Web Development Risks
Web development differs from other development methods in that users' actions affect your computer, not theirs. Programming errors, either naive or malicious, can be made to provide intruders access to your system via the comfort of their Web browser. Many of the errors discussed in this book result from mishandling of user input. In the case of CGI applications, this is the primary focus of concern. If user input can be manipulated beyond the intentions of the developer, it can often be used in malicious ways.
Many Web developers consider Web pages to do nothing more than make a visual presentation: An interface is displayed, and users are given a few fields, switches, and toggles they can use to send information back to the server for processing. This, unfortunately , does not take into account the information contained within the page's HTML code. Consider, for example, the PHP code for a "system status" application shown in Listing C.1:
Listing C.1 A "Harmless" System Status Application ( status.php )
1: <?php 2: if ($action) { 3: $output='$action'; 4: print "The result is:<br />"; 5: print "<pre>$output</pre>"; 6: } else { 7: ?> 8: <form action="<?php print $me; ?>" method="post"> 9: <select name="action"> 10: <option value="uptime">Uptime</option> 11: <option value="who">Current Users</option> 13: </select> 14: <input type="submit"> 15: </form> 16:<?php 17:} 18:?> This seemingly harmless (and potentially useful) tool allows users to view their computers' uptime or active users from a Web page, as shown in Figure C.1 and Figure C.2.
Figure C.1. Choose the information to display
Figure C.2. and it is returned to the Web browser.
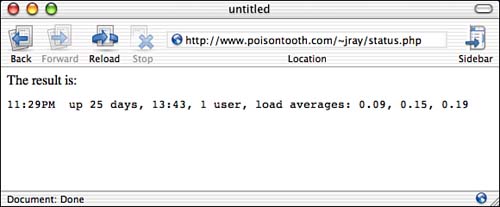
For average users, the page holds little risk beyond the obvious no-no of displaying valid usernames of the people currently logged in to the system. Enterprising individuals, however, may view the source code for the initial display screen (Figure C.1) and notice the lines:
<select name="action"> <option value="uptime">Uptime</option> <option value="who">Current Users</option>
These lines contain the actual commands ( uptime and who ) that are used to generate the output. These commands are supplied to the application via the variable action . Although the interface to the application does not provide a means of choosing something other than uptime or who , this is easily circumvented by simply calling the Web application with an action specified in the URL. For example, status.php?action=ls%20-alR%20/Users , would execute the command ls -alR /Users ”or a recursive list of all the user directories on the machine:
The result is: total 10576 drwxrwxr-t 14 root wheel 476 Oct 23 15:33 . drwxrwxr-t 31 root admin 1054 Nov 13 09:46 .. -rw-rw-rw- 1 jray unknown 6148 Oct 8 13:55 .DS_Store -rw-r--r-- 1 root wheel 0 Jul 14 07:33 .localized drwxrwxrwt 3 root wheel 102 Jul 14 02:20 Shared drwxr-xr-x 12 502 staff 408 Jun 27 2001 mysql drwxr-xr-x 12 skonowal admin 408 Sep 17 2001 skonowal /Users/jray/: -rw-r--r-- 1 root staff 793 Sep 11 13:21 #Work.ics# drwxr-xr-x 174 jray staff 5916 Nov 19 21:39 . drwxrwxr-t 14 root wheel 476 Oct 23 15:33 .. -rw-r--r-- 1 jray staff 3 Nov 14 2000 .CFUserTextEncoding -rwxr-xr-x 1 jray staff 12292 Oct 31 20:14 .DS_Store -rw-r--r-- 1 jray staff 4727 Sep 12 2001 .DiskCopyLog -rw-rw-rw- 1 jray staff 153600 May 9 2001 .FBCIndex drwxrwxrwx 3 jray staff 102 May 9 2001 .FBCLockFolder drwx------ 3 jray staff 102 Oct 14 15:34 .Trash drwxr-xr-x 4 root staff 136 Mar 27 2002 .cpan drwxr-xr-x 3 root staff 102 Oct 10 10:47 .emacs.d -rw------- 1 jray staff 129484 Nov 27 14:05 .mysql_history drwxr-xr-x 17 jray staff 578 Nov 22 2001 .ncftp drwxr-xr-x 3 jray staff 102 May 22 2001 .qt Suddenly, the entire contents of the machine are accessible via the Web. Apache does a good job of providing access controls over what directories can be accessed and by whom, but in one fell swoop, all of Apache's access control is bypassed. Keep in mind that the Web application, although capable of executing arbitrary code on the server, has only the access privileges of the Apache process owner ( www ). Even so, the potential for damage is great. Executing the command find / - exec "rm" "{}" ";" would result in every single world-writable file and directory being removed from the attacked system. Directories such as /tmp and shared storage areas would be wiped clean ”even entire drives that take advantage of Apple's Ignore Privileges on This Volume feature would be wiped out.
Obviously, this is an example of an extremely poorly designed Web application. Unfortunately, it isn't an uncommon development technique to make calls to the operating system to perform certain functions. User input, however, should never directly be used in a system shell call. By passing shell metacharacters to a shell command, a user can execute arbitrary code.
NOTE
A metacharacter is a character that is interpreted "differently" by a shell ”not as part of a file name. The characters & , ; , and > are examples of metacharacters. For more information on a given shell's metacharacters, read the associated man page (that is, man tcsh ).
Consider another seemingly innocuous piece of PHP code shown in Listing C.2, showfile.php :
Listing C.2 Another Disaster Waiting to Happen: showfile.php
1: <?php 2: $fp = popen ("cat /Users/jray/public_html/$filename", "r"); 3: while (!feof($fp)) { 4: $buffer .= fread($fp, 1024); 5: } 6: print "<pre>"; 7: print $buffer; 8: print "</pre>"; 9: ?> The showfile.php program performs (when working as intended) one simple task: It displays a named file in my HTML directory /Users/jray/public_html within the <pre></pre> tags. Unfortunately, there are a few problems with the code that may not necessarily be obvious at first glance.
First, although the full path is specified in the code ( /Users/jray/public_html/$filename ), a user can easily display any file by supplying a custom value for filename as a URL parameter. For example, consider showfile.php?filename=../../jackd/secretfile . This translates to the directory /Users/jray/public_html/../../jackd/secretfile , which is equivalent to /Users/jackd/secretfile ”a location that was never intended to be accessible at all.
A second, less obvious problem also exists: the opportunity to execute arbitrary code, just as the first example offered . To do this, one can simply chain a command onto the end of the $filename variable. Multiple commands are separated in the shell by the ; character. To generate a listing of the root directory, for example, one could call the script using showfile.php?filename=;%20ls%20-al%20/ (the %20 is a URL-encoded space):
total 9409 drwxrwxr-t 31 root admin 1054 Nov 13 09:46 . drwxrwxr-t 31 root admin 1054 Nov 13 09:46 .. -rwxrwxr-x 1 jray admin 6148 Oct 31 20:14 .DS_Store d-wx-wx-wx 3 root unknown 102 Oct 8 14:37 .Trashes -r--r--r-- 1 root wheel 156 Jul 14 02:20 .hidden dr--r--r-- 2 root wheel 96 Nov 13 09:46 .vol drwxrwxr-x 28 root admin 952 Oct 18 13:37 Applications -rw-r--r-- 1 root admin 85504 Oct 31 16:31 Desktop DB -rw-r--r-- 1 root admin 318114 Oct 29 11:48 Desktop DF drwxrwxr-x 13 root admin 442 Oct 10 12:27 Developer drwxrwxrwx 3 root unknown 102 Nov 13 09:46 File Transfer Folder drwxrwxr-x 33 root admin 1122 Oct 18 13:37 Library drwxr-xr-x 6 root wheel 204 Oct 8 17:24 Network drwx---rwx 2 root wheel 68 May 31 2001 Network Trash Folder drwxr-xr-x 4 root wheel 136 Oct 18 13:37 System drwxrwxr-t 14 root wheel 476 Oct 23 15:33 Users drwxrwxrwt 2 root wheel 68 Oct 31 20:14 Volumes dr-xr-xr-x 1 root wheel 512 Dec 1 14:57 automount drwxr-xr-x 37 root wheel 1258 Oct 15 09:53 bin drwxrwxrwt 3 root wheel 102 Oct 14 17:57 cores dr-xr-xr-x 2 root wheel 512 Nov 13 09:46 dev lrwxrwxr-t 1 root admin 11 Nov 13 09:46 etc -> private/etc lrwxrwxr-t 1 root admin 9 Nov 13 09:46 mach -> /mach.sym -r--r--r-- 1 root admin 704492 Nov 13 09:46 mach.sym -rw-r--r-- 1 root wheel 3678188 Sep 7 02:25 mach_kernel drwxr-xr-x 6 root wheel 204 Nov 13 09:46 private drwxr-xr-x 60 root wheel 2040 Oct 8 18:50 sbin lrwxrwxr-t 1 root admin 11 Nov 13 09:46 tmp -> private/tmp drwxr-xr-x 11 root wheel 374 Oct 10 12:27 usr lrwxrwxr-t 1 root admin 11 Nov 13 09:46 var -> private/var
As you can see, a piece of code that was actually designed for a specific purpose and hard coded for a given path is still easily exploited with nothing more than a simple understanding of how your computer parses input strings.
| |
| |
| Top |
EAN: 2147483647
Pages: 158
- An Emerging Strategy for E-Business IT Governance
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- Measuring ROI in E-Commerce Applications: Analysis to Action
- Technical Issues Related to IT Governance Tactics: Product Metrics, Measurements and Process Control
- Governance in IT Outsourcing Partnerships