Chapter 7: Wireless Networking Basics
Organizations are adopting wireless networking technologies to address networking requirements in ever-increasing numbers . The phenomenal rate of change in wireless standards and technology complicates the decision of how to implement or update the technology. In this chapter, we delve into the inner workings of the wireless LAN (WLAN) environment of today. We start by concentrating on the specific topic areas related to wireless networking technology. We explain how LANs and WLANs work, coexist, and interoperate . We discuss the varying wireless standards that exist today and look at some future standards. Mobile workforces drive the need for strong understanding of the issues surrounding mobile security, and we cover those issues in fairly extensive detail. Because mobile security requires encryption to work, we cover the various encryption standards in use today and explain the strengths and weaknesses of each. At the end of this chapter, you should have a fundamental grasp of the essentials of wireless networking. Now, let's begin by taking a look at WLANs.
7.1 Wireless Local Area Networks
In 1997, the IEEE ratified the 802.11 WLAN standards, establishing a global standard for implementing and deploying WLANs. The throughput for 802.11 is 2 Mbps, which was well below the IEEE 802.3 Ethernet counterpart . Late in 1999, the IEEE ratified the 802.11b standard extension, which raised the throughput to 11 Mbps, making this extension more comparable to the wired equivalent. The 802.11b standard also supports the 2-Mbps data rate and operates on the 2.4-GHz band in radio frequency for high-speed data communications.
WLANs are typically found within a small client node-dense locale (e.g., a campus or office building), or anywhere a traditional network cannot be deployed for logistical reasons. Benefits include user mobility in the coverage area, speed and simplicity of physical setup, and scalability. Being a military spinoff, WLANs also provide security features such as encryption, frequency hopping , and firewalls. Some of these features are intrinsic to the protocol, making some aspects of WLANs at least as secure as wired networks and usually more so. The drawbacks are high initial cost (mostly hardware), limited range, possibility of mutual interference, and the need to security-enable clients .
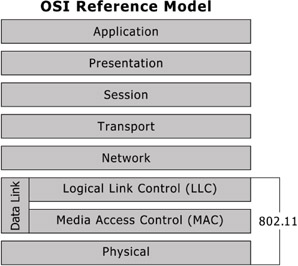
Figure 7.1: How 802.11 works in the OSI Model.
7.1.1 LANs and WLANs Explained
A LAN physically links computers in an organization together via network cabling, often specified as Ethernet CAT 5 cabling. With a wired LAN, computers are connected by a fixed network of wires that can be difficult to move and expensive to change. These wires run throughout the walls, ceilings, and floors of the organization's buildings . LANs allow data and applications to be shared on multiple computers. A LAN provides a means for applications and files to be accessed on a central server via wired (or wireless) connections.
A WLAN enables a local network of computers to exchange data or other information without the use of cables. It can either replace or extend a wired LAN. The data can be transmitted as radio signals through the air, walls, ceilings, and so on without wired cabling. Using WLANs, mobile computing devices may be carried from place to place in an organization while remaining continuously connected. Any device that is within the range of an access point can potentially connect to the WLAN. This provides greatly increased freedom and flexibility compared to a wired network. WLANs are typically built using two key components :
-
An access point, or base station, that is usually physically connected to a LAN
-
A wireless card that is either built into or added to a handheld, laptop, or desktop computer
Using WLANs, it is easy to provide access to additional users. Access points can be added as necessary to manage the capacity and growth of an organization. The most common wireless standard, 802.11b, has a data transfer rate of 11 Mbps ”much slower than current wired LANs, which operate at 100 Mbps. Newly installed wired networks now operate at up to 1,000 Mbps (1Gb). 802.11b devices are often branded with a Wireless Fidelity (WiFi) mark to indicate interoperability. A WLAN has sufficient bandwidth to handle a wide range of applications and services; however, it has a limited ability to deliver multimedia applications at sufficient quality, and a wired LAN is probably needed to access these. Ongoing advances in wireless standards continue to increase the data rate achievable with new equipment.
7.1.2 How WLANs work
In a typical WLAN, a transmitter/receiver (transceiver) device, called an access point, is normally physically connected to the wired network using standard cabling. At a minimum, the access point receives, buffers, and transmits data between the WLAN and the wired network infrastructure, using radio frequencies to transmit data to each user. A single access point can support a small group of users, normally within a range of up to 100 meters depending on the local environment.
To access a WLAN via the access point, users need a computer with a wireless network interface card (NIC) either built in or installed. A wireless NIC can be inserted into the PCMCIA slot of a computer, laptop, or handheld device. Wireless NIC cards can also be installed into the PCI expansion slot of a desktop computer. In either case, the necessary software drivers should also be installed. It is also possible to create a peer-to-peer network ”joining two or more computers together simply by installing a wireless NIC in each machine. Equally, it is possible for one of the computers in the peer-to-peer network to be joined to a LAN and to provide Internet access for the other computers in the network.
7.1.3 Advantages and Disadvantages of WLANs
WLANs have advantages and disadvantages when compared with wired LANs. A WLAN will make it simple to add or move workstations and to install access points to provide connectivity in areas where it is difficult to lay cable. Temporary or semipermanent buildings that are in range of an access point can be wirelessly connected to a LAN to give these buildings connectivity. Where computer labs are used in schools , the computers (laptops) could be put on a mobile cart and wheeled from classroom to classroom, provided they are in range of access points. Wired network points would be needed for each of the access points. A WLAN has some specific advantages:
-
It is easier to add or move workstations.
-
It is easier to provide connectivity in areas where it is difficult to lay cable.
-
Installation is fast and easy, and it can eliminate the need to pull cable through walls and ceilings.
-
Access to the network can be from anywhere within range of an access point.
-
Portable or semipermanent buildings can be connected using a WLAN.
-
Although the initial investment required for WLAN hardware can be similar to the cost of wired LAN hardware, installation expenses can be significantly lower.
-
When a facility is located on more than one site (such as on two sides of a road), a directional antenna can be used to avoid digging trenches under roads to connect the sites.
-
In historic buildings where traditional cabling would compromise the fa §ade, a WLAN can avoid the need to drill holes in walls.
-
Long- term cost benefits can be found in dynamic environments requiring frequent moves and changes.
WLANs also have some disadvantages:
-
As the number of computers using the network increases , the data transfer rate to each computer will decrease accordingly .
-
As standards change, it may be necessary to replace wireless cards and/or access points.
-
Lower wireless bandwidth means some applications such as video streaming will be more effective on a wired LAN.
-
Security is more difficult to guarantee and requires configuration.
-
Devices will only operate at a limited distance from an access point, with the distance determined by the standard used and buildings and other obstacles between the access point and the user.
-
A wired LAN is most likely to be required to provide a backbone to the WLAN; a WLAN should be a supplement to a wired LAN and not a complete solution.
-
Long-term cost benefits are harder to achieve in static environments that require few moves and changes.
7.1.4 Current WLAN Standards
The Institute of Electrical and Electronics Engineers (IEEE) 802.11b specification is the most common standard for WLANs. 802.11a has recently been cleared to operate without a license in the 5-GHz frequency range. Several other standards are still under development, including 802.11g, 802.11h, and Ultra Wideband (UWB).
IEEE 802.11a
802.11a operates in the 5-GHz waveband. Because they operate in different frequencies, 802.11b and 802.11a are incompatible. This means organizations that have already deployed 802.11b networks, but want the faster speeds available through 802.11a, will either have to build a new WLAN alongside the existing one or purchase hardware that allows for both types of wireless cards to coexist. Several manufacturers currently provide, or are planning to release, dual-mode access points, which can hold both 802.11a and 802.11b cards. The power output of 802.11a is restricted, and the range tapers off more quickly than in 802.11b.
At present, 802.11a experiences few of the signal interference and congestion problems occasionally experienced by 802.11b users, although this may change now that license restrictions on the 5-GHz frequency band have been lifted and use increases. We can expect to see an increase in dual-platform access points to ensure compatibility between equipment.
IEEE 802.11b
This type of equipment is most common for establishing a WLAN in business. Not all 802.11b equipment is compatible, so the WiFi compatibility mark has been developed. A WiFi mark indicates compatibility between 802.11b products from different manufacturers. 802.11b equipment that is not WiFi branded should be treated with caution. The 802.11b standard operates in the 2.4-GHz spectrum and has a nominal data transfer rate of 11 Mbps; however, in practice, the data transmission rate is approximately 4 to 7 Mbps, around one-tenth the speed of a current wired LAN. This is still adequate for accessing most data or applications, including Internet access, but would be insufficient for multimedia applications or for instances when a large number of simultaneous users want to access data in a single WLAN. Some manufacturers are producing 802.11b solutions with additional functionality that offers throughput at 22 Mbps speed. It is unclear if this type of equipment will be compatible across vendors .
7.1.5 Future WLAN Standards
Several standards are in development, all of which have a nominal data transfer rate of 54 Mbps, with actual data throughput probably in the vicinity of 27 to 30 Mbps. These standards, briefly discussed as follows , are known as IEEE 802.11g and IEEE 802.11h.
IEEE 802.11g
The IEEE is in the process of developing the 802.11g standard. Products have been launched by manufacturers such as Apple, D-link, and Buffalo, which are based on the draft 802.11g specification. The standard was expected to be finalized by IEEE around mid to late 2003. 802.11g operates in the 2.4-GHz waveband, the same as the 802.11b standard. If 802.11g becomes available, its advantage is that it offers some degree of backward compatibility with the existing 802.11b standard.
Potential users must be aware that any equipment installed before a final standard is ratified may not conform to the final standard. Organizations are advised to gain the necessary assurances from their supplier or a technical authority, and it is recommended that they seek up-to-date advice on the current licensing situation before making any financial commitment.
IEEE 802.11h
This is a modification of 802.11a being developed to comply with European regulations governing the 5-GHz frequency. 802.11h includes Transmit Power Control (TPC) to limit transmission power and Dynamic Frequency Selection (DFS) to protect sensitive frequencies. These changes protect the security of military and satellite radar networks sharing some of this waveband. It is likely that if 802.11h equipment meets with approval, current regulations will be reviewed, and 802.11h may supersede 802.11a. This may mean that no new 802.11a equipment could be installed and used, and existing equipment could be used only if no changes are made to the network.
7.1.6 Bluetooth and Wireless Personal Area Networks
Bluetooth-enabled devices allow creation of point-to-point or multipoint Wireless Personal Area Networks (WPANs) or "piconets" on an ad hoc or as-needed basis. Bluetooth is intended to provide a flexible network topology, low energy consumption, robust data capacity, and high-quality voice transmission. Bluetooth is a low-cost radio solution that can provide links between devices at distances of up to 10 meters. Bluetooth has access speeds of 1 Mbps, considerably slower than the various 802.11 standards; however, the Bluetooth chips required to connect to the WLAN are considerably cheaper and have lower power requirements. Bluetooth technology is embedded in a wide range of devices. The Bluetooth wireless transport specification is meant to be used for bridging mobile computing devices, fixed telecom, tethered LAN computing, and consumer equipment together using low-cost, miniaturized RF components. Transport of both data and voice is supported in Bluetooth. Originally, Bluetooth was envisioned as a methodology to connect cellular or PCS telephones to other devices without wires. Examples of these other applications include USB " dongles ," peripheral device connections, and PDA extensions.
Bluetooth, as a WPAN, should not be confused with a WLAN because it is not intended to do the same job. Bluetooth is primarily used as a wireless replacement for a cable to connect a handheld, mobile phone, MP3 player, printer, or digital camera to a PC or to each other, assuming the various devices are configured to share data. The Bluetooth standard is relatively complex; therefore, it is not always easy to determine if any two devices will communicate. Any device should be successfully tested before a purchase is made. Bluetooth is an open specification made available to Bluetooth SIG members on a royalty-free basis. More than 2,000 companies worldwide have declared interest in Bluetooth-enabled devices [1].
According to a recent article about Bluetooth gadgetry written by Will Knight [2], Ollie Whitehouse, a researcher based in the United Kingdom and employed by the computer security company @Stake, created an eaves-dropping tool to demonstrate just how vulnerable Bluetooth-enabled devices such as laptops, mobile phones, and handheld computers are to someone attempting to pilfer data from them. Whitehouse claimed his "Red Fang" program can be used in any setting where it is common to see users with mobile devices, such as while riding airplanes or trains or sitting in coffee shops . The Red Fang system can be used to scan these devices and determine if they are unprotected . Whitehouse sees his program as being similar to those used for "war-driving" activities (where people seek out poorly secured 802.11 wireless networks.) Ollie claims many people do not even know Bluetooth wireless technology is installed on their mobile devices, let alone the fact that the corresponding Bluetooth security settings are often turned off by default.
A report issued by research firm Gartner in September 2002 indicated that many people do not activate Bluetooth security features, and this inaction potentially exposes their devices to exploitation by hackers. Red Fang was unveiled in August 2003 at the Defcon computer security conference held in Las Vegas, Nevada. Bruce Potter, a security expert with U.S. think tank the Shmoo Group, improved the tool by making it more user friendly, according to Knight in his aforementioned article, which went on to state that "Potter expects Bluetooth security to become a growing concern, considering the high penetration of Bluetooth-enabled devices and the lack of knowledge about Bluetooth security in corporate security departments."
7.1.7 Ultra Wideband
UWB is a high-bandwidth (100 Mbps and up), short-range (less than 10 meters) specification for wireless connection designed to connect computers, or computers and consumer-electronics devices such as handheld and digital cameras , with the potential to become a high-bandwidth connection. There are some doubts that UWB equipment will become commercially available.
7.1.8 Security for WLANs
The IEEE is currently working on a new security standard for incorporation into 802.11a, 802.11b, and any new 802.11 standards that are approved for use, such as 802.11g. These enhancements, known as 802.11i, replace Wired Equivalent Privacy (WEP) encryption with a new, more secure security encryption protocol called Temporal Key Integrity Protocol (TKIP), Advanced Encryption Standard (AES), and 802.1 x authentication, and should be available sometime early in 2004 since NIST approved the draft standard on Sep 4, 2003. In the meantime, the WiFi Alliance announced an interim standard called WiFi Protected Access (WPA), which should go a substantial way toward correcting flaws with the 802.11i standard. WPA will not include AES, however.
Anyone with a compatible wireless device can detect the presence of a WLAN. If appropriate security mechanisms are put in place, this does not mean that the data can be accessed, however. The WLAN should be configured so that anyone trying to access the WLAN has at least the same access restrictions as they would if they sat down at a wired network workstation. All of the following suggestions are practical steps that can be put in place to improve WLAN security. A combination of methods can be selected to meet company needs.
Wired Equivalent Privacy
WLANs that adhere to the WiFi standard have a built-in security mechanism called WEP, an encryption protocol. When WLAN equipment is bought, WEP encryption is often turned off by default. In order to be effective, this security mechanism should be turned on. Originally, WEP encryption used a 40-bit or 64-bit encryption key and later a 128-bit key to increase security. All access devices must, however, be set to use the same encryption key in order to communicate. Using encryption will slow down the data transfer rate by up to 30 percent because it takes up some of the available bandwidth.
SSID
SSID is a method wireless networks use to identify or name an individual WLAN. Short for Service Set Identifier, the SSID is a 32-character unique identifier attached to the header of packets sent over a WLAN. This identifier acts as a device-level password when a mobile device tries to connect to the Basic Service Set (BSS). The SSID enables a differentiation from one WLAN to another. All access points and all devices attempting to connect to a specific WLAN must use the same SSID. A device is not permitted to join the BSS unless it can provide the unique SSID. Because an SSID can be sniffed in plain text from a packet, it does not supply any security to the network. Sometimes, the SSID is referred to as a Network Name. It is a good practice to change the default SSID (network name) and passwords when setting up an Access Point. Access Points may be factory-set to broadcast SSID data to allow users to configure access. This feature should be turned off. Here are some other tips to secure your WLAN:
-
Install personal firewall software on all connected PCs and laptops.
-
Utilize the Access Control List (ACL) that is standard in WLAN equipment. All devices have a unique MAC address; the ACL can deny access to any device not authorized to access the network.
-
Remove rogue unauthorized access points from the network.
-
Use password protection on all sensitive folders and files.
-
Avoid wireless accessibility outside buildings where it is not required; directional aerials can be obtained to restrict the signal to 180 or 90 degrees from the access point.
-
Switching off the power to the access point during off hours makes the WLAN unavailable at those times.
All WLAN systems should run on their own LAN segment, and a firewall should isolate them from the corporate LAN. Users wishing to access company databases through the wireless network should use a Virtual Private Network (VPN), encrypting all WLAN traffic and, thereby, protecting the system from hacking.
7.1.9 WLAN Performance
It is important to note that transmission speeds for all WLANs vary with file size , number of users, and distance from the access point. The performance of each standard varies considerably. 802.11b has a nominal data transfer of 11 Mbps, but in practice, the data rate is approximately 4 to 7 Mbps, depending on the equipment used. Performance figures vary depending on the number of users, the local environment, and any obstructions that are in the way. Buildings with many girders, thick walls, and concrete will often shorten the effective range, and there may be areas that are "dead zones." For that reason, it is always wise to try out a few different products to see how well they perform in your environment.
7.1.10 WLAN Implementation Concerns
Planning
To determine the location of access points, it is essential that a site survey be undertaken by a specialist in this area. A site survey will also determine the number of access points required to give the desired coverage, the range of each access point, and its channel designation. The access point, or the antenna that is attached to the access point, will usually be mounted high in a room; however, an access point may be mounted anywhere that is practical as long as the desired radio coverage is obtained. Larger spaces generally require more access points. Before a site survey is undertaken, it is advisable to prepare a floor plan to show where coverage is required. It is also essential that technical staff assist with the site survey. There may be a charge for the site survey, but the supplier will often refund the charge for the site survey if the equipment is subsequently purchased from them.
Capacity
Planning a wireless LAN should take into account the maximum number of people who will be using wireless devices in the range of any access point. The recommended number of devices accessing each access point is 15 to 20. Where light usage of the network occurs, such as with Web browsing or accessing applications that require little exchange of data, this could rise to around 30 users. It is relatively easy to scale wireless LANs by adding more access points, but for an 802.11b network, no more than three access points may operate in any one coverage area because of frequency congestion. An 802.11a network can operate up to eight access points in one area, each using a different channel.
With single-story facilities, the access points will usually be spread far apart, making channel assignment relatively straightforward. You can easily use a drawing to identify the position of your access points in relation to each other and assign each access point to a channel. The key with a larger 802.11b network is to make sure channels are assigned in a way that minimizes the overlap of signals. If access points will be located on multiple floors, then the task is slightly more difficult because planning will need to be done three-dimensionally.
Performance
Each 802.11b access point can potentially be accessed from up to 350 meters away outdoors. This distance is very much reduced indoors, the maximum distance attainable in ideal conditions being 100 meters. The range depends on the extent to which the radio signal is dissipated by transmission through walls and other obstructions and interference from reflection. The amount of data carried by a WLAN also falls as the distance increases; as signal strength becomes reduced, data rate reductions from 11 Mbps to 5.5, 2, or 1 Mbps will automatically occur in order to maintain the connection. It is possible that there may be issues of interference when using a 802.11b WLAN and where there are devices with Bluetooth connectivity, such as handheld devices and mobile phones, in the same area.
Post-installation coverage and performance may also vary as a result of building work, metal storage cabinets introduced into the coverage area, or other obstructions or reflectors that are moved or introduced. Microwave ovens and fish tanks have also been known to affect the performance of 802.11b networks. In the case of microwave ovens, they use the same frequency band as WLANs. If a different standard is implemented after installation of an existing 802.11b wireless network, a further site survey may be required because the coverage is likely to be different when compared to 802.11b. More access points may be required to maintain or improve data rates.
Power Consumption
The power output of 802.11a access points is limited, and the range from each access point may vary depending on the specific frequency used within the 5-GHz spectrum. Wireless cards typically have several different settings related to their power usage. For example, standby mode, where the transmission of data occurs only when required, uses relatively little power and leads to improved battery performance. This works similarly to a mobile phone that only connects to a network when making or receiving a call. Wireless cards that have recently come to market tend to consume less power. This trend is expected to continue as newer generations of cards become available.
Power over Ethernet
Access points require a power supply in addition to a wired network connection. Access points are often sited high on walls and away from existing power outlets. Some products on the market will supply power to the access point via the network cable, removing the need to install additional power cabling.
EAN: 2147483647
Pages: 153