Samba
| < Day Day Up > |
Integrating Tiger into an Active DirectoryIf your company is primarily Windows-based, it probably has or is moving to Microsoft's Active Directory. Active Directory (AD) is Microsoft's enterprise directory service. It provides centralized resource and user management for tens, hundreds, or thousands of users. Tiger also supports directory services, such as NetInfo and LDAP, and can even integrate into an AD-based network without resorting to installing special software or compromising the way you use your computer. These features are part of the Apple Open Directory architecture. Open Directory allows Mac OS X computers to interact with directory servers, local files, and network resources to create distributed administration systems that can be used in a wide variety of settings. A properly configured client is subject to the same login/password policies as a Windows client. Mac users can also have their home directory stored on a Windows server and accessed from anywhere on the AD network. Authenticated AD administrators will even have administrative access on Tiger. New to Tiger are mobile AD users. When active, this feature caches the login credentials for users authenticating from the Active Directory and creates a local login for them. If the AD goes down or the machine is not communicating with the AD (such as the case of a laptop that moves around), users will still be able to log in to their accounts. Configuring AD SupportTo set up the connection, open the Directory Access utility (path: /Applications/Utilities/Directory Access). To use an AD server, you need the following information:
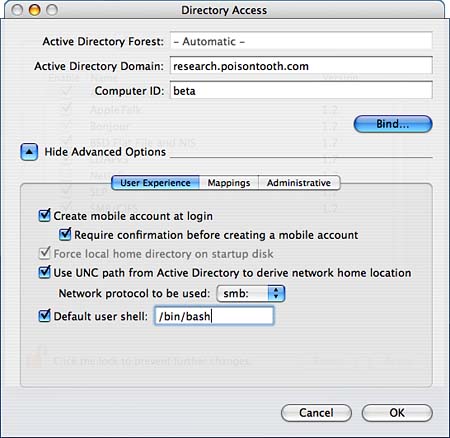
Collect this information from your Windows administrator before continuing. Authenticate by clicking the lock button in the lower-left corner of the window. Highlight the Active Directory plug-in (make sure that it's checked) and then click Configure. A dialog appears, and Directory Access prompts you for information about your AD server. Click the Show Advanced Options disclosure push button to display all the setting options, as shown in Figure 27.7. Figure 27.7. Enter the information necessary to connect to the Active Directory.
The first two pieces of information your AD domain and computer ID are required. The forest is identified automatically. The additional settings are optional but greatly affect how your machine operates within the Active Directory. Use the button bar at the bottom of the window to fine-tune your setup within the areas of User Experience, Mappings, and Administrative. User Experience OptionsThe first setting group, User Experience, controls how the system will integrate Active Directory accounts into the Macintosh experience. Choose between the following settings based on how you want your system to handle home directories and the command-line interface (CLI) shell.
Mapping OptionsBy default, Tiger automatically generates a UID/GID value for users that are logged in from the AD. Because these values don't necessarily correspond to what you might want, you can use the Mapping button to map user and group IDs to specific attributes within the active directory. Systems with Microsoft Services for Unix, for example, can use the SFU UID attribute to map directly to a Mac OS X UID. This doesn't work out of the box, however. The AD schema must be updated to include the attributes that you will be mapping to. Assuming that your AD has these attributes in place, select the check box in front of the attribute you want to map and then enter the appropriate AD attribute. Administrative OptionsThe final settings pane, Administrative, is used to control the default domain server and assign valid AD administrative groups.
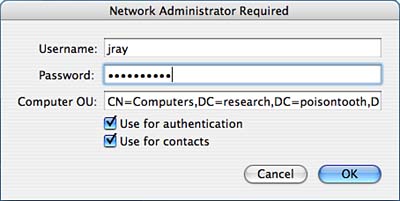
Binding/Unbinding with the DomainAfter your options have been set, click the Bind button. Tiger prompts for a username, password, and search path to identify your computer OU in the Active Directory, as shown in Figure 27.8. This is an AD username and password with the appropriate permissions to add a machine to a domain; it is not your local Tiger admin account. Figure 27.8. Bind with the Active Directory.
Choose how you will be using the binding by selecting Use for Authentication and/or Use for Contacts. Using the AD for authentication will allow AD users to log in to the Tiger system and potentially administrate it (refer to the previous section, "Administrative Options"). The Use for Contacts setting allows applications such as Address Book to query the AD for contact information. Finally, click OK to begin the binding process. Tiger takes a few moments to complete the steps in connecting to the Active Directory. If any errors occur along the way, you will be given specific information to help correct the problem. After the binding has been completed (and assuming that it was set up for authentication), users should be able to log in via the AD by clicking the Other user icon at the Tiger login screen and supplying the standard AD domain credentials instead of local login information. To unbind from a domain, click the Unbind button within the Active Directory plug-in setup screen. You will be prompted for a username and password. Again, this is AD authentication information not a local Tiger account. The supplied username and password must have permission to remove the computer from the AD. If you do not have permission or the unbind fails, click the Force Unbind button to forcibly disconnect from the AD.
|
| < Day Day Up > |
EAN: 2147483647
Pages: 251