Using Network Security Mechanisms
| Network security mechanisms protect servers, facilitate packet filtering with firewalls, and enable the use of private addresses with NAT. VPN is another security mechanism that provides secure, encrypted remote access to an internal network from computers on the Internet. This section discusses these mechanisms. Network servers are valuable assets that should be protected with physical security and hardened (strengthened) against intrusions. To harden a server, you should enable only the services that you absolutely need. If the server has network interfaces that you aren't using, you should disable those interfaces. You should also carefully maintain software and apply security patches when necessary. Avoid using nonsecure protocols such as Telnet to administer a network server. Firewall rules can establish which computers can connect to servers using safer remote administration methods such as Secure Shell Protocol (SSH), SNMP, Apple Server Admin, or Netopia's Timbuktu. When a server is compromised, attackers may try to use that server to attack other servers. Although network security usually focuses on what traffic is allowed into servers, you may also want to develop firewall rules that restrict applications that a server can go to, in case the server gets compromised. Finally, one last general point is that you must read logs. Firewall logs are especially important for recognizing impending (or possibly already successful) attacks. Setting Up FirewallsA firewall is software or hardware that guards the entrance to a network or computer and keeps out unwanted network traffic. It creates a protected environment "behind" or "inside" the firewall that is distinct from the risky world that lies "beyond" or "outside" it. A firewall can run on a router, a server (such as a Mac OS X server), a dedicated hardware box, or an individual Macintosh or PC. Security experts often make a distinction between a host firewall and a network firewall:
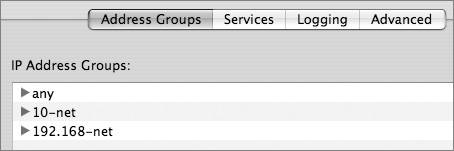
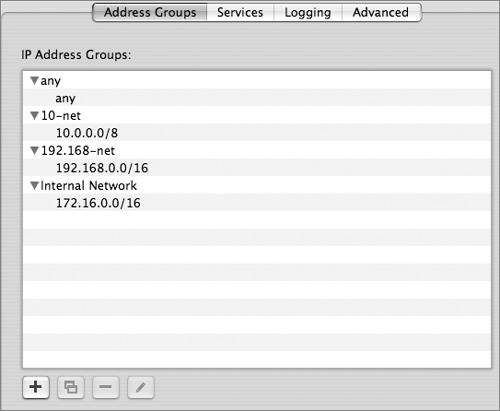
A firewall has a set of rules that specify whether network traffic should be accepted, denied, or handled in some other way. As part of your network security design, you must decide if you want to configure firewall rules that protect the server or rules that protect the networks connected by the server, or both. Firewall rules specify criteria that are applied to a packet to determine if the packet should be accepted or denied. Typical criteria are the packet source address, the packet destination address, the protocol type in the IP header, or the source or destination port numbers in the TCP or UDP header. Some firewalls, including Mac OS X Server, have more advanced capabilities. For example, to allow all TCP traffic back in for a connection that an inside user initiated, you can allow all packets with the TCP ACK or RST (reset) bits set. This avoids traffic with only the SYN bit set, which would indicate traffic initiated by an outsider rather than an inside user. Allowing traffic with the ACK or RST bit set is called "allowing established traffic." For each packet, a firewall reads the list of rules in order. If a rule applies to the packet, the action specified in the rule is taken (for example, accept or deny) and the reading of further entries in the list usually ends. Because firewall software tests a packet against each criterion in the list of rules until a match is found, you should design rules with care to avoid problems and to provide good performance. It won't work, for example, to deny all TCP packets from a network before you allow TCP from one host on that network. You would have to do it the other way around. On the other hand, to optimize performance, when possible you should design the list so that most packets match the earliest conditions. Fewer conditions to check per packet means better throughput. To optimize security, the last statement should be a general deny-all statement. A stateless firewall looks at packets as individual events. A stateful firewall, on the other hand, can track multipacket communication sessions and more intelligently accept or deny traffic. For example, a stateful firewall can remember that a protected client initiated a request to download data from an Internet server and allow data back in for that connection. Mac OS X Server can do both stateless and stateful processing. To use stateful processing, Mac OS X Server adds the keep-state keyword to rules. Set Up Mac OS X Server Firewall ServiceThe Mac OS X Server firewall is built on the standard, open-source ipfw software from FreeBSD UNIX. Like most firewalls, the Mac OS X Server firewall scans incoming packets and accepts or denies them based on the packet-filtering rules that you configure. You can restrict access to any service running on the server, and you can customize filters for all internal clients or for a range of internal IP addresses. You can also allow or disallow traffic from the server to implement advanced security policies. Although you can add and delete rules with the UNIX ipfw tool using Terminal, usually you don't need to do this; Server Admin provides a sophisticated and easy-to-use interface to ipfw. The one ipfw command that you will use regularly, however, is sudo ipfwshow, which displays the rules that ipfw is using. It shows you exactly what the underlying ipfw service is doing and helps you verify that the configuration you set up with Server Admin is correct. Create Firewall Address GroupsTo simplify configuring firewall rules, Server Admin enables you to set up address groups. An address group can be a single address, such as 192.168.3.1, or a range of addresses, such as 192.168.3.0192.168.3.255. You can set up a range of addresses using subnet mask notation (192.168.3.0: 255.255.255.0) or Classless Interdomain Routing (CIDR) notation (192.168.3.0/24). Mac OS X Server has three preset firewall groups:
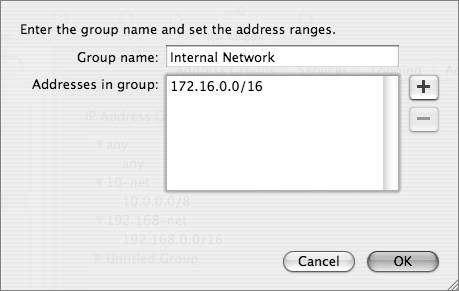
As part of your network security design process, you should have identified the user communities in your environment that need security. These user communities can become address groups. Because you will probably have many rules that apply to addresses, configuring address groups as your first step will save you much typing when configuring rules. By default, the Mac OS X Server firewall includes an address group for "any" (meaning any IP address) and may include other defaults, depending on your configuration. To create an address group:
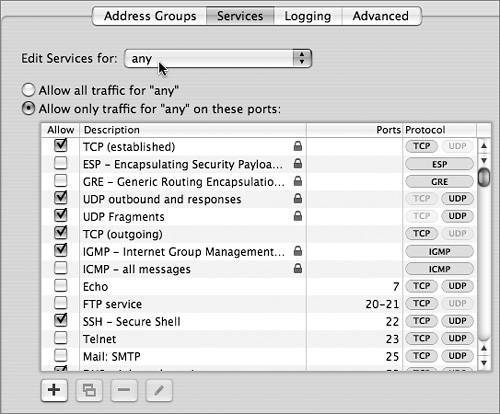
As an example, you could configure an address group for the network manager. Later, you could use this address group when setting up rules to specify what the network manager can do (remote server administration, SSH, and so on.) Use the Services and Advanced PanesOnce you have some address groups configured, you can configure rules using the Services and Advanced panes in Server Admin. The Services pane is quite user-friendly, whereas the Advanced pane is optimized for a finer degree of control. In the Services pane, you can configure rules that will apply to traffic into the server. For example, one of your first configuration steps should be to specify which services the any group can reach on the server. To do this, you enable (select) or disable (deselect) services for any. The wording in the Services pane can be confusing. When the pane says "edit services for any," for example, it actually configures rules to allow traffic from any address to the services checked. For example, by checking Mail: SMTP, the following rules are added to ipfw:
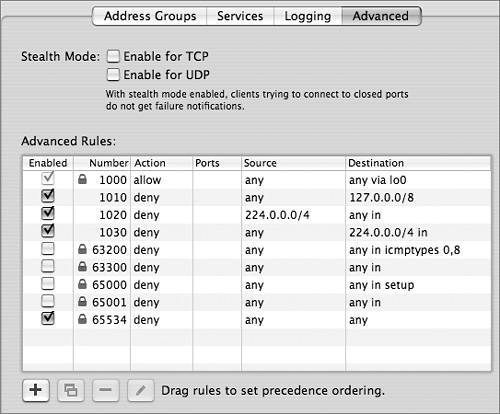
The 12305 is a rule number. (The firewall can have more than one rule with the same number. It reads and obeys the rules in the order that they appear in the list.) The first "any" in the rule means any source IP address. The second "any" means any destination IP address. Port 25 is the well-known port for Simple Mail Transfer Protocol (SMTP). When using the Services pane to add rules, the firewall automatically allows traffic destined to both UDP and TCP ports 25, even though SMTP doesn't use UDP. To configure more advanced rules, use the Advanced pane. The Advanced pane is also useful for displaying default rules. The firewall adds low-numbered rules (1000-1030) to cover well-known vulnerabilities and high-numbered rules (63200-65534) to cover typical default policies. The most important default policy is covered by rule 65534, which denies all IP traffic not covered by lower-numbered rules. Generate and Review ipfw show OutputYou can see the rules that your firewall has enabled by clicking Active Rules in the Server Admin application or by opening Terminal (Applications/Utilities) and entering sudo ipfw show. The following table explains the rules in use on a typical server that connects an "outside" Ethernet network that goes to the wide area network (WAN) and the Internet, and an "inside" Ethernet interface that connects a private local area network (LAN). The outside interface is en0 and the inside interface is en1. The inside network is 192.168.3.0/24. The server is providing NAT for this private address range.
Understanding Network Address TranslationNAT converts addresses that are used on an inside network to addresses that are appropriate for an outside network, and vice versa. NAT is useful when computers that need access to the Internet have private addresses. Private IP addresses are addresses that a network administrator assigns to internal networks without any coordination from an ISP or one of the regional registries for IP addressing, such as the American Registry for Internet Numbers (ARIN). An ISP or registry provides public addresses for Web servers or other servers that external users access, but public addresses aren't required for internal computers. The Internet Engineering Task Force (IETF) reserves the following numbers for private networks:
With NAT, when an internal computer sends a packet, a NAT gateway (such as Mac OS X Server) dynamically translates the private source address in the packet to a public address. The gateway keeps track of this translation and converts the destination address on return packets to the correct private address. Private addressing offers some security, although it could be considered merely security by obscurity. Private network numbers are never advertised to the Internet because they aren't globally unique. Not advertising internal network numbers provides some privacy. Of course, additional securityincluding firewalls, IDSs, and antivirus softwareshould also be deployed. NAT sometimes gives people a false sense of security, but keep in mind that a privately addressed computer is actually still reachable from the Internet if the NAT gateway is functioning correctly, but a firewall is not in place and configured correctly to protect the computer. Mac OS X Server NAT ServicesMac OS X Server makes an excellent NAT gateway, especially when used with Gateway Setup Assistant (added in Mac OS X version 10.4), which makes setting up NAT even easier than it was in previous versions of Mac OS X. When Mac OS X Server provides NAT services, it translates internal addresses to the address assigned to the external address. It also keeps state information so that traffic coming back in can be translated and sent to the right internal address. When you enable NAT, the natd process is started and a rule is added to the firewall to divert packets that come in via the outside interface to the natd process. For example, the previous table showed the following rule, where 8668 is the process ID for natd and en0 is the outside interface: 00010 divert 8668 ip from any to any via en0 Enabling NAT also adds a rule to allow traffic initiated by inside users and to keep state so that return traffic is allowed. For example, the following rule is added to support internal users on the 192.168.3.0/24 network, reachable via the server's inside interface en1: 12307 allow ip from 192.168.3.0/24 to any via en1 keep-state Note that if you enable the NAT service, you are also required to enable the firewall service. Otherwise packets won't be diverted to the natd process and NAT service will not take effect. Mac OS X Server Gateway Setup AssistantThe Gateway Setup Assistant helps you quickly and easily set up Mac OS X Server for routing and NAT. It also enables the firewall and adds some default firewall rules. Depending on your configuration choices, the assistant will do the following when it is finished:
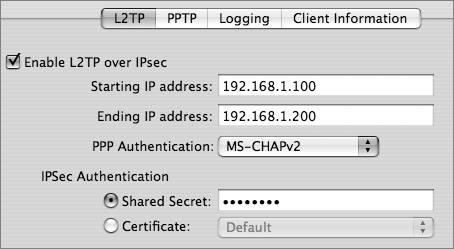
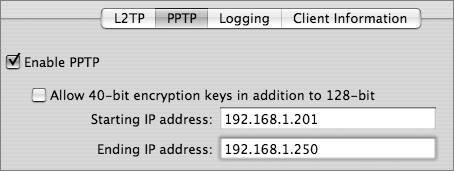
To use the Gateway Setup Assistant, you can open the Gateway Setup Assistant application from the Applications/Server directory on the server, or you can select View > Gateway Setup while in Server Admin. Follow the directions in the assistant and click Continue after each page. Read the final output carefully, and make sure you approve of the configuration before finalizing the settings. Before running Gateway Setup Assistant, you should have planned which interface will connect the outside network, which interfaces will connect the inside networks, and whether you want to enable VPN. The first interface that Gateway Setup Assistant asks about is the outside interface that connects to the Internet. The assistant calls this the WAN interface, even though the interface probably uses a classic LAN technology such as Ethernet. 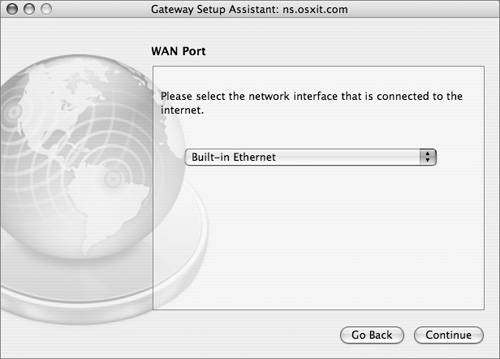 Note Gateway Setup Assistant assumes that the outside "WAN port" gets its address via DHCP. A DHCP address for an outside interface is typical in home networks but not in enterprise networks. On an enterprise network, it's more common for the outside interface to have a public address or an address assigned by a corporate network manager. You may need to use System Preferences > Network to reenter the correct address for your outside WAN interface after running Gateway Setup Assistant. Understanding Virtual Private NetworkingVPN supports mobile users, telecommuters, and business partners who may not physically be on a private network but want to virtually appear as if they are. Users run VPN client software that lets them connect to the private network in a secure fashion. Because the users might be on a public, insecure network, such as the Internet, all their traffic to the private network is sent in an encrypted tunnel. This allows users to travel outside the physical boundaries of the private network, but still have access to the network. LAN-to-LAN VPNs are also possible. In this case, two private networks are connected via a public network, such as the Internet. Security is maintained because all traffic between the LANs is sent in an encrypted tunnel. Mac OS X Server VPN ServicesThe built-in VPN server on Mac OS X Server supports Mac, Windows, and Linux systems running standards-based VPN client software. Both the Layer Two Tunneling Protocol (L2TP) and the Point-to-Point Tunneling Protocol (PPTP) are supported. L2TP runs on top of IPSec, which is an IETF set of standards for Network-layer encryption and authentication. You can also use MS-CHAPv2 or Kerberos for authentication. IPSec uses security certificates (either self-signed or from a certificate authority such as VeriSign) or a predefined shared secret. The shared secret must be entered on the server as well as on the clients. L2TP is a better choice than PPTP because it uses strong IPSec encryption and supports both IPSec and Kerberos for authentication. PPTP is still commonly used, however, to support older Windows computers and Mac OS X v10.2 clients. PPTP offers good encryption (provided strong passwords are used) and supports a number of authentication schemes. With PPTP, you can allow 40-bit encryption in addition to the default 128bit encryption if needed by your VPN clients, but note that 40-bit encryption is weaker. Note PPTP has known weaknesses, so you should use L2TP whenever possible. VPN requires firewall configuration. The firewall must be able to pass network traffic from external IP addresses through the firewall to the private network. This can be as open or restricted as you deem necessary. For example, if the VPN clients travel a lot and may come in via a large range of IP addresses, you may need to open the "any" firewall address group to VPN connections. If you know where your users will be coming in from, you can narrow access to a small range of IP addresses. You can create an address group that reflects that smaller range and only enable VPN traffic originating from that list. |
EAN: 2147483647
Pages: 258