Understanding Permissions
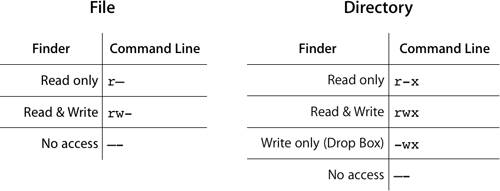
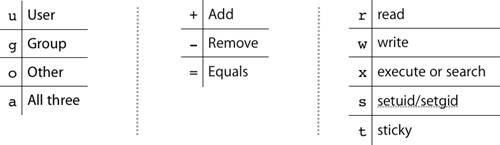
| On Mac OS X and other UNIX-based operating systems, files and folders have an attribute known as the file permission mode. This mode determines how the file's owner, group, and others may access the file. You can view the mode in a long ls listing. For example: % ls -l lrwxr-xr-x 1 david david 5 7 Jan 09:57 DirLink -> MyDir lrwxr-xr-x 1 david david 6 7 Jan 09:57 FileLink -> MyFile drwxr-xr-x 2 david david 68 7 Jan 09:56 MyDir -rw-r--r-- 1 david david 6 7 Jan 09:57 MyFile -rw-rw-r-- 1 david david 498 7 Jan 09:58 NewFile -rwxr-xr-x 1 david david 369 7 Jan 09:59 Script In a long ls listing, the leftmost character indicates the type of file: d for directory or folder, l for symbolic link, and - for a regular file. The next nine characters represent the file mode, which consists of three sets of three bits. The three sets correspond with Owner, Group, and Other permissions. The three bits in each set correspond with read (r), write (w), and execute (x) permission. A hyphen (-) replaces the r, w, or x character for permissions that are not set. The following figure shows the correspondence between the information you see in the Finder's Get Info window and the information you see in a long ls listing. 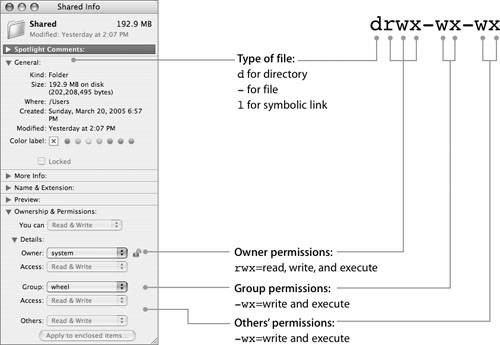 The Finder's Get Info window enables you to choose from three types of access permission on a file and four on a folder. The figure shows the available Finder permission choices and how they appear at the command line. Note that the Finder automatically sets x permission on a folder whenever you choose "Read only," "Read & Write," or "Write only" from the Finder. If you use the command line to set permissions, other permission combinations are available. Note Copying files using the Finder may change their permissions, as viewed from the command line. When you create a new file from the command line on Mac OS X, the file's group is set to the group of the parent folder, even if the user who creates the file is not a member of that group. In some versions of UNIX, a file's group is set to the group of the user who creates the file. Setting Permissions With chmodYou use the chmod (change mode) command to set the permission mode from the command line. Because "owner" and "other" both begin with the letter o, you use u (user) for owner permission. The symbolic mode argument shown in the following figure consists of three characters, one from each table. You will learn about the setUID, setGID, and sticky bits later in this lesson. You will also learn about numeric and absolute arguments to the chmod command. Why Set or Clear x Permission?There are three cases in which you might find it useful to set or clear the x permission from the command line. You can:
To grant or deny program execution, set or clear the x permission: student17$ ls -l Ascript; ./Ascript -rwxr--r-- 1 david david 29 14 Jan 11:15 Script bash: ./AScript: Permission denied To deny long but grant short directory listing, set r and clear x permission: student17 $ ls -ld ADir; ls -l ADir drwxrw-r-- 3 david david 102 27 Jan 18:48 ADir ls: Information.txt: Permission denied To deny directory listing but grant file access by name, clear r and set x permission: student17$ ls -ld ADir; ls ADir; cat ADir/Docz.txt drwx--x--x 4 david david 106 28 Jan 14:42 ADir ls: ADir: Permission denied This is the contents of Docz.txt. Grant or Deny x Permission on a FileTo execute a program or shell script, you must have both r and x permission to it. When a programmer creates an application or command-line utility, the software that builds the program sets x permission automatically. When you create a script, you must set x permission on it with the chmod command. As an administrator, you can deny x permission to restrict execution of a command to the file's owner or group. For example: david$ ls -l shutdown -r-sr-xr-- 1 root operator 20636 16 Nov 09:19 shutdown david$ /sbin/shutdown /sbin/shutdown: Permission denied. Deny x and Grant r Permission on a FolderExecute permission on a folder is sometimes called search permission. Without search permission, you cannot perform a long listing of the folder's contents. You can perform a short ls listing (as long as you have r permission to the folder), so you can view the filenames and copy the files. As an administrator, you can prevent users from seeing the other information fields in the long listing by denying x permission. For example: david$ ls -ld modetest drwxrw-r-- 3 root david 102 27 Oct 48 12:20 modetest david$ ls modetest Information.txt david$ ls -l modetest ls: Information.txt: Permission denied Grant x and Deny r Permission on a FolderA user who has x but not r permission on a folder cannot display the contents of that folder at all. The user can, however, access a file in that folder by name (if the user has r permission to the file). This might be useful when an administrator wants to provide quick selective access to a file, without changing permissions on server folders, as opposed to a long-term strategy for providing selective access to files. Granting x and denying r on a folder can be useful when you want to make a file available to a limited set of usersfor example, to limit file access over FTP. Users who know the name of the file can get it, but other users cannot see the name in a folder listing. For example:
Controlling File Deletion From a FolderUsers need write permission to a folder in order to add, delete, or rename a file. By denying w permission to a folder, you can prevent users from deleting files or adding files. If you grant a user w permission to a folder:
Using the Sticky BitWhat if you want finer control than just one owner of a folder being able to delete everything? How do you allow users to add files to a folder, but prevent users from deleting each other's files from the folder? You set the sticky bit on the folder using chmod: $ chmod +t MyDir $ ls -ld MyDir drwxrwxrwt 3 david david 102 Oct 28 16:27 MyDir/ Note You omit the u, g, and o when you set the sticky bit. In the following example, user david owns a folder with the sticky bit set. Owner, group, and other all have rwx permission. User laura cannot delete user david's file. laura$ ls -ld nodeldir drwxrwxrwt 3 david david 102 28 Oct 16:27 nodeldir/ laura$ rm nodeldir/efile override rw-r--r-- david/david for nodeldir/efile? y rm: nodeldir/lfile: Operation not permitted A user can remove or rename a file in a folder with the sticky bit set only if both of these statements are true:
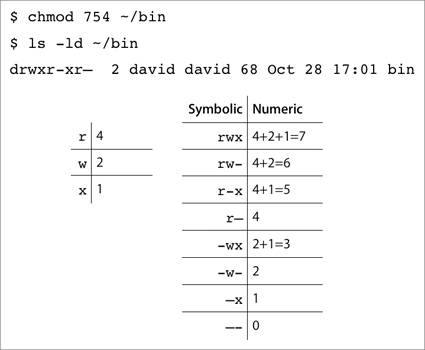
Note that the sticky bit does not prevent a user from changing or overwriting another user's file. A user who has write permission to a file can change the contents of that file, even if the sticky bit is set on the folder. To prevent overwriting, users must deny write access to group and other on files they create. Note On some versions of UNIX, new folders inherit the sticky bit from their parent folder. This is not true on Darwin/Mac OS X. Starting a Process As a Different UserWhen a program has the setUID (set user ID on execution) bit set, that program always executes with the user ID of the owner of the file, regardless of who actually executes the program. In a long ls listing, a file with the setUID bit set has an s in place of an x in the owner (user) permissions. A program with the setGID (set group ID on execution) bit set executes with the group ID of the file's group. In a long ls listing, a file with the setGID bit set has an s in place of an x in the group permissions. In early UNIX, someone added a feature to mail so users could mail a file, but that person forgot that mail ran setUID to root. As a result, you could read any file, regardless of its permissions, by mailing it to yourself! Modern programming techniques for eliminating flaws in setUID programs include privilege bracketing: Programmers use a system call to make some sections of the code run as root and other sections run as an unprivileged user.  The setUID and setGID bits are important because some commands installed on your computer must run with the user or group ID of an administrator in order to perform their function. For example, the passwd command must execute as root to modify your user information when you change your password. Note If a program is installed with the setUID or setGID bit set, do not clear it! If a program that runs as root contains a security flaw, a malicious user might be able to obtain root access to a computer by exploiting that flaw. Programmers try to eliminate vulnerabilities, but they don't always succeed. You can find examples of setUID-related security vulnerabilities by searching for setUID on the CERT webpage, www.cert.org. Mac OS X does not honor the setUID or setGID bit on shell scripts. Warning Utilities on your computer rely on file permissions to prevent users from causing inadvertent or malicious damage. To avoid exposing your computer to malicious or inadvertent damage, do not set the setUID or setGID bit on utilities installed on your computer. Set the SetUID and SetGID BitsYou set the setUID bit using the command chmod u+s filename. Clear the setUID bit using the command chmod u-s filename. Use g in place of u to set and clear the setGID bit. A long ls listing shows the letter s in place of x in the owner bits for setUID. For example: -rwsr-xr-x 1 david david 60 20 Nov 17:52 myprogram A long ls listing shows the letter s in place of x in the group bits for setUID. For example: -rwxr-sr-x 1 david david 60 20 Nov 17:52 myprogram Using Numeric Arguments to chmodYou can set the mode of a file or folder by using numeric arguments to chmod. Numeric arguments enable you to set exactly the mode you want with just one command. Note Don't recursively use chmod with numerical arguments on home directories. Use the textual method when you want to operate only on specific permissions categories (user, group, and other). The numerical method always sets all three categories, which is not appropriate for home directories. In the following figure, the first table shows that the r, w, and x bits correspond with the values 4, 2, and 1. The second table shows the value of each triplet. You can set the sticky bit on a folder by adding 1000 to the mode. For example, $ chmod 1755 mydir will set the permissions to -rwxr-xr-t 1 david david 68 Nov 20 20:28 mydir You can set the setUID bit by adding 4000 to the mode. For example, $ chmod 4755 myprog will set the permissions to -rwsr-xr-x 1 david david 102 Nov 20 20:28 myprog You can set the setGID bit by adding 2000 to the mode. Note Before you use numeric arguments to chmod, look at the current mode of the file or folder to be sure you do not inadvertently clear the sticky, setUID, or setGID bit. Setting Permission Policy Within the Session: umaskThe umask (user mask) masks the mode bits when you create a file or folder. The umask enables you to set a permission policy within a Terminal session. For folder creation, subtract the umask from a maximum of 777 to see what the folder creation mode will be. For file creation, subtract the umask from a maximum of 666 to see what the file creation mode will be. For example, when the umask is 022, folders are created with mode 755 (drwxr-xr-x), and files are created with mode 644 (-rw-r--r--). The umask command with no arguments lists the current umask. The default umask in Terminal is 022. Use the umask command to set the umask within a session. You can omit leading zeros, so 22 is equivalent to 022 and 2 is equivalent to 002. When the umask is 002, new folders you create have mode 775 (drwxrwxr-x), and new files have mode 664 (-rw-rw-r--). For example: $ umask 002 $ umask 2 $ echo Test > testfile $ mkdir testdir $ ls -l drwxrwxr-x 2 david david 68 28 Oct 17:06 testdir -rw-rw-r-- 1 david david 16 28 Oct 17:06 testfile When you set the umask in Terminal, it is effective only for the session in which it is set. You can set the umask for all of your Terminal sessions by setting the umask in your .profile, .login, or .cshrc files. Unfortunately, the defaults command uses decimal numbers, and umask values are octal numbers. To set a umask of 22, you would use the argument -int 18, not -int 22. As administrator, you can set a global, systemwide umask by adding an umask command to the script /etc/rc. The umask will apply to the Finder and other graphical user interface programs, as well as the Terminal interface. A user can set a per-user umask that applies to the Finder and other Utilities, as well as the Terminal interface, by using the defaults command. For example, defaults write -g NSUmask -int 2 will set the umask to 002. |
EAN: 2147483647
Pages: 258
- Chapter V Consumer Complaint Behavior in the Online Environment
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XII Web Design and E-Commerce
- Chapter XIV Product Catalog and Shopping Cart Effective Design