Monitoring and Auditing IIS
|
| < Day Day Up > |
|
You will need to track what the users are doing on the IIS server to be truly secure. You will use the information to verify that there are no security problems with the website and to build a case if you have been successfully attacked. You will then be able to determine the extent of the damage and may be able to recover more quickly. You can track what users do by configuring protocol logging and audit policies.
Design Scenario: Designing an Authentication Strategy with RADIUS
Wonder, Inc. wants Elektronics R Us, its partner organization, to maintain the accounts of its own employees that will authenticate with the website. Wonder needs a mechanism to forward requests to authenticate to Elektronics R Us and receive validation as to whether the employee will have access to the content. The folks at Wonder are concerned about security and require that the solution support auditing.
-
Question: What technology should Wonder, Inc. implement? Answer: Wonder would use IAS, which is Microsoft’s RADIUS. This will allow Wonder, Inc. to authenticate, authorize, and audit access by Elektronics R Us employees without having to maintain their accounts.
Configuring IIS Protocol Logging
You can track each request of the underlying protocol to the server by enabling IIS protocol logging on the service’s virtual server. You can use this information to track the user’s activities or to determine what an attack affected.
You will need to make sure that this is secure to prevent an attacker from manipulating or deleting the files to cover their tracks.
You can enable logging by checking the Enable Logging check box on the Web Site tab of the website’s Properties dialog box, as shown in Figure 7.6.
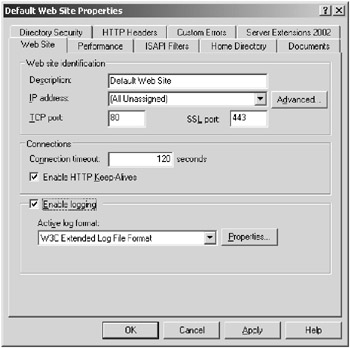
Figure 7.6: Enabling logging through the Web Site tab
You have the option of choosing the following from the Active Log Format drop-down box:
-
Microsoft IIS Log File Format
-
NCSA Common Log File Format
-
W3C Extended Log File Format
-
ODBC Logging
You would choose the NCSA log file format to be compliant with engines that parse and report with this file format. The NCSA web server was the first successful web server, and its log file format was used as the basis for many reporting tools. The World Wide Web Consortium (W3C) extended the NCSA log file format to allow you to include additional information in the log file which is called the W3C extended log file format. This format is the more popular choice for local logging now. You can choose the items you want to log on the Advanced tab for the log format, as seen in Figure 7.7.
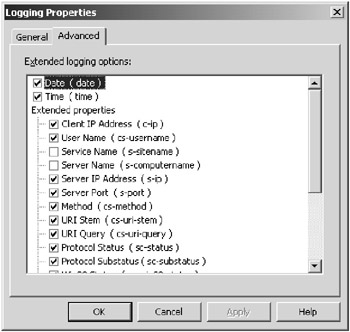
Figure 7.7: The Advanced tab of the Logging Properties dialog box is where you can configure additional information to log.
You should consider enabling logging of the following items when choosing the W3C Extended log file format:
-
Client IP Address (c-ip)
-
User Name (cs-username)
-
Method (cs-method)
-
URI Stem (cs-uri-stem)
-
Protocol Status (sc-status)
-
Win32 Status (sc-win32-status)
-
User Agent (cs(user-agent))
| Note | The Win32 Status is useful for debugging security problems. An error code of 5 indicates that access is denied. You can run helpmsg errNum on the command line, where errNum is the error number in the Win32 Status field. |
You should consider adding the following items in a multiserver environment to track what server the information came from because you will typically run scripts that will combine the log files into a single database to report on them:
-
Server IP Address (s-ip)
-
Server Port (s-port)
ODBC Logging allows you to log directly to an ODBC data source like SQL Server 2000. This can save you the step of moving the text-based log formats discussed earlier into a database server. You will log directly to the database at the cost of performance, which may be an issue if you host many websites or one busy site.
The Microsoft IIS Log File Format is a format that was introduced by Microsoft when they released IIS. It is not a popular log file format and few tools even support the log file format. You will only need to support this format if there is a reporting tool that requires it.
You can create a separate log for each website on your server. The logs will track what was viewed on the site, when it was viewed, and who viewed it. You could give website administrators access to their websites’ log files. IIS log files are only available to individuals in the Local Administrators group. The owner of the log directory and files must be in the Local Administrators group or IIS will log an error to the system event log.
| Note | Some IIS servers may need to host hundreds of websites and logging can be degraded. You can improve performance by enabling centralized binary logging. All server activity is written to a single log file in a binary log file format. This will reduce the number of logs and, therefore, writes to the disk drive, increasing the performance. This makes logging feasible for large hosting sites. You can enable binary logging by setting the W3SVC/CentralBinaryLoggingEnabled metabase property to True and then restarting the web service. |
HTTP.sys Logging
In addition to protocol logging, you can enable HTTP.sys logging. You may remember that HTTP.sys is the new kernel mode driver for IIS 6.0 and is responsible for parsing each incoming HTTP request to the IIS server and submitting it to the proper queue for the application. Since it sees every request for your web server, HTTP.sys is responsible for logging web traffic if you have enabled logging for your website. HTTP.sys only logs web traffic, not FTP, SMTP, NNTP, or other traffic, which is handled by the inetinfo.exe process. HTTP.sys logging guarantees that the request is logged if you are experiencing a denial of service attack, or if a malformed request (whether malicious or unintentional) is causing your web applications to fail. After all, if the application fails it may not log this information. But there are times when HTTP.sys has had a problem and the standard logging function will not work. It will then create a file called httperr.log in the System32\logfiles directory and log the requests. If your whole web server hung, you should inspect this file for malformed requests or other information that may help you determine the problem.
Configuring Audit Policies
When security professionals refer to a secure implementation of a server, they call it hardened, not secure. This is because you can never be sure that the server is totally secure; you have to assume that the security measures can be overcome. If the server is compromised, or even if someone is attempting to compromise it, you would like to know. You can track what users are failing to do or successfully doing with the server through audit policies and logging.
You will need to set up an audit policy to track security events like access to files or authentication attempts with the server. This information will be written to the Windows security log, which can be viewed with Event Viewer. You can use this information to determine what is going on with the server and where your security mechanisms may be breaking down. However, if you audit everything, you will be overwhelmed with information and will more than likely miss seeing patterns in the logs, not to mention the performance issues this will cause on the server or the security log filling up quickly. You will need to determine what you should audit.
You should configure an audit policy to track the logon and logoff of sensitive accounts like administrators and server operators, but this could also include individuals that have high levels of access to applications, like database administrators.
You should also enable the Audit Object Access policy so that you can track access to sensitive files and data or access to the Registry. In fact, you can use Audit Object Access to track access to any kind of object in Windows. For example, you can track the use or attempted use of files, folders, Registry keys, or printers. You will not cause any events to be audited by just turning on the Audit Object Access setting. You will need to enable auditing on the individual resource for events to be generated when the object access is successful or failed. The Success setting will generate an event whenever the object is successfully accessed. The Failure setting will generate an event whenever someone tries to access the object but fails due to the security settings. You would enable the Global Audit setting, and then on each resource, you would configure the information that you want to audit. You can set detailed events to control whether you want to audit just reads or writes to the resource.
For example, you can use the Write And Append Data Auditing on website files to track changes to the web pages. This could notify you that your site is being compromised.
You should also track changes to the audit policy, which could be an indication that someone is trying to cover their tracks.
You will need to use the business and security requirements to determine what the audit policy will be for your environment. You can set the audit policy by using the Audit Policy node in the Domain Security Policy MMC or in the Local Security Policy MMC if the server is not a member of the domain. You can generally choose to audit the success or failed use of a right or access to a resource. The Audit Policy settings are located in Security Settings\Local Policies\ Audit Policy of the server, as seen in Figure 7.8.
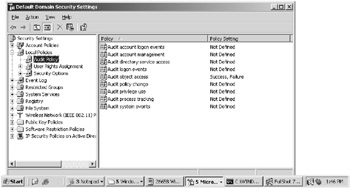
Figure 7.8: Configuring the audit policy
In the Design Scenario “Designing a Monitoring and Auditing Strategy for IIS,” you will design an auditing strategy for IIS.
Design Scenario: Designing a Monitoring and Auditing Strategy for IIS
Wonder, Inc. has installed its web server to host its e-commerce site and is concerned about an attacker trying to gain access to its website. The folks at Wonder have taken measures to harden their server by configuring and verifying the NTFS permissions on the site, installing the minimum amount of services, and keeping the server up-to-date. They know that there may still be a security incident and are worried about how they will detect it.
-
Question: You need to come up with a strategy for detecting a security incident that will alleviate the CIO’s concerns. What should you do to help detect a security incident? Answer: You should plan on creating an audit policy for the server that will trac k object access, user authentication, and changes to the audit policy itself. You should also enable protocol logging on the IIS protocols that you are using.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 168
- Structures, Processes and Relational Mechanisms for IT Governance
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governance in IT Outsourcing Partnerships
- The Evolution of IT Governance at NB Power
- Governance Structures for IT in the Health Care Industry