarily lose your wireless connection and come back without dropping your VPN connection. IPSec has many desirable built-in features, such as integrity checking, mutual authentication, and antireplay . Using a VPN appliance or firewall with IPSec-enabled WLAN clients does not require you to use only a single vendor's equipment, as does LEAP and some 802.1 x implementations.
IPSec has a few drawbacks in performance and cost that make the risk-benefit most applicable for use in Option Three. IPSec on the WLAN environment prevents roaming, which means that a user will not be able to seamlessly move about from one access point to another. IPSec requires the use of additional equipment, software, administrative management, and training. IPSec VPNs require some overhead in each packet, but this is very small compared to other VPN protocols such as PPTP. In addition, as a VPN protocol, it only supports unicast traffic, so applications that use only broadcast or multicast may not work correctly.
WISDOM Advanced Security uses a VPN appliance that allows limited Internet access for WLAN users, but requires an IPSec VPN connection before allowing entrance to the wired network. A VPN requires a VPN switch, also called a VPN gateway, that can be accessed from the Internet. Restricting unnecessary or redundant protocols from the LAN segments that connect the APs to the VPN gateway reduces the possibility of unidentified holes and vulnerabilities. The LAN segments that connect to wireless APs should connect to a corporate VPN gateway, but not directly to the production network. Eliminating APs from the production network minimizes the risk of attack techniques such as packet sniffing. This option also assumes that a WLAN security policy is in place.
IPSec is a framework of open standards for ensuring secure private communications over IP networks. IPSec VPNs use the services defined within IPSec to ensure the confidentiality, integrity, and authenticity of data communications across public networks, such as the Internet. IPSec also has a practical application to secure WLANs by overlaying IPSec on top of cleartext 802.11 wireless traffic. When IPSec is deployed in a WLAN environment, an IPSec client is placed on every PC connected to the wireless network, and the user is required to establish an IPSec tunnel to route any traffic to the wired network. Filters are put in place to prevent any wireless traffic from reaching a destination other than the VPN gateway and DHCP/DNS server. IPSec provides for confidentiality of IP traffic, as well as authentication and antireplay capabilities. Confidentiality is achieved through encryption using a variant of the Data Encryption Standard (DES) called Triple DES (3DES). Although IPSec is used primarily for data confidentiality, extensions to the standard allow for user authentication and authorization to occur as part of the IPSec process. This scenario offers a potential solution to the user differentiation problem with WLANs.
IPSec provides numerous security features. The following have configurable values for the administrator to define their behavior: data encryption, device authentication and credentialing, data integrity, address hiding, and Security-Association (SA) key aging. The IPSec standard requires use of either data integrity or data encryption; using both is optional. WISDOM Option Three will use both encryption and integrity. Data encryption will be set for 3DES. Data integrity comes in two types: 128-bit-strength Message Digest 5 (MD5)-HMAC or 160-bit-strength Secure Hash Algorithm (SHA)-HMAC. Because the bit strength of SHA is greater, it is considered more secure, and it will be used in this design. A session key's strength is proportional to the number of binary bits comprising the session key file. This means that session keys with a greater number of bits have a greater degree of security and are considerably more difficult to forcibly decode.
WISDOM Advanced Security uses IPSec VPN(s) as an overlay security mechanism to access the production network from a WLAN. The WLAN APs will connect to Layer 2 (OSI Model) switches and forward traffic from the WLAN to the wired LAN using IPSec to protect the data until it reaches the wired network. WEP will not be enabled in this design. The WLAN is considered an untrusted network, suitable only as a transit network for IPSec traffic. The WLAN clients associate with a wireless AP to establish connectivity to the wired network at Layer 2. The wireless clients then use DHCP and DNS services in the server module to establish connectivity to the wired network at Layer 3. When the wireless client is communicating with the wired network, but before the IPSec tunnel is established, the client traffic is not considered secure. All of the noted WLAN security issues are still present until the wireless client can secure communications with an IPSec VPN. In addition to the implementation of Option One security requirements, the following will be implemented to mitigate remaining WLAN vulnerabilities:
-
Personal firewall software is included on the wireless client to protect the client while it is connected to the untrusted WLAN network without the protection of IPSec.
-
In general terms, the VPN gateway delineates between the trusted wired network and the untrusted WLAN. The wireless client establishes a VPN connection to the VPN gateway to start secure communications to the corporate network. In the process of doing so, the VPN gateway provides device and user authentication via the IPSec VPN. Even with this filtering, the DNS and DHCP servers are still open to direct attack on the application protocols. Extra care will be taken to ensure that these systems are as secure as possible at the host level. This will include up-to-date OS and application patches and a Host-based Intrusion Detection System (HIDS).
The VPN gateway can use digital certificates or preshared public keys for wireless device authentication. The VPN gateway then takes advantage of One-Time Passwords (OTPs) to authenticate users to it. Without OTPs, the VPN gateways are vulnerable to brute force login attempts by hackers who have obtained the shared IPSec key used by the VPN gateway. The VPN gateway takes advantage of RADIUS services, which in turn contact the OTP server for user authentication. The VPN gateway uses DHCP for IP address configuration in order for the WLAN client to communicate through the VPN tunnel. Security in this configuration is maintained by preventing network access if a VPN gateway or RADIUS service fails. Both services are required in order for the client to reach the wired network with production traffic. In remote-access VPNs, user authentication and device authentication occurs. When the remote device is authenticated, some level of access control should be in place to permit only the traffic over the tunnel that should be there. Device authentication uses either a preshared key or valid digital certificate issued from a recognized CA to provide the identity of a device. Digital certificates scale better than unique preshared public key pairs because they allow any device to authenticate to any other device but do not have the security properties of wildcard keys.
A message digest is the representation of text in the form of a single string of digits, created using a formula called a one-way hash function. Encrypting a message digest with a private key creates a digital signature, which is an electronic means of authentication. A one-way hash is an algorithm that turns messages or text into a fixed string of digits, usually for security or data management purposes. The "one way" means that it is nearly impossible to derive the original text from the string. A one-way hash function is used to create digital signatures, which in turn identify and authenticate the sender and message of a digitally distributed message.
Digital certificates are not tied to IP addresses, but to unique, signed information on the device that is validated by the enterprise's CA. If a hacker compromises or steals a device with a digital certificate, the administrator will revoke the digital certificate and notify all other devices by publishing a new Certificate Revocation List (CRL). The CRL contains a CA-signed list of revoked certificates. When a device receives a request for tunnel establishment and uses a digital certificate for proof of identity, the device checks the peer certificate against the CRL. Much of the information required to manage certificates can be stored in a Lightweight Directory Access Protocol (LDAP)-compliant directory. LDAP can also contain CRL information.
LDAP, which is used for accessing directory services, provides even greater flexibility for managing certificates. The CA can use LDAP directory information as a means to issue certificates individually or in batches, depending on the security policies of the organization. Other routine management tasks , such as key management and renewing and revoking certificates, can be partially or fully automated with the aid of the directory. Devices generating digital certificates or validating received certificates during tunnel authentication and establishment must know the correct time of day (preferably Coordinated Universal Time [UTC]). This is more than just expiration, it is a frame in which the certificate is valid ”not before, not after. Time is also used to determine when the CRL expires so that a new one can be retrieved. Although checking CRLs can be configured as optional, it should always be enabled on remote and head-end devices when digital certificates are deployed. This is the only revocation scheme for digital certificates compared to preshared key pairs that are simply removed from the uncompromised devices.
After the device and user authentications (if applicable) are complete, IPSec access control occurs. Normally, the networks, hosts , and ports that are allowed to traverse the tunnels are defined in the Security Policy Database (SPD), as defined by the IPSec protocol (IETF, 2003). This database is populated by the use of ACLs, which are sometimes referred to as "crypto ACLs" or "network rules." For remote-access traffic filtering, access control occurs dynamically by loading the per-user granular authorization information when the user successfully authenticates via extended authentication (XAUTH).
WISDOM Advanced Security also provides internal users with connectivity to Internet services and Internet users with access to information on the public servers (e.g., Hypertext Transfer Protocol [HTTP], FTP, Simple Mail Transfer Protocol [SMTP], and DNS). Additionally, this design will terminate VPN traffic from remote users and remote sites as well as traffic from traditional dial-in users. The 10 WISDOM Advanced Security vulnerability, threat, and mitigation elements are described in Table 12.3. The WISDOM Advanced Security topology is shown in Figure 12.3. Key design features and components for WISDOM Advanced Security are as follows:
-
VPN gateway. This authenticates individual remote users and terminates their IPSec VPN tunnels.
-
Remote-access VPN client with personal firewall software. This software client provides end-to-end encrypted tunnels between individual PCs and the corporate wireless VPN gateways; personal firewall software provides device-level protection for individual PCs.
-
VPN firewall. This provides network-level protection of resources and stateful filtering of traffic and differentiated security for remote-access users; it authenticates trusted remote sites and provides connectivity using IPSec tunnels.
-
VPN concentrator. This authenticates individual remote users and terminates their IPSec tunnels.
-
NIDS appliance. This provides Layer 4 “to “Layer 7 monitoring of essential network segments in the module.
-
DHCP server. This delivers IP configuration information for wireless VPN clients before and after VPN establishment.
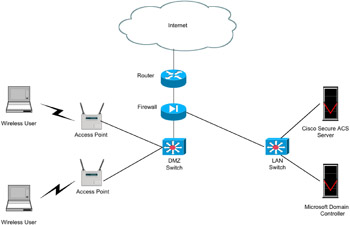
Figure 12.3: WISDOM Advanced Security topology.
| Vulnerability | Threat | Mitigation |
|---|---|---|
| Client's WLAN without IPSec protection. IPSec renders most of the commonly used attack methods completely ineffective . It does this by providing confidentiality, integrity, and authentication of traffic. | A client's system can be vulnerable to attack when it is connected to the untrusted WLAN network without the protection of IPSec. | Include personal firewall software on the wireless client to protect the client while it is connected to the untrusted WLAN network without the protection of IPSec. |
| DNS and DHCP server application protocols. These protocols are not protected by the VPN IPSec solution and will require supplementary host security best-practice implementation and third-party software to mitigate the risk of attack against the server(s). | In general terms, the VPN gateway delineates between the trusted wired network and the untrusted WLAN. The wireless client establishes a VPN connection to the VPN gateway to start secure communication to the corporate network. In the process of doing so, the VPN gateway provides device and user authentication via the IPSec VPN. This filtering does not protect the application protocols on the DNS and DHCP servers and therefore leaves them open to direct attack. Extra care must be taken to ensure that these systems are as secure as possible at the host level. | Implement host-level security to include updating and maintenance of the latest OS and application patches and the use of a host-based intrusion detection system (HIDS). |
| Wireless packet sniffers against WLAN clients. The effort needed for intruders to penetrate a wireless network is now being lessened with the release of several wireless sniffer software applications that allow intruders to passively collect data for real-time or later analysis. Such analysis can lead to the compromise of the network. AirSNORT is an application that utilizes known WEP flaws to extract the WEP key and allow unauthorized network access. NetStumbler is a full-featured wireless sniffer that logs an extensive array of information about any wireless network it happens to encounter: the MAC address of the access point, the network name, SSID, manufacturer, channel in use, signal strength, and whether WEP is enabled, to name a few. An intruder looking to attack a target wireless network can use all of this information. | Wireless packet sniffers can take advantage of any of the known WEP attacks to derive the encryption key and other information valuable for preattack reconnaissance. | Use IPSec encryption of wireless client traffic. |
| Man-in-the-middle attacks. A man-in-the-middle attack security breach is when a malicious user intercepts, and possibly alters, data traveling along a network. Security auditing tools such as dsniff, sshmitm, and webmitm are capable of performing active man-in-the-middle attacks against encrypted SSH and HTTPS traffic. A rogue access point can utilize this default behavior to compel clients to connect to a node performing active man-in-the-middle attacks against sensitive traffic. | WLANs are susceptible to man-in-the-middle attacks. The man-in-the-middle or TCP hijacking attack is a well-known attack where an attacker sniffs packets from a network, modifies them, and inserts them back into the network. There are a few programs/ source codes available for doing a TCP hijack. TCP hijacking is an exploit that targets the victim's TCP-based applications such as Telnet, rlogin, ftp, mail application, Web browser, etc. An attacker can grab unencrypted confidential information from a victim's network-based TCP application and can further degrade the authenticity and integrity of the data. | Use IPSec encryption of wireless client traffic. |
| DHCP IP configuration protocol spoofing. | By spoofing the client's packet exchange, a DHCP server will give all of the available leases to a spoofed MAC address, thus causing a denial of service. Any machine wishing to join the network after the attack would not be allocated an IP address because the whole of the DHCP range will have been either allocated to valid interfaces (i.e., interfaces already joined to the network before the attack took place) or spoofed MAC addresses. Any interface already joined to the network would not notice the effect of the attack because it has already been assigned an IP address, but interfaces without an IP address would not be able to join the network because the DHCP server will have no available IP addresses. A rogue DHCP server could also be set up by a hacker. The DHCP protocol can aid a hacker to redirect traffic through his or her machine (man-in-the-middle attack) or to send users to false Web pages (via a rogue DNS server). This could occur because a DHCP server can set various options, such as what IP address to use for the default gateway and what DNS servers to use. | Allow only the known protocols for initial IP configuration (DHCP) and VPN access (DNS, Internet Key Exchange [IKE], and Encapsulating Security Payload [ESP]) from the WLAN to the wired network through filtering at the AP and Layer 3 switch. Enforce authorization policies on the VPN gateway for individual user groups. |
| IP spoofing. The attack is based on the fact that Internet communication between distant computers is routinely handled by routers, which find the best route by examining the destination address, but generally ignore the origination address. The origination address is only used by the destination machine when it responds to the source. In a spoofing attack, the intruder sends messages to a computer indicating that the message has come from a trusted system. To be successful, the intruder must first determine the IP address of a trusted system and then modify the packet headers so that it appears as if the packets are coming from the trusted system. The attacker is fooling (spoofing) the distant computer into believing that he or she is a legitimate member of the network. The goal of the attack is to establish a connection that will allow the attacker to gain root access to the host, allowing the creation of a backdoor entry path into the target system. | WLANs are susceptible to IP spoofing. A hacker can use IP spoofing to gain unauthorized access to the network and computers, whereby the intruder sends messages to a computer with an IP address indicating that the message is coming from a trusted host. To engage in IP spoofing, a hacker must first use a variety of techniques to find an IP address of a trusted host and then modify the packet headers so that it appears as if the packets are coming from that host. | Implement IPSec. Hackers can spoof traffic on an unprotected WLAN, but only valid, authenticated IPSec packets will ever reach the production wired network. An effective measure against IP spoofing is the use of a VPN protocol such as IPSec. This methodology involves encryption of the data in the packet as well as the source address. The VPN software, or firmware, decrypts the packet and the source address and performs a checksum. If either the data or the source address have been tampered with, the packet will be dropped. Without access to the encryption keys, a potential intruder would be unable to penetrate the firewall. |
| ARP spoofing. ARP spoofing is a method of exploiting the interaction of IP and Ethernet protocols. It is only applicable to Ethernet networks supporting IP. ARP spoofing involves constructing forged ARP replies. By sending forged ARP replies, a target computer could be convinced to send frames destined for computer A to go instead to computer B. When it is done properly, computer A will have no idea that this redirection took place. The process of updating a target computer's ARP cache with a forged entry is referred to as "poisoning." | ARP is a TCP/IP-based protocol used to convert an IP address into a physical address (called a Data Link Control [DLC]) such as an Ethernet address. A host wishing to obtain a physical address broadcasts an ARP request onto the TCP/IP network. A host on the network that has the IP address in the request will reply with its physical hardware address. After authenticating, ARP spoofing attacks can be launched in the same manner as in a wired environment to intercept other users' data. | Implement IPSec. ARP spoofing attacks can be launched; however, data is encrypted to the VPN gateway, so hackers will be unable to read the data. |
| Password attacks. An attacker who obtains some sensitive password-derived data, such as a hashed password, performs a series of computations using every possible guess for the password. Because passwords are typically small by cryptographic standards, the password can often be determined by brute force. Depending on the system, the password, and the skills of the attacker, such an attack can be completed in days, hours, or perhaps only a few seconds. A password database should always be kept secret to prevent a dictionary attack on the data. Obsolete password methods also permit a dictionary attack by someone who eavesdrops on the network. Strong password policy enforcement methods prevent this occurrence. | As with wired networks, WLANs are vulnerable to exploitation when weak policies and password controls exist. | Implement good password policies, one-time-passwords (OTP), and auditing. |
| Unauthorized network topology discovery. Network topology discovery is part of the reconnaissance process for an adversary planning for unauthorized access to a network or an attack. | Unauthorized topology discovery can occur in the same way that is possible in the wired network. Network topology can aid an adversary in the attack planning phase when this information is not otherwise available. | Control IP configuration protocols. Only IKE, ESP, DNS, and DHCP will be allowed from the WLAN to the wired network. |
| MAC/IP spoofing from unauthenticated users. WLANs are susceptible to both MAC and IP spoofing. | Without IPSec, ARP spoofing and IP spoofing are still effective on the WLAN subnet client. | Implement IPSec to secure the connection. |
EAN: 2147483647
Pages: 153