Summary
| < Day Day Up > |
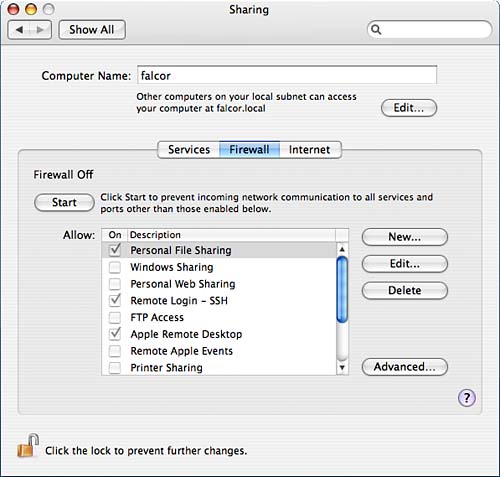
Using the Built-in Tiger FirewallA firewall is something interposed between the stuff that's important and the stuff that's dangerous. In a vehicle, this is the bit of the car that separates the passenger compartment from the engine, protecting the riders from dangers that might occur under the hood. In the world of computers, the firewall sits between the outside network and network services on your computer to protect the computer from network-based attacks. Not that long ago, firewalls were seldom seen, annoying things that got in your way, hindered your work, and generally annoyed everyone, including the seemingly dictatorial network administrators who imposed them on their users. Now, everyone wants one. The most effective firewalls are completely separate devices, physically separating the protected network from the exterior network and its dangers. Much less expensive, and somewhat less effective, is firewall software that lives on the same machine it's protecting. Although a hardware firewall can interrupt network traffic upstream of the protected computer and prevent the traffic from ever reaching the protected machines, a software firewall must transparently intercept traffic as it reaches the machine, determine whether to accept it, and then hand it to the service for which it was destined. This method doesn't prevent the traffic from reaching the machine, but rather tries to prevent the traffic from reaching the services it was headed for. It's not always a successful way of trying to do things, as demonstrated by the fact that there have been a number of commercial software firewalls for a certain other operating system that provide less than complete protection. The firewall software running under Mac OS X's Firewall pane (ipfirewall, sometimes called ipfw) is well respected, however. Although not conceptually as secure as a separate firewall device, it's quite powerful and provides a good level of protection. As with many of the more powerful aspects of the Unix underpinnings of Mac OS X, the GUI interface to the firewall provides access to only the simplest functionality of the software. The ipfw software is capable of considerable sophistication in its control of your network connection, but it requires manual editing of configuration files. More sophisticated configuration than can be accomplished through the GUI is covered in Chapter 28, "Implementing Server and Advanced Network Configuration." Under the Firewall subpane of the Sharing preferences pane, shown in Figure 7.20, you can enable Mac OS X's built-in firewall software and perform simple configuration and control. You can't actually select the check boxes for services that are enabled/enabled via the Services subpane they're automatically checked if you enable the service. Figure 7.20. The Firewall subpane of the Sharing preferences pane.
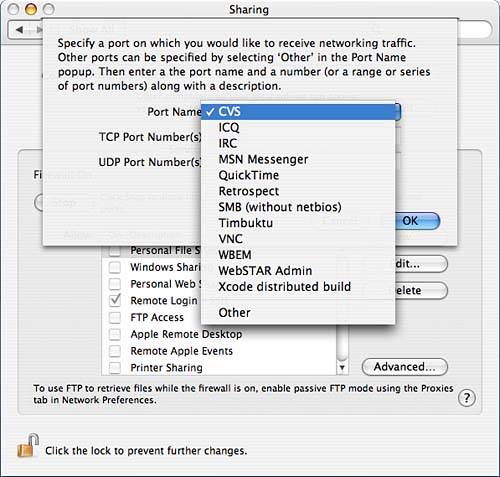
Click the Start (or Stop) button to enable (or disable) the firewall. If the firewall is disabled, all services on your machine are on their own as far as network security goes, and all ports on your machine can be reached from the network. When enabled, the firewall prevents network clients from accessing any port that it isn't explicitly configured to allow. This can protect your machine against compromise by malicious software that might open a port and allow access without your knowledge (again, much more sophisticated configuration is possible from the command line). The check boxes shown in the scrolling list activate and disable access for certain services or port ranges. Those for known services enabled through the Services subpane, however, are automatically checked when the service is enabled and unchecked when the service is disabled, and cannot be edited through the Firewall subpane. These entries for known services also cannot be edited. If you click the New button, you are presented with a dialog like that shown in Figure 7.21. This is where you can configure other services that you want the firewall to allow connections to. Select either a known service-type entry from the shown pop-up list, or the Other entry to configure for unknown services. The dialog automatically fills in the port or port range for known services in the list. For the Other entry, you fill in the applicable port(s) and a description of the service, which is the name that will be used when it is added to the list in the subpane. Figure 7.21. Adding a new service to those passed by the firewall.
The Firewall subpane includes an Advanced options section. In that section, which is shown in Figure 7.22, you can choose to block UDP (User Datagram Protocol) traffic, enable firewall logging, and enable stealth mode, which ensures that traffic to your machine does not even receive notification that your machine exists. You can also open the log, which is located in /var/log/ipfw.log, through the Advanced options section. The five-digit number that you will notice with much of the activity is the rule number that the firewall enforced. Figure 7.22. Advanced options for the firewall.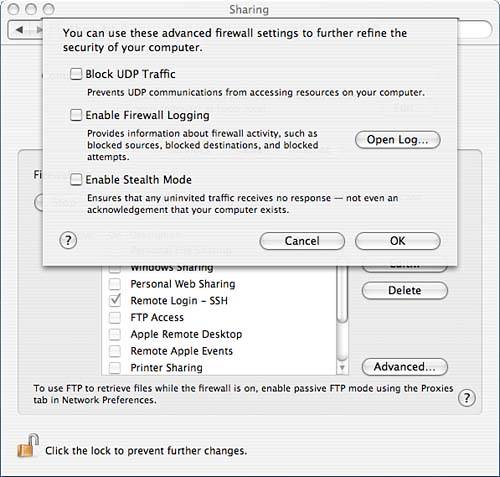 The built-in firewall can protect your machine from incoming connections, but if you are also interested in protecting your machine from outgoing connections, you might take a look at a commercial package called Little Snitch, available at http://www.obdev.at/products/littlesnitch/index.html. Little Snitch notifies you whenever an application tries to make an outgoing connection. You can then allow or deny the connection, or create a rule for Little Snitch to follow the next time. An application such as this can assist in protecting your machine from downloading harmful software such as trojans and worms. |
| < Day Day Up > |
EAN: 2147483647
Pages: 251