C.2 Realization of security services
C.2 Realization of security services
Referring to a generic communication protocol stack, like the one outlined in Figure C.1, the realization of the security services can be localized at either of the two levels [2].
-
Secure channel : The communication subsystem provides the sender and receiver applications with the necessary means for information exchange. The choice of implementing security services into the communication subsystem leads to a solution where a secure communication channel is made available to the applications.
-
This solution was adopted by the SIM Toolkit Application designers who foresaw the realization of confidentiality, data authentication, timeliness, and non- repudiation services at the level of the short message service point-to-point (SMS-PP) transportation layer [3, 4].
-
A similar approach was adopted by Netscape Communications, which designed and proposed the SSL as a transport layer security protocol for the Internet [5]. This security layer is interleaved between the communicating applications and the TCP/IP protocol stack, which is used for the Internet connections. Starting from the SSL protocol, the IETF working group proposed the TLS [6]. The security services provided by this protocol are confidentiality, entity authentication, and key establishment [7].
-
-
Secure communication over insecure channel : Here the communication subsystem provides the sender/receiver applications with a communication link, which initially in itself is not secure. Realizing the security services at the application level leads to the situation where the application itself builds a secure link over the insecure communication channel. The following payment standards implement security at the application level:
-
EMV ¢ debit/credit application both in the chip card and card accepting device terminal [8 “11], as detailed in Chapter 6.
-
Common Electronic Purse Specification (CEPS) [12] application both in the chip card and card accepting purchase or loading device .
-
SET [13] application in the consumer's PC, merchant's Web server, and payment gateway of the acquirer, as is outlined in Chapter 8.
-
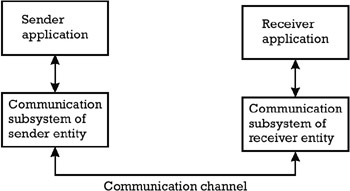
Figure C.1: Generic communication protocol stack.
EAN: 2147483647
Pages: 131