28.2 Building an IP Network
| |
The first step toward building an IP-based network is to select a particular class of network addresses. For this you need to know or estimate how many hosts will be included in your network. When deciding on the number of hosts, you should also keep in mind future expansion of the network. Based on the number of hosts , you can decide which class of network addresses should be used.
If you don't plan to connect your network to any public network such as the Internet, you can select any network address for your network. If you want to connect the network to the Internet, you must get a range of IP addresses from your Internet service provider or from the address assignment organization for your geographic location. These organizations are listed below according to geographic region.
For North and South America
American Registry for Internet Numbers
ARIN
4506 Daly Drive, Suite 200
Chantilly, VA 20151
Phone Number: +1-703-227-0660
Fax Number: +1-703-227-0676
E-Mail: hostmaster@arin.net
WWW: http://www.arin.net
For Asia Pacific Region
Asia Pacific Network Information Center
APNIC
Level 1, 33 Park Road
P.O. Box 2131
Milton, QLD 4064
Australia
Phone Number: +61-7-3367-0490
Fax Number: +61-7-3367-0482
E-Mail: hostmaster@apnic.net
WWW: http://www.apnic.net
For Europe
Rseaux IP Europens
RIPE NCC
Singel 258
1016 AB Amsterdam
The Netherlands
Phone Number: +31-20-535-4444
Fax Number: +31-20-535-4445
E-Mail: hostmaster@ripe.net
WWW: http://www.ripe.net
Even if you don't want to connect your network with the Internet at the present time, it is better to get a network address from one of these organizations so that when you decide to have an Internet connection, you won't need to make any changes to the network.
Assigning IP Addresses
After selecting a network class and getting a network number, you can assign IP addresses to individual hosts. When assigning IP addresses, keep the following considerations in mind.
-
The first IP address (the smallest IP address) in your network is the network number or network address. This is also called a generic network address. Don't assign this address to any host. For example, if you are using a class C network address 192.168.4, don't assign IP address 192.168.4.0 to any host.
-
The last IP address in your network (the largest IP address in a network) is the broadcast address. This should not be assigned to any host. All hosts in the network receive any data packet sent to this IP address. In the above example, 192.168.4.255 is the broadcast address.
-
You should reserve the first working IP address in your network for the router. This is not mandatory but it makes it easy to remember the router address and is a general convention. In the above example, 192.168.4.1 should be reserved for the router.
-
You should also devise an IP address assignment scheme to ensure that no IP addresses are duplicated in your network.
-
If a host has multiple network interface adapters, a unique IP address must be assigned to each one.
-
Multiple IP addresses can be assigned to a single network interface adapter.
-
IP address 127.0.0.1 is a special address known as the loopback address. It is used for test purposes. A data packet sent at this address is received by the host itself.
Netmasks and Subnetting
A netmask is used to separate the network and host parts of an IP address. It consists of a continuous sequence of 1s equal to the number of bits in the network part of an IP address. After that, a sequence of 0s equal to the number of bits in the host part is present. For example, class C networks consist of 24 bits in the network part and 8 bits in the host part. A netmask for class C networks consists of twenty-four 1s and eight 0s. Thus the netmask for all class C networks (if these are not subnetted ) is always 255.255.255.0 (11111111111111111111111100000000). Similarly, the netmask for class B networks is 255.255.0.0, and the netmask for class A networks is 255.0.0.0. The netmask is the same for all hosts in a network.
A netmask plays an important role in subnetting. Subnetting is a process in which a network is broken into smaller networks. For example, if you have only one class C network address space and want to set up two networks of 20 hosts each, you can break the class C network into a number of smaller networks. A class C network consists of 256 IP addresses (including generic network and broadcast addresses) in total. This can be broken into four subnetworks of 64 IP addresses each with the help of netmasks. This is accomplished by using 26 bits in the network part of an IP address and 6 bits in the host part of an IP address. In this case, the netmask will contain twenty-six 1s and six 0s resulting in 255.255.255.192 (11111111111111111111111111000000). The generic network addresses and broadcast addresses are shown in Table 28-2. The class C network used in this example is 192.168.4.0.
Table 28-2. Dividing a Class C Network into Four Networks
| Network Address | Netmask | Broadcast Address | Range of Host Addresses |
|---|---|---|---|
| 192.168.4.0 | 255.255.255.192 | 192.168.4.63 | 192.168.4.1 192.168.4.62 |
| 192.168.4.64 | 255.255.255.192 | 192.168.4.127 | 192.168.4.65 192.168.4.126 |
| 192.168.4.128 | 255.255.255.192 | 192.168.4.191 | 192.168.4.129 192.168.4.190 |
| 192.168.4.192 | 255.255.255.192 | 192.168.4.255 | 192.168.4.193 192.168.4.254 |
Using the same subnetting technique, class A and class B networks can also be divided into smaller networks. Netmasks also play an important role in data routing.
IP Routes
When two or more IP networks are connected with the help of routers, IP routes are defined that are used to send data through a specific router when the source and destination hosts are not present on the same network. Figure 28-5 shows a scenario where three networks are attached to each other using three routers. A fourth router connects these three networks to the Internet.
Figure 28-5. Use of routers in IP networks.
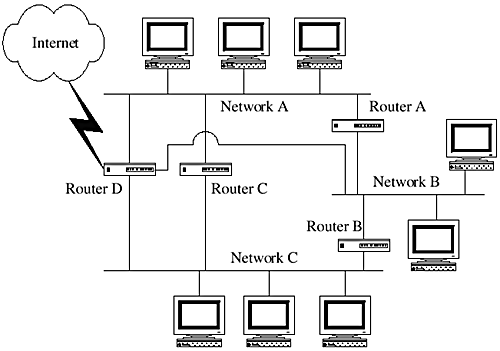
Networks A and B are connected together with the help of router A. Networks B and C are connected together with the help of router B. Networks A and C are connected using router C. All of these three networks are connected to router D, which is also connected to the Internet.
Multiple routes are defined in each network. For example, hosts in network A have a route defined to network B that passes through router A. They also have a route defined to network C, that passes through router C. Similarly, the other two networks have their own route definitions.
DEFAULT ROUTE
Router D in Figure 28-5 is connected to all three networks and the Internet. If the destination address does not lie in any of these three networks, the data packet is sent to router D, which acts as a default route. The default route is used as a last resort in the routing process to send a data packet. It is the responsibility of the default router to determine where a packet should go if the destination address is not present in any of the local network addresses. Router D is also responsible for distributing incoming data packets from the Internet among these three networks.
ROUTING PROCESS
When a host wants to send a data packet, the network layer checks the destination IP address for the routing information. If the destination host is in the same network as the sending host, the data packet is sent directly to the destination host without involvement of a router. In case the destination host is not on the local network, other defined routes are tried. If a route is found, the data packet is forwarded to a specific router depending on the destination address. The router then forwards the data packet to the destination host. In case no defined route is found for the destination address, the packet is forwarded to the router acting as default gateway using the default route. It is then the responsibility of this router to deliver the data packet to the destination host with the help of its own routing method.
ROUTING PROTOCOLS
Static routes are defined by the network administrator and remain fixed. Dynamic routes are calculated in real time and keep changing depending on network conditions. Different routing protocols are used for calculating dynamic routes. HP-UX supports the most commonly used routing protocols.
-
Routing Information Protocol (RIP)
-
Open Shortest Path First Protocol (OSPF)
-
Border Gateway Protocol (BGP)
-
Exterior Gateway Protocol (EGP)
Address Resolution Protocol
IP addresses are used at the network layer. These are the logical addresses used for hosts connected to a network. At the network layer level, the data packets contain source and destination IP addresses. However, at the physical and data link layer level, hosts recognize each other with physical (MAC) addresses instead of IP addresses. When the data reach the data link layer on the sending host, the host must know the physical addresses of the receiving host in addition to the destination IP address. A special protocol known as Address Resolution Protocol (ARP) is used for this purpose. The address resolution protocol may be thought of as a function that takes the destination of the IP address as input and gives the destination MAC address as its output.
ARP uses a broadcast mechanism to determine the MAC address of the destination host. It sends a broadcast data packet on the network asking the identity (MAC address) of the host who is assigned the destination IP address. The request is like the following.
"Send me your MAC address if you have this IP address, " where "this IP address" is the IP address of the destination host. Every host on the network listens to this request and only that host responds whose IP address matches the destination IP address.
The HP-UX kernel maintains a special data structure in memory known as the ARP cache, which contains a mapping of IP addresses to MAC addresses. When ARP successfully resolves an IP address, its entry is added into the ARP cache and remains in the table for 10 minutes.
HP-UX provides the arp command, which is used to display and manage the contents of the ARP cache. The following command displays the contents of the ARP cache.
# arp -a 192.168.3.45 (192.168.3.45) at 0:10:83:36:d1:dc ether 192.168.3.10 (192.168.3.10) at 0:60:b0:59:fe:99 ether 192.168.3.17 (192.168.3.17) at 0:60:83:2:50:20 ether # In addition to displaying ARP cache contents, the arp command can be used to add and delete ARP entries manually.
Study BreakAdding Entries to the ARP Cache
|
Reverse Address Resolution Protocol (RARP)
In some cases, you need the reverse process of the ARP. You already know the MAC address and want to find out the IP address corresponding to that MAC address. One example of this situation is a diskless client. A diskless client does know its MAC address at boot time, but due to nonavailability of disk files, it is unaware of its IP address. Just after the boot process, it contacts a BootP or DHCP server using the Reverse Address Resolution Protocol (RARP) and asks it to provide the IP address corresponding to its MAC address. A BootP or DHCP server provides the IP address to the client after receiving the request. An HP-UX machine can be configured as an RARP server.
Internet Control Message Protocol
The Internet Control Message Protocol (ICMP) is used for network monitoring and troubleshooting purposes. ICMP uses data packets to convey information about the status of the network, such as network congestion and network unreachable conditions. The common use of ICMP is the ping command. Using this command, you send a data packet to a host to check if the host is alive. When the receiving host receives this data packet, it returns it to the sending host. If you then receive the data packet, you know that the host is alive . In the other case, it is assumed that the host is dead or can't communicate on the network. The returned data packet also contains time information that shows the time taken by the data packet in the round trip. The simplest form of the ping command is shown here. To stop the command, use the ![]() key combination.
key combination.
# ping 192.168.3.13 PING 192.168.3.13: 64 byte packets 64 bytes from 192.168.3.13: icmp_seq=0. time=2. ms 64 bytes from 192.168.3.13: icmp_seq=1. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=2. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=3. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=4. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=5. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=6. time=0. ms 64 bytes from 192.168.3.13: icmp_seq=7. time=0. ms ----192.168.3.13 PING Statistics---- 8 packets transmitted, 8 packets received, 0% packet loss round-trip (ms) min/avg/max = 0/0/2 # By default, the data packet size of the ICMP packet used by the ping command is 64 bytes. You can change the data packet size to check delivery of large packets on the network. The following command uses a data packet size of 20,000 bytes. Note that the larger the data packet size, the more time it takes to process them.
# ping 192.168.3.13 20000 PING 192.168.3.13: 20000 byte packets 20000 bytes from 192.168.3.13: icmp_seq=0. time=10. ms 20000 bytes from 192.168.3.13: icmp_seq=1. time=9. ms 20000 bytes from 192.168.3.13: icmp_seq=2. time=9. ms 20000 bytes from 192.168.3.13: icmp_seq=3. time=9. ms ----192.168.3.13 PING Statistics---- 4 packets transmitted, 4 packets received, 0% packet loss round-trip (ms) min/avg/max = 9/9/10 # | |
| |
| Top |
EAN: 2147483647
Pages: 390