6.3 RADIUSTACACS
|
6.3 RADIUS/TACACS+
A discussion of access controls would be remiss without some discussion of one of the most popular access control systems of all time, the Remote Authentication Dial-In User Service (RADIUS), and its close cousin, Terminal Access Controller Access Control System (fortunately, commonly referred to as just TACACS+ [1]). Each of these is a centralized access control mechanism.
You do not need to have a very large network to understand the advantages of centralized access control. Imagine the following scenario, which may be common on even a small network. You have access control as part of the network operating system that controls users' ability to access network resources while locally logged on to the network. You also maintain a small modem bank and a remote access server that manages user connections over the modem bank. Finally, in an effort to reduce the costs associated with the modem bank and toll-free telephone calls, you have a separate remote access server that manages VPN connections incoming from your wide area network. Each of these three devices can require a separate user database along with associated permissions for network access. This implies that each user addition, removal, or change must be replicated in at least three locations. Not only is this a pain from an administrative point of view, but it is also detrimental to the overall security of a network. Complexity leads to mistakes and oversights on the part of network administrators. These mistakes may provide the vulnerability that a threat can utilize to gain access to your network.
Instead, the preferred solution is to centralize the access control mechanisms. RADIUS and TACACS+ are two systems that will accomplish just this for your network and they are both available as free services for your network or as bundled services in other operating systems or remote access controls. While commonly referred to as a service, RADIUS and TACACS+ are technically protocols that provide for the authentication, authorization, and various levels of accounting for users logging on to the network. Because the protocols are very similar, the remainder of this discussion will focus primarily on RADIUS, with attention paid to TACACS+ when it differs significantly from the RADIUS standard.
RADIUS was originally developed by Livingston labs and has since moved into the realm of free software. Many free implementations of RADIUS are available for downloading. TACACS+ started out as the TACACS protocol and was extended by Cisco to the current version. Originally tightly controlled by Cisco, TACACS+ implementations are also available free of charge. The historical difference between RADIUS and TACACS+ ownership and cost is what caused many ISPs to implement RADIUS as the access control mechanism of choice and, to date, RADIUS maintains its position as the more often deployed protocol of the two.
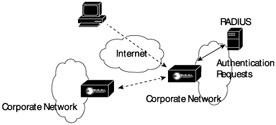
Like most TCP/IP protocols, RADIUS is a client/server protocol with the exception that RADIUS protocol is not found on user hosts. Instead, it is a protocol that operates between a remote access server (RAS) and a RADIUS server. Exhibit 1 shows the common implementation of RADIUS into the network. When a user attempts to log in to the network via a remote access server, the RAS sends a RADIUS packet to the RADIUS server with the username and the encrypted user password. The fact that only the password is encrypted is a concern to some. While the password is certainly the most important element of the packet, there is a great deal of other interesting information available to someone who manages to capture the packet over the network. Most significantly is the username itself. Because so many users tend to pick poor passwords, knowing the username allows someone to start making educated guesses about the password itself. This information is only ever transmitted between the remote access server and the RADIUS server. Whether or not this is a significant threat depends on your security needs.
Exhibit 1: Sample RADIUS Implementation
TACACS+ addresses the issue of unencrypted data of a RADIUS exchanges by encrypting the entire packet. Thus, someone capturing a TACACS+ packet will only see that a TACACS+ transaction has occurred, not who has logged in.
The primary advantage of centralized AAA servers such as RADIUS and TACACS+ is that user management is centralized. Instead of having to maintain user databases and access permissions on multiple RAS devices and other authentication points, network administrators are able to maintain that information in a single location and configure all other devices that perform authentication to query that central user database. With RADIUS and TACACS+, network administrators can maintain this user database on their own LAN and authenticate users company wide.
[1]There are actually three versions of TACACS. The most recent and commonly employed is TACACS "Plus," thus the "+" symbol after the acronym. The versions are not compatible with each other.
|
EAN: 2147483647
Pages: 119