Description of the Iris Algorithm
| < Day Day Up > |
| Now that we know what constitutes the iris biometric, and how it can be captured, we need to know how the algorithm works. Once an iris is captured, it is then converted into a template that is 2,048 bits in length. To compare a live template to the reference template, a simple exclusive OR (XOR) operation is done on the two values. Their corresponding mask bit vectors are used in an AND operation to verify that there were no artifacts affecting the comparison. The norms of the resulting XOR and AND operations are used to compute a Hamming Distance. [3] The Hamming Distance is a measure of dissimilarity between the two iris templates. This distance is then used to determine whether there is a match or not. Since there are many degrees of freedom in the iris code, a relatively large Hamming Distance can be used to still guarantee a near-zero FAR. This simplicity of the algorithm allows for very fast matching in the range of 100,000 per second on a 300MHz machine.
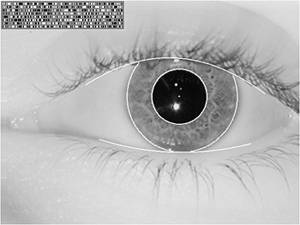
Figure 8-1 illustrates a sample of iris templating and the resulting iris code is shown in the top left of the image. Figure 8-1. Sample of iris templating and resulting iris code. |
| < Day Day Up > |
EAN: 2147483647
Pages: 123