Sniffing Around with Ettercap
Although your computer comes with tcpdump , it is not the sort of tool that modern attackers have in their arsenal ”after all, it requires that you know how to type. For the lazy attacker, there are much better options, such as ettercap (http://ettercap. sourceforge .net/). Ettercap hides many of the details of sniffing behind an easy-to-use interface, and can even sniff switched networks.
A few of the "cool features" listed for version 0.6.7 on the Web site include
-
Characters injection in an established connection ” A user can insert characters into a connection between another machine on the local network and a remote host, effectively hijacking the communications.
-
SSH1 support ” Even though SSH is known for security, ettercap can sniff the encrypted data from SSH1 sessions, easily retrieving usernames and passwords.
-
HTTPS support ” Like SSH1 support, ettercap can easily break into HTTP SSL-encrypted streams!
-
Plug-ins support ” Developers can take advantage of the ettercap API to create their own plug-ins.
-
Password collector ” If a password is detected for the protocols TELNET, FTP, POP, RLOGIN, SSH1, ICQ, SMB, MySQL, HTTP, NNTP, X11, NAPSTER, IRC, RIP, BGP, SOCKS 5, IMAP 4, VNC, LDAP, NFS, SNMP, HALF LIFE, QUAKE 3, MSN, or YMSG, ettercap can log it.
-
OS fingerprint ” Easily identify remote operating systems and the network adaptors they use.
-
Kill a connection ” See a connection between two machines that you want to terminate? Ettercap can do it.
-
Passive scanning of the LAN ” Passive scanning can provide information about your network and the attached hosts without actively sending packets to the machines.
-
Check for other poisoners ” You have ettercap and so do the "bad guys." Detects other ettercaps and spoofing attempts on your network.
What makes ettercap truly dangerous is its capability to carry out ARP poisoning. ARP poisoning exploits the stateless nature of the ARP. Normally, machines send out an ARP request asking for the address of another machine, and presumably receive a reply. In ARP poisoning , the replies are sent without a request being made. The sniffer essentially tells the rest of the network that it is every other machine on the network ”and subsequently receives traffic for those machines. This type of attack is easily identified by viewing the ARP cache of a machine on the poisoned network ( arp -a ). If multiple machines map to a single MAC address, you may be viewing the result of ARP poisoning.
NOTEThere are perfectly legitimate reasons for multiple IPs and hostnames to be attached to a single MAC address. Multihomed servers and terminal servers, for example, often have multiple IP addresses assigned to a single network interface. |
Ettercap, for all the attack capabilities built in, also features an extremely useful ARP poisoning detector, making it an effective tool against the very people who use it inappropriately.
You can download a precompiled .pkg version of the latest ettercap release from http://ettercap.sourceforge.net/index.php?s=download&p=binary.
After downloading and installing, start ettercap with /usr/sbin/ettercap . If you have multiple active network interfaces, use the switch -i <interface> to choose which will be used.
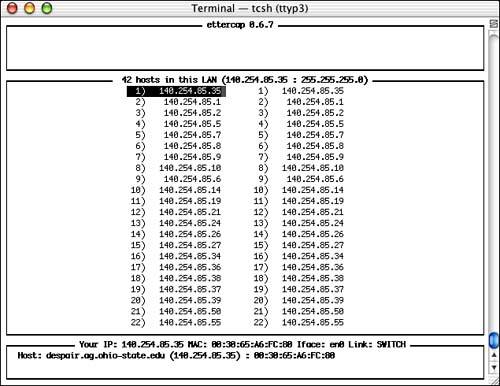
When starting, ettercap initially scans your network and collects IP and MAC addresses for all active machines, and displays two identical columns with the located devices. Figure 7.2 shows the initial ettercap screen.
Figure 7.2. All active LAN devices are shown.
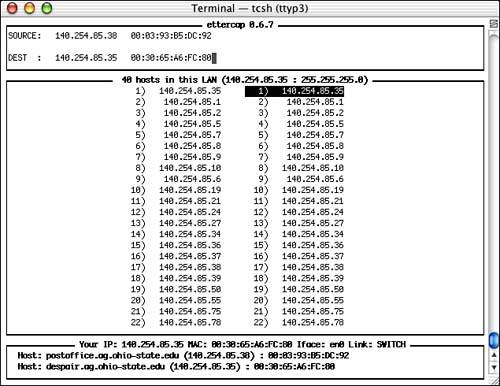
Ettercap is a cursor-based program that you can navigate with your keyboard's arrow keys. Help can be shown at any time if you press h. In the initial display, the left column is used to pick a potential source for sniffing, whereas the right column is the destination. You can choose one, both, or neither (to sniff everything) by moving your cursor to the appropriate selection in one column, pressing Return, then doing the same in the next . To deselect an address, push the spacebar. Figure 7.3 shows a selected source and destination pair.
Figure 7.3. Choose the targets you want to sniff, or leave either field empty to sniff all hosts.
After choosing your targets, you can use the key commands in Table 7.3 to start sniffing and monitoring the hosts. Several commands do not require a source or destination and simply operate on the entire network, or on the actively highlighted machine.
Table 7.3. Ettercap Sniffing Commands
| Keystroke | Purpose |
|---|---|
| a | Start sniffing using ARP poisoning. |
| s | Sniff based on the IP addresses of the selected machines. |
| m | Sniff based on the MAC addresses of the selected machines. |
| j | Poison the ARP caches of the chosen machines, but do not sniff. |
| x | Forge a packet (including all headers, payload, and so on) from the chosen source computer to the destination. |
| d | Delete an entry from the list; it will not be subjected to ARP poisoning if unlisted. |
| f | Fingerprint the remote OS. |
| o | Passively identify hosts on the network. |
| c | Check for ARP poisoners; ettercap will identify all hosts responding to more than one IP address. |
| r | Refresh the host listing. |
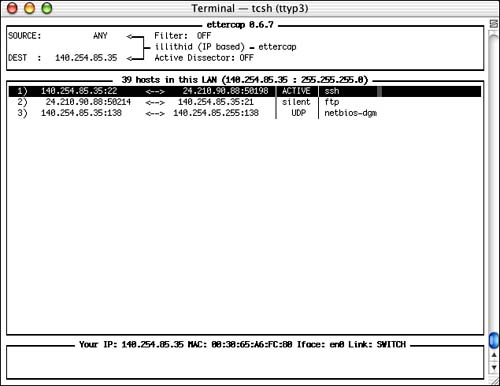
After ettercap has started sniffing, the screen will refresh with a new display listing all the active connections that you can monitor, as shown in Figure 7.4. In this example, there are three connections: SSH, NetBIOS, and FTP.
Figure 7.4. Choose the connection to monitor.
Use the arrow keys to choose an interesting connection (such as the FTP session shown in the figure), the press Enter, or use one of the other options, shown in Table 7.4.
Table 7.4. Choose What to Sniff
| Keystroke | Purpose |
|---|---|
| return | Sniff the connection. |
| x | Forge a packet within a connection. |
| f | Filter the connections based on packet attributes, such as port numbers . |
| a | Turn on active password collection. |
| l | Log all collected passwords (FTP, SSH, Telnet, and so on) to a file. The file will be named with the current date and time. |
| k | Kill the selected connection. |
| d | Resolve the selected IP |
| r | Refresh the list. |
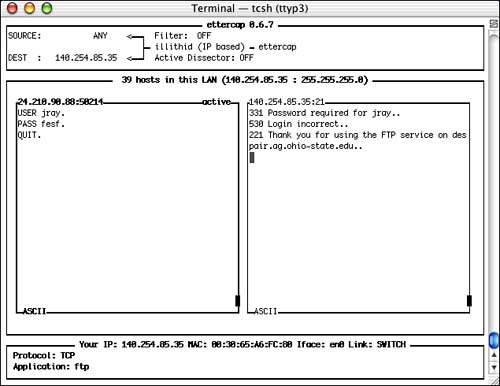
Assuming you chose to sniff the connection, the right side of the screen will refresh with a log of the data coming from the source, whereas the left will contain the responses sent from the destination. Figure 7.5 shows a sniffed FTP login that has failed.
Figure 7.5. Watch the Presentation layer data in real time.
Use the key commands in Table 7.5 to control the sniffed connection.
Table 7.5. Control the Sniffed Connection
| Keystroke | Purpose |
|---|---|
| k | Kill the connection. |
| a | ASCII view of the sniffed data. |
| h | Hex view of the sniffed data. |
| j | Join the source and destination windows . |
| t | Display only text (readable) characters. |
| i | Inject characters into the connection. |
| l | Log the sniffed data to a file. |
| b | Bind the sniffed data to a port. (You can then connect to this port on the sniffer to monitor the connection.) |
| q | Exit to the previous screen. |
As you can see, ettercap is easy to use and extremely powerful. I highly suggest that you read through the available help screens and be very careful with what you choose to do. The default distribution of ettercap includes a number of external plug-ins ranging from ettercap detectors to DoS attack implementations (for informational purposes only).
TIPUsing the cursor-controlled interface is the most user-friendly means of operating ettercap, but for those who want to run it via script or launch it as a daemon, all functions are accessible via the command line. Type /usr/sbin/ettercap -h to display the command-line syntax. |
| |
| |
| Top |
EAN: 2147483647
Pages: 158