10.4 Enhancing WLAN Security
10.4 Enhancing WLAN Security
In this section, segmentation devices and other techniques that can be used to enhance WLAN security are described. Segmentation devices are security devices that are used when implementing a demarcation between wired and wireless networks to mitigate the risk of exposure to the wired network from the WLAN. The techniques described herein add security to the wireless LAN by reducing the number of potential single points of failure in the network, isolating it, and controlling access to LAN-based internal services from the Internet.
10.4.1 Segmentation Devices
WLANs pose a unique problem because they do not have physical barriers and is data broadcast in the air. In general, a WLAN is more vulnerable to compromise and is less secure than a wired network. This requires wireless access points to be separated from the wired network by some type of security device. These devices are generally called segmentation devices and are used when implementing segmentation between wired and wireless networks. In a WLAN design, segmentation means placing the wireless access points on a network segment separated from the backbone network by some type of security device. An example of segmentation is shown in Figure 10.2. This section discusses the type of devices generally used for segmentation between WLANs and wired networks and the strengths and weaknesses of each.
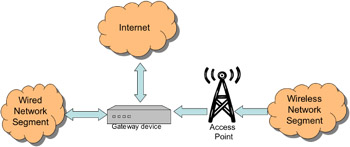
Figure 10.2: Segmentation of wired and wireless network segments.
Routers
The strongest level of security supported by a router is a firewall feature set, which is a strong set of access control lists (ACLs). Although routers are intelligent , their security functionality is relatively weak because of the way access lists are used in the device. If a router is used as a segmentation device, it needs to handle the traffic from approximately 15 to 20 access points, which equates to about 75 to 100 Mbps of throughput because each access point can push approximately 5 Mbps of wireless traffic. Routers are not always the best segmentation devices to use because the types of routers that can handle this volume of traffic are very expensive, and moderately priced routers generally have slow interfaces because their CPUs cannot push large amounts of traffic. Most routers use ACLs to ensure that clients match a predetermined set of criteria. Routers do not use authentication and are considered a security risk to be avoided in WLAN designs where authentication is extremely important. As an alternative, Cisco's IOS router software support for Mobile IP may be used in conjunction with Mobile IP software packages.
Layer 3 Switches
Layer 3 switches are routers that can perform switching functions and have many names , such as switch routers, route switches, and network layer switches. Virtual interfaces that exist logically are added to the switch as a switching functionality. Network traffic is routed through the Layer 3 switch between virtual interfaces in addition to switching traffic between physical interfaces mapped to the virtual interfaces.
A Virtual Ethernet Interface (VEI) is a pseudodevice that can be used as a cloned Ethernet device. VEI will respond to Ethernet packages for an IP address other than the normal address used for the machine. In this way, it is possible to have several IP addresses for a single Ethernet interface. Nodes that are attached to switched interfaces are switched to other interfaces falling under the same VEI, but they are routed to nodes attached to another designated port or ports. A number of physical switched interfaces can be assigned to a logical routed interface. The routed interface will be assigned an IP address just as the router's interface would be assigned one.
Layer 3 switches normally have fast, distributed CPUs per port or per block of ports and are somewhat expensive. Security on Layer 3 switches is performed with the use of ACLs on routed interfaces. Processing of these lists is greatly expedited because the switches are capable of much greater processing speeds and are much faster and more versatile than routers. Few Layer 3 switches support Mobile IP, and they have the same security limitations as routers because they do not provide any means of authentication.
VPN Concentrators
VPN concentrators, also known as VPN servers, are the cornerstones of secure remote access. The ability to scale from supporting just a few to many thousands of users is made possible through the use of RADIUS or TACACS+ authentication and multiple types of VPN technologies and protocols. VPN concentrators build an encrypted point-to-point connection between the client and the concentrator and block unauthenticated Layer 3 traffic from entering the backbone segment to prevent malicious eavesdropping. The client and server at each end of the VPN tunnel must use the same VPN protocol and settings. The security level of a VPN also depends on the protocols used.
VPN concentrators were never built specifically for use in wireless environments or as WLAN segmentation devices, and they leave access points unprotected just like any Layer 3 security device. EWGs with VPN concentrator functions have been designed for wireless operations and are a much better choice than using a VPN concentrator independently in a WLAN.
VPN concentrators, whether small or large, are expensive and are becoming even more so as the requirements for the number of simultaneously supported VPN tunnels increases . The strong authentication and encryption in VPNs comes with high overhead costs and decreased throughput. Interoperability between concentrators and client software should be taken into consideration during the network design phase. Specific VPN protocol maturity and support should also be considered.
Firewalls
The use and function of firewalls has evolved rapidly over the last few years , resulting in an increase in both features and the granularity with which firewalls can filter traffic. This can cause existing routers to bottleneck traffic and network throughput to suffer. Firewalls were initially used to filter traffic between network segments such as the intranet and the Internet and performed this function well. As high-bandwidth links became affordable, firewalls were enhanced to keep up with throughput demands and route and filter between many network segments. Multiport NICs were introduced into network devices as a result of the introduction of Demilitarized Zones (DMZs). Other detailed tasks performed by firewalls were added, such as stateful inspection, to keep intruders out.
The long-running arguments over task-specific firewalls versus general-purpose firewalls continue. One group maintains that a firewall is the best device for all filtering situations, while the other group assures its customers that firewalls should be task-oriented and purposefully designed units. WLAN security support has generally fallen in the "all-purpose group," resulting in expectations of the nearly impossible task of filtering unlike types of traffic at incredible speeds from a variety of audiences. The "purpose-built group" segmented firewalls into several different types, including Internet firewalls, WLAN firewalls, and other task-dependent types. Stateful inspection and any other type of low-level packet filtering and review can be performed adequately on a typical Internet firewall that deals with 1.5 and 10 Mbps of Internet traffic. A wireless access point at the same speed pushes 5 Mbps per AP. Common enterprise WLAN designs consist of 100 or more access points in a network. If these types of additional burdens are put on the firewall while minimizing the amount of filtering, they can handle such loads without causing a bottleneck in the network. A firewall may incorporate authentication and encryption in the form of an integrated VPN concentrator, but in so doing, the firewall takes on even more types of functions and traffic. Authentication requires either RADIUS support or a local database of users and routing, tunnel building, and data encryption functionality to be added to the filtering function.
Many organizations use their existing firewalls for WLAN segmentation because they are already in place before the WLAN is designed or installed. A firewall certainly has its place and may be part of an overall WLAN security design, but it is not a good stand-alone solution because WLAN environments grow rapidly in size and complexity. The best way to use a firewall to optimize security is to use it in conjunction with other solutions. A firewall can be used to segment the wireless segment where clients are required to use an SSH2 client to connect to an SSH2 server located on the backbone behind the firewall. The firewall can then be used to block all traffic except SSH2 tunnel traffic destined to the IP address of the SSH2 server, resulting in greater throughput between the WLAN and the backbone segment of the network because the overhead of encryption, routing, authentication, firewall management, and other work can be shared between the SSH2 server and the firewall.
Enterprise Encryption Gateways
The Enterprise Encryption Gateway (EEG) serves as a gateway device because it segments wireless networks from a network's backbone. The access points and EEGs are managed from the unencrypted segment of the network. An authentication server such as RADIUS or an Access Control Server (ACS) and a management station are also used in this configuration.
Ethernet frames that originate from or are routed to the WLAN segment are taken by EEG Layer 2 encryption devices and placed in proprietary frame formats that traverse both the wireless and wired segments. This is identical to the basic Layer 2 VPN design where each link is an encrypted point-to-point tunnel between the client and the gateway. The Layer 3 to 7 information is removed from the proprietary frame after the traffic arrives at the gateway and is placed in a standard Ethernet frame for delivery upstream to the destination station.
EEGs do not perform routing and are assigned an IP address for management purposes only. Gateways and clients use a proprietary frame format to compress the data payload for increased throughput. Gains in throughput are directly related to the amount of payload compression and type of data being compressed. 3DES or AES algorithms are used when strong encryption is required, but they significantly increase overhead and latency, thereby reducing throughput. Noticeable differences in network throughput can be achieved by mandating the use of compression schemes or by moving encryption and decryption to a dedicated off-load processor.
EEG supports access point management as part of its configuration to include the IP and MAC address of each access point behind a gateway. Depending on the type of tasks that can be performed (e.g., Telnet, HTTP, and HTTPS), Layer 4 port filtering might be appropriate to implement. A filtered request sent to an access point or bridge located on the encrypted side of an EEG will send the traffic unencrypted to the wireless infrastructure device so the device may properly read the traffic.
RADIUS authentication is supported from EEGs through a proprietary ACS. To provide seamless integration with an existing environment, the ACS may redirect authentication requests to a RADIUS server. The ACS provides added value to the wireless network because it has vendor-specific security and other management features not found in RADIUS.
Enterprise Wireless Gateways
EWGs are the end result of the evolution of various networking hardware and software products to meet a specific set of needs for wireless networks. The implementation and management complexities, cost of simultaneous deployment, and weaknesses of Layer 3 switches, firewalls, routers, and VPN concentrators helped shape the evolution of the EWG. The EWG combines the features common to all of the aforementioned devices and additional features specific to wireless networks. EWGs lack protection for access points and must use a separate security solution to meet this need.
EWGs are normally used as a gateway positioned between the wireless network segment and the network backbone through which WLAN clients can access the network core or backbone. EWGs should reside between VLANs when they are used to separate WLANs from backbone networks. EWGs act as routers, with one interface on the unprotected wireless side and the other interface on the protected wired side, with each interface having its own IP address. It is possible for NAT to perform in both directions, with each direction having a different purpose. Because of the high volume of traffic traversing these types of networks, the interfaces are always Fast Ethernet or Gigabit Ethernet.
Although many EWGs integrate firewall features, it is rare for an EWG to have a set of features comparable to an enterprise firewall software package because of costs and the amount of traffic that will traverse the EWG in comparison to an enterprise firewall. As with regular firewalls, if the filtering and analysis of inbound and outbound traffic become more complex, the firewall's ability to process traffic is reduced and the number of simultaneously supported access points will decrease along with the number of simultaneously supported wireless clients. An administrator's comfort level with the EWG firewall features will depend on his or her knowledge of firewall administration and technology.
The VPN concentrator function acts as the primary security feature for most EWGs. It provides support for most VPN types to include IPSec, PPTP, and L2TP. VPN concentrators also integrate IPSec VPN implementations with diverse feature sets and support for RADIUS, optional local user databases, LDAP support, and other authentication methods .
The lack of user authentication and authorization found in current WLAN standards and the unique mobile nature of wireless clients drove the development of special features in EWGs that are specific to wireless, including RBAC, rate limiting, and proprietary methods of subnet roaming, discussed later in this chapter.
There are two main types of EWGs: appliance (hardware) and software. EWG appliances are stand-alone boxes that may resemble a rack-mountable PC in a 1U or 2U chassis. EWG software and operating systems are often combined into one unit running versions of Linux or FreeBSD operating systems, and they are managed from a console port or through a Web interface using HTTP, Telnet, HTTPS, or SNMP. A replacement firmware file, typically in binary format such as .bin, must be uploaded to the unit through the management interface to upgrade these units.
The software EWG is the second common type of EWG and can run on a typical Intel PC with two Ethernet interfaces on top of operating systems such as Windows and Linux. Some are similar in operation to network appliances and come with a complete operating system and needed applications. Others have a master/slave or client/server configuration where one centralized piece of software controls many client pieces, and those typically run on top of a Windows or Linux operating system. Software and hardware EWGs each have disadvantages. Software EWGs require additional costs for an additional computer(s), and if required, operating system software. This can also introduce a single point of failure on the network. Hardware EWGs also have higher costs. Given that the management costs, in terms of time and difficulty, are about the same for both types, the software solution will probably be the best decision for those companies that already have the required computer platform(s) and operating system licenses.
It is important to consider performance during the EWG selection process. The rather young wireless industry has not had time to standardize the large variance of interface and management demands among EWG units. Even so, vendors in this space are targeting large enterprise customers and creating units that scale to accommodate very large workloads. Performance factors such as the number of simultaneous users, unencrypted throughput, and encrypted throughput should be kept in mind when selecting an EWG. The number of simultaneous user sessions that can be supported by the unit will help determine the number of EWGs required in an organization. If the machine is supporting the maximum number of users and all users are active, it is important to know if the EWG can keep up with the load, or the EWG can become a chokepoint on the network. Even though the primary purpose of the EWG is authentication and encryption, most vendors talk about the unencrypted throughput number because it is more impressive than the figures for encrypted traffic. Depending on the type of encryption used, the encrypted data throughput number is usually significantly lower than the unencrypted throughput and far less than the speed of the interfaces both upstream and downstream. An EWG may have very fast interfaces, but this does not mean it can push as much traffic as the interfaces can pass to it.
Scalability of a prospective EWG is another important factor to consider when designing and implementing a wireless network. Network growth, standards support, limitation of features, increased number of clients and/ or access points, increased bandwidth, and technology independent enough to scale adequately are all issues that can cause an EWG to become a chokepoint if they have not been factored correctly into the design. Interfaces can be fast enough to support 802.11b devices, but the CPUs may not be able to keep up with the increased workload when new technologies become available, such as 802.11a and 802.11g. Colocating 802.11g with 802.11b or replacing 802.11b access points with 802.11a can produce a scenario where the EWG could easily become overloaded if it was not designed for higher bandwidths. Through firmware or software upgrades, EWGs should support the latest technologies on the market that positively affect its ability to scale to the needs of the network. If your EWG vendor does not keep the firmware or software updated, you may reach a point where you have to replace the EWGs to grow the network.
10.4.2 Techniques
In this section, the techniques of network segmentation, redundancy, NAT / Network Address Port Translation (NAPT) and RBAC are discussed in relation to their ability to enhance the security of WLANs. Network segmentation and redundancy is presented from the viewpoint of preventing single points of failure. NAT enhances the security of business networks by hiding the IP addresses of hosts from the outside world, making it more difficult for attackers to penetrate and compromise a network. NAT also protects against Internet users directly accessing Web and FTP servers used internally on the private network. Through the use of NAPT, connections from the Internet to the private network are virtually impossible. Unlike simple packet filters, passing any unsolicited traffic from an external host to the private network is prevented. Unsolicited packets are those that have not been initiated by a private host. The only inbound traffic able to traverse NAPT is that traffic which has been solicited. This is similar to the effect of a stateful firewall. RBAC is attracting increasing attention because it reduces the complexity and cost of security administration in large networked applications. With RBAC, security is managed at a level that corresponds closely with the organization's structure, and complexities introduced by mutually exclusive roles or by role hierarchies are managed much more easily.
Redundancy
The decision to include and deploy network segmentation in the overall wireless design should be weighed carefully because segmentation can result in a single point of failure for the entire WLAN, or at a minimum, a segment of the WLAN. The need to address redundancy in the network segmentation should not be ignored. For example, the entire WLAN segment would be unable to connect to the network backbone if all of a network's access points are on the same VLAN and separated from the main VLAN by a router that failed. Good WLAN network designs should mandate redundancy through the use of hot and cold failover access points, access point colocation, or even the use of multiple frequency bands as with 802.11a and 802.11b. Backup router protocols such as Virtual Router Redundancy Protocol (VRRP) and Hot Standby Routing Protocol (HSRP) have traditionally been used to design and build a redundant network. Manufacturers of EWGs, firewalls, and other device types have been forced to adopt some type of backup mechanism because routers are not the only segmentation devices in wireless networks.
NAT/NAPT
NAT is a method of connecting multiple computers to the Internet (or any other IP network) using one IP address. It is most often used to conserve public IP space by translating private IP ranges into public ones. NAPT is an extension to basic NAT in that many network addresses and their TCP/UDP ports are translated to a single network address and its TCP/UDP ports. NAPT is also called Port Address Translation (PAT) or NAT overloading and presents some challenges in VPN and 802.1 x /EAP networks. The use of NAPT on a router allows a network administrator to configure the network so that it will use only one public IP address on the outside interface of the router while masking the private IP addresses of the computers inside the router. The router uses a dynamic table of inside-to-outside translations to allow the internal private IP users to access the Internet through a single public IP address. If used correctly, NAPT can be a good solution for use with segmented WLANs because NAPT can conserve backbone IP space by using private IP ranges in the WLAN segments. Unfortunately, many VPN protocols and routers do not support NAT or NAPT.
NAPT configuration issues can result from an EWG connected to a network backbone and performing NAPT on all traffic sent between the WLAN and the LAN backbone. Through the use of virtual servers, port mapping is typically the only way to go backward through a NAPT router. Only one access point can be managed with this method, making this scenario infeasible. An alternative solution is to perform a 1:1 static NAT mapping through an EWG that assigns backbone IP addresses to the access points and answers on behalf of each access point. After the EWG answers on behalf of the access point, it forwards traffic between the protected backbone segment and the unprotected WLAN segment. This, of course, requires the EWG to have a 1:1 static NAT mapping capability.
802.1 x port-based access control on access points located on the unprotected segment of the EWG will cause some problems when used with NAPT. The 802.1 x /EAP traffic must pass through the EWG and be routed to IP addresses translated onto the backbone segment using NAT because the RADIUS server will be located on the protected backbone segment. When the access point sends traffic to the RADIUS server, it will see the traffic as coming from each statically NAT'd address on the backbone segment. The static NAT table entry will take precedence over NAPT because the static NAT entry will be in the NAT table before any NAPT translation is ever attempted. When the RADIUS server is configured, each NAT entry must be configured with the IP address that resides on the backbone segment, which will be translated from the EWG onto the wireless segment. In these types of scenarios, the EWG will handle the return translation and session information. The RADIUS server recognizes the wireless users as a single IP address (also the EWG's backbone IP address) in this type of design, and it recognizes each access point individually according to how the static 1:1 NAT is configured. This design will also require the access points to be configured to have a gateway address. The RADIUS requests must be routed by the EWG to the RADIUS server because the access point is not on the same network segment as the RADIUS server.
Role-Based Access Control
RBAC defines "roles" based on job description or network use requirements. Any user assigned to a role inherits the defined properties of that role, aiding in both network security and bandwidth control. For example, a role of "security administrator" may be assigned to the wireless security manager, which results in that person's being given access to the Internet and the corporate intranet to include full bandwidth use. The role of "guest" could be used to limit the use of bandwidth and use of the Internet only. The popularity of RBAC in EWGs has increased along with the growing need for stronger access control within enterprise wireless networks.
RBAC provides significant advantage for VPNs used in 802.1 x solutions. Basing the user's role in the network on the ability to assign guest, authorized user, administrator, and other types of privileges (such as server-access or high-bandwidth levels) has many advantages. When the Internet is accessed through a wireless network, RBAC can reduce administrative overhead by managing contractor, guest, or other authorized external user access by assigning the guest user to a particular role, where no encryption, user registration, or other time-consuming tasks are necessary. The ability to individualize account features and put users into appropriate role categories has significant value in many organizations.
EAN: 2147483647
Pages: 153