Designing Remote Site Connectivity
For years, companies used WAN technologies to connect remote sites. These WAN connections were typically based on dedicated broadband connections. The drawback to these connections was their cost. As companies have tried to reduce costs, they have increasingly considered using the Internet to interconnect their remote locations. Of course the Internet has never been considered a secure method of communication. Virtual Private Technologies have matured over the past few years to where they are considered appropriate for businesses to take advantage of.
However, many companies are still using dedicated broadband connections, and many others-will consider using them because of the inherent security that they provide. When designing your remote site connectivity, you need to determine what types of connectivity are appropriate for your infrastructure.
Determining Connectivity Needs
Depending upon how large your organization is, you may need connections between locations. Even some small organizations that have a single location may find themselves needing some type of external connection to a business partner. When you are designing your network infrastructure, look at your existing network map to determine which connections you need to retain, and then review all of the interview information to determine if you should add any new connections.
Once you have determined the connections you require in order to keep your locations communicating, you need to make another decision for each one: what type of routing you are going to use. Microsoft has offered software routing as part of the Windows server family for many years, but it does have its limitations. Under Windows Server 2003, RRAS can be used to provide routing functions within an organization, but it is not meant to be used for extremely large environments where the routing topology is complex. However, if you need to have a demand-dial router between your main office and an outlying office, it could very well suit your needs.
Hardware routers are more robust than what you find in RRAS. Most network administrators opt for dedicated hardware routers because they can provide all of the functionality that the administrator needs, and they do not have to use the Windows operating system as the platform on which the routing functions run. Plus, you will find that it is much cheaper to buy a router than it is to pay for server hardware and a copy of the operating system.
No matter which type of router you use, you need to decide upon a routing protocol. Routing tables contain two types of entries: static routes and dynamic routes. Using static entries in a routing table, you can determine where the packets should be forwarded. The drawback to static routing, just like almost any static method, is that you have to manually reconfigure the entries whenever a change takes place. That being said, if you have a demand-dial interface and you only need to provide information about the routing information on the other side of the link, a static routing table can be easy and efficient to use.
Dynamic routing protocols, in a Windows routing environment, is available in two types:
Distance vector The distance vector dynamic routing option for RRAS is Routing Information Protocol (RIP).
Link-state The link-state option is Open Shortest Path First (OSPF).
Before determining which routing protocol you will use within your RRAS server, find out which protocols are used within your existing environment. If the existing routers are broadcasting their routing information through RIP, follow suit with the RRAS server. The same is true for the OSPF capable routers; configure your RRAS server to use OSPF, but make sure you are configuring everything correctly so that you do not cause routing problems within your network due to an inappropriate routing table entry.
| Note | Other routing protocols that are used within enterprise level routers such as IGRP, EIGRP and BGP, are not supported on Windows RRAS. |
Identifying Internet and Extranet Considerations
When connecting your internal network infrastructure to the Internet, you need to determine the best options for your organization. One of the primary challenges you will face is designing a secure solution while staying within the budget of the organization. You will also need to make sure that the solution you design restricts unwanted traffic while still allowing businesscritical data to pass.
In the following sections we are going to look at how you should protect your network by using firewalls. Since firewalls come in many flavors, you will need to determine which is the best fit for your needs.
Determining Firewall Options
Firewalls are devices that control the network traffic into and out from a network. Several firewall options are on the market; some are dedicated hardware devices whereas others are software running on one of the operating system platforms. No matter which firewall type you use, each is usually a member of one of the following configurations:
-
Bastion host
-
Three- homed firewall
-
Back-to-back firewalls
We will look at each in the following sections.
Bastion Host
A bastion host is a single firewall that is used to block traffic coming into the network. Usually found in small organizations, it is the primary means of making sure that only the appropriate traffic is allowed to gain access to the internal network. Although this is one of the least expensive methods of protecting your network, it is also one of the least secure. Because it is the only protection, if the bastion host is compromised, the entire network could be jeopardized. Figure 9.5 is an example of the bastion host.
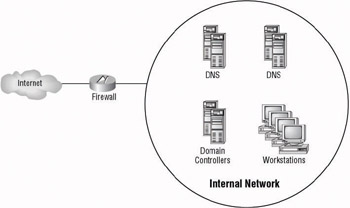
Figure 9.5: Example of the bastion host firewall solution
Three-Homed Firewall
The three-homed firewall is a firewall that is connected to three networks and controls which traffic is allowed to pass to each of them. With this firewall type, one network connection is made to the Internet. The second network, sometimes known as the perimeter network, connection is made to a network that contains resources that can be accessed by users on the Internet. You will usually find web servers on this network. The third network connection is to the internal network. The firewall should not allow users on the Internet to access resources within the internal network, but it should allow resources within the perimeter network to access resources within the internal network. Figure 9.6 is an example of the three-homed firewall.
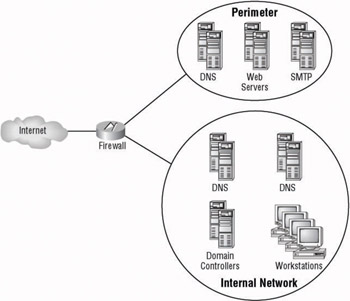
Figure 9.6: Example of the three-homed firewall solution
As with the bastion host, the cost of the three-homed firewall is usually one of the more inexpensive options, but you give up some of your security in using this option. If the firewall is breached, an attacker could gain access to the internal network.
Back-to-Back Firewalls
When you use the back-to-back firewalls option, sometimes referred to as a demilitarized zone (DMZ), two firewalls are employed to increase the level of security to the internal network. The first firewall allows users from the Internet to access the resources within the perimeter network. This front-end firewall has far fewer restrictions than the back-end firewall, whose job it is to block all traffic except the required traffic from the perimeter network. Figure 9.7 is an example of the back-to-back firewall approach.
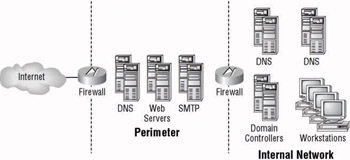
Figure 9.7: Example of the back-to-back firewalls solution
Although this solution is more expensive than either the bastion host or three-homed firewall, it allows for extra levels of security. If the front-end firewall is compromised, the back-end firewall can stave off attacks.
| Tip | Ideally the internal firewall should be from a different manufacturer, or at the very least, the firewalls should be different model numbers , so that common flaws can t be used to attack both boxes. |
In the Building the Firewall Design Scenario, you need to determine the best firewall solution.
Forest Firewall Considerations
Whenever a perimeter network is used, you need to determine how the accounts within the organization will be used. Four options are available for creating the accounts that will be used to authenticate to resources within the internal network and the perimeter network:
-
A single forest design
-
A multiple forest, no trust design
-
A multiple forest, one-way trust design
-
A multiple forest, two-way trust design
| |
Eros is concerned about the safety of his internal network. The previous administrator had configured a bastion host to protect the network from external users, but he had also opened ports to allow access to web servers and an SMTP server. Eros has called you to present options for a more secure network.
-
Question: What options would you present to Eros? Answer: A perimeter network needs to be created if the resources are to be secure. You can present the options of either using a three-homed firewall or a back-to-back solution.
-
Question: If you were designing the network infrastructure for Eros, which of the firewall options would you recommend and why? Answer: The back-to-back firewall option is always the preferred method, although it usually is more costly. If an attacker gains access to the forward firewall and breaks into the perimeter network, they still have another firewall to attack.
| |
You should determine which of the scenarios works best for your organization so that you can have efficient administration of all resources while maintaining a high security level.
Single Forest Design
Most organizations take advantage of the simple single forest design . This is the easiest to administer because all of the accounts used within the internal network and the perimeter network belong to the same forest. However, if an attacker gains access to an account within the forest, they can also access internal resources. If a single forest is utilized, you may want to consider creating a separate domain for the perimeter network. In doing so, you can create accounts within the perimeter network that would not necessarily have access to any resources within the domain or domains used within the internal network.
Multiple Forest, No Trust Design
The multiple forest, no trust design is the most secure of all of the forest options. The perimeter network uses a different forest than the internal network. If an attacker is able to compromise the perimeter network, the accounts used within the perimeter network do not have permissions within the internal network. This is a very costly scenario to implement, however. Not only do you need additional domain controllers and DNS servers to support the infrastructure, the administrative costs increase greatly. Administrators need to maintain multiple accounts and manually maintain connectivity of resources.
Multiple Forest, One-Way Trust Design
The multiple forest, one-way trust design has most of the security benefits of the multiple forest, no trust design, while it alleviates some of the administrative concerns. Although not as easy to design as the single forest design, the multiple forest, one-way design allows administrators to create a one-way trust relationship between the forests so that accounts within the internal network can be added to groups within the perimeter network. Once added to the groups, administrative personnel from the internal network can maintain the resources within the perimeter network. If the perimeter network is compromised, the attackers would not have access to internal resources using the accounts from the perimeter network.
The multiple forest, one-way trust design is more expensive than the single forest design because it requires additional domain controllers and DNS servers to support both forests. The initial administrative overhead is also greater, because the required accounts need to be added to groups within the perimeter network to facilitate administration, but once this is designed and created, administrators don t need duplicate accounts to maintain the internal and perimeter networks.
Multiple Forest, Two-Way Trust Design
The multiple forest, two-way trust design allows trusts to be created between the internal and perimeter forests so that each forest trusts the other. This design allows for nearly the same level of interoperability between the resources of the two forests as the single forest design allows. Accounts from each forest can be added to groups within the other forest to facilitate efficient access to resources. This design allows extranet access to internal resources, but it also opens up security concerns because perimeter accounts can now access internal resources. If an attacker compromises the perimeter network, an account in the perimeter network that has privileges in the internal network could be used to compromise the internal network.
| Tip | SID Filtering should be turned on between the internal and forests so that an attacker cannot take advantage of using the SIDHistory attribute to gain access to resources. |
Designing Secure Replication Through Firewalls
For organizations that utilize the Internet to interconnect offices, firewalls are put into place to restrict access to resources. If the remote office has a domain controller, replication traffic needs to make its way through the firewall so that the domain controller can remain up-to-date. You need to design the network infrastructure to allow for this replication, and you must determine how domain controllers will be created. You must decide the method you are going to use to initially populate the directory service.
Identifying the Initial Promotion Options
Two methods allow Active Directory to be populated during the promotion of a Windows Server 2003 server to a domain controller. The default method involves allowing replication to populate Active Directory. If you choose the default method, the server locates a domain controller that is nearby and requests replication of the objects in Active Directory. The second method is to use the advanced method of promoting the domain controller. If you use the advanced method, the initial population of Active Directory is accomplished using data from the system state that has been backed up from another domain controller. Using the backed-up data, the domain controller does not have to replicate the data across network connections ” the data can be imported locally.
| Tip | Make sure the system state data that you are using for the initial population of Active Directory is as current as possible. The older the data, the more replication will be needed to bring the new domain controller up-to-date. |
No matter which method you used, the server being promoted needs to be able to connect to a domain controller so that it can be authenticated to the domain that it is joining.
| |
Penny is in the process of designing the updated network infrastructure to support her Active Directory design. Currently the design calls for a single forest with a single domain. She has eight locations, and tests have determined that the available bandwidth among all of the locations is sufficient to support the replication traffic that she is anticipating .
During the design of the infrastructure, she determines that she needs to implement a perimeter network to support her SMTP and web servers. After identifying the need for the perimeter network, she returns to the Active Directory design concerned about the security requirements for the perimeter network. Her main concern is the possibility of jeopardizing internal resources if an attacker gains control of a system within the perimeter.
After talking with the staff responsible for maintaining the perimeter servers, she determines that their highest priority is to maintain the security of the organization, but at the same time, they express a desire to make the administration of resources as easy as possible.
Penny s initial perimeter design document identifies the devices within the perimeter network as a separate forest. The domain controllers and DNS servers that support the devices within the perimeter are located within the internal network. The proper firewall rules are created to allow the perimeter devices to pass through the firewall to the domain controllers and DNS servers. Penny identifies that she needs a one-way trust relationship, allowing the administrative staff within the internal network to manage the resources within the perimeter. Penny discovers that she will need additional administration to keep the administrative accounts updated, and the users will need to use a different account when working with the perimeter resources, but she feels that is justified in order to keep the internal network resources protected.
| |
Identifying the Replication Options
No matter which of the promotion options you used, the replication of Active Directory objects between domain controllers is vital to the organization. Without this replicated information, the domain controllers in remote sites would not have accurate directory service information.
Active Directory replication between domain controllers within the same domain occurs using Remote Procedure Calls (RPCs). To allow replication to occur between domain controllers from the same domain in remote sites, you must configure the firewall to allow RPC data to pass. To do so, you must configure the firewall to either have RPC ports open or you must use IPSec to allow replication traffic to pass through the firewall.
USING IPSEC
When you use IPSec for secure replication, all of the replication traffic between the domain controllers is encapsulated in encrypted IPSec packets. Both domain controllers must be configured with the correct IPSec policies. Domain controllers can use a Group Policy object (GPO) that uses Kerberos for IPSec encryption, but any stand-alone server that is being promoted needs to use certificates because it will not be a member of the domain and cannot use Kerberos.
Using IPSec is the most secure way to transmit replication traffic over an insecure network like the Internet because the only ports that need to be opened on the firewall are those used by IPSec, DNS, and Kerberos.
The ports that you will need to open on the firewall in order to allow replication to occur are found in Table 9.2.
| Service | Port/Protocol |
|---|---|
| DNS | 53/tcp, 53/udp |
| Kerberos | 88/tcp 88/udp |
| Internet Key Exchange (IKE) | 500/udp |
| IPSec encapsulated security payload (ESP) | IP protocol 50 |
| IPSec authenticated header (AH) | IP protocol 51 |
OPENING RPC PORTS
If IPSec is not used to protect the replication data, you have to configure ports to allow RPC traffic to pass through the firewall along with DNS and Kerberos. By default, you have to open all of the ports used by RPCs, including all of the dynamic RPC ports. This option opens too many holes within your firewall and could potentially allow undesirable traffic to enter into your internal network.
Microsoft has identified that allowing all of the RPC ports to be opened is not a desirable option, so they have issued a fix that allows you to define a single dynamic RPC port to use. To do so, you must edit the Registry to define the dynamic port. Although this reduces the number of ports that the firewall exposes, it is still not as desirable as using IPSec.
| Note | For more information on how to configure Domain Controllers to use fixed RPC ports, see www.microsoft.com/technet/prodtechnol/windows2000serv/technologies/ activedirectory /deploy/confeat/adrepfir.mspx. |
Identifying Extranet Options
Using the Internet as an extension to your network in order to keep costs down is very popular. Extending it one step further by allowing a partner organization to access your internal resources is the next logical step. By allowing a partner organization to have access to resources within your organization, you can maintain the data and guarantee that it is valid, but at the same time, you need to exercise even greater control over the resources to keep them from becoming compromised.
As you design extranet access, you should determine who needs to access your resources. Only those external users who need access to your internal resources should be able to view the data. Consider creating accounts for each of the external users so they have to authenticate with when connecting. If you only use a single account for all external users, you will lose accountability.
If you have created separate accounts for each of the external users, you should then make sure that they can only access those resources they need in order to perform their job. When you are designing extranet access, it is a good idea to perform an audit of the resource access that is given to users. Having incorrectly applied permissions that allow an internal user to access resources could cause problems, but allowing external users to see confidential information could be disastrous to your company.
Finally, make sure you are only giving access to the correct users within the partner organization. There may be external users who you do not want to have access to your resources. You definitely don t want to allow users from other nontrusted organizations to have access. Part of the design criteria could identify an audit policy that is enacted to monitor access to resources that are made available to partner organizations. This helps you identify inappropriate access to your network.
Guideline for Server Placement
Determining where you are going to place your VPN and RAS servers takes a little planning. First you need to determine where your corporate policies allow you to place your server. Some companies do not allow a server to be placed outside of the perimeter network where it is exposed to the Internet. If this is the case, then you need to determine how you will implement firewall rules to protect the servers that do reside within the perimeter network and, at the same time, still allow efficient client access.
VPN Server Placement
You have two choices when you are implementing a VPN solution:
-
You can use your firewall as your VPN server if it has VPN capabilities and can handle the processing of VPN client data.
-
You can use a software solution. Windows Server 2003 RRAS will act as a VPN server and could potentially be more flexible and easier to deploy than a firewall-based solution.
You really only have two options when deciding where to place software-based VPN servers: either in front of the firewall, exposed to the Internet, or behind the firewall. The advantage of placing the VPN server in front of the firewall is that from there it can process the data as it comes from remote users or other locations and then pass it to the firewall to be directed within the intranet. The firewall should have rules in place that only allow traffic from the VPN server to pass into the perimeter network. The firewall can then scan the data for viruses and determine if the data is valid before it enters any part of your internal network.
More often than not, however, the VPN server is placed within the perimeter network where the firewall can protect it from attacks. The firewall has rules that direct the VPN traffic to the VPN server, which in turn processes the data and passes it to the correct servers within the intranet. Although placing the VPN server within the perimeter network is the preferred method, you have to expose the entire VPN IP address range through the firewall. You need to determine if exposing the entire VPN server to the Internet outweighs the risk of exposing the perimeter IP address range to attackers.
RAS Server Placement
Clients who connect to a RAS server in order to obtain access to their resources need to be assured that they have access to the same data as if they were working from the internal network. At the same time, you need to make sure that the clients , both internal and external, do not over consume the network when they are accessing their data. Try to place the RAS server as close to the resources as possible. When the client is accessing the network from a remote location, the traffic that it is causing will not be traveling across too many segments.
Just like any other service, though, make sure you are following corporate policies when you are determining where the RAS server can be placed. If your corporate policies do not allow you to have clients access your network segments directly, you may have to place the RAS server in the perimeter network. Of course, this is the safest location for those users who are using a VPN client to access the network from across the Internet. That said, if your corporate policies allow it, you could place a RAS server on the same segment as the resources that your dial-up clients need to access. You need to make sure that you can restrict access to only those parts of the network that the remote client needs to access.
Placing the RAS server within the perimeter network does have security advantages, of course. You can protect the RAS server from potential attackers through the use of firewall controls. You can also control access to resource that reside within the perimeter network and not allow users to access internal resources.
RADIUS Client Placement
As a rule of thumb, you should place the RADIUS client close to the user population that will use it. Doing so could potentially reduce the dial-up charges that are incurred because the users will dial a local point-of-presence (POP) instead of dialing a long distance number to gain access to a RAS server. This also allows the RADIUS client to be administered by staff who are located at, and are responsible for, the servers.
When users connect to the RADIUS client, they are connecting to a local system. They pass their credentials to the RADIUS client; the RADIUS client is then responsible for encrypting the data and passing it securely to a RADIUS server. Because the authentication is actually accomplished by a domain controller, the RADIUS client does not have to be configured with any user account information.
RADIUS Server Placement
Due to the fact that the RADIUS server needs to contact a domain controller in order to authenticate the remote users, it should be placed close to the domain controllers where the users account information resides. If you place the RADIUS server within the local network, you can configure firewall rules that allow RADIUS clients to pass their information to the RADIUS servers. In this manner, you protect the account information within the internal network by using firewalls, and all of the communication between the RADIUS server and the domain controllers is protected there as well.
When it comes down to the lowest level of the network infrastructure, you need to understand the IP addressing options that are available to the network administrator. In the following sections, we are going to look at the options that are available when addressing host systems as well as efficient methods of assigning addresses.
EAN: 2147483647
Pages: 159