Working Within the Group Policy Snap-in Namespace
| The nodes of the Group Policy MMC snap-in are themselves MMC snap-in extensions. These extensions include Administrative Templates, Scripts, Security Settings, Software Installation, Folder Redirection, Remote Installation Services, and Internet Explorer maintenance. Extension snap-ins may, in turn, be extended. For example, the Security Settings snap-in includes several extension snap-ins. You can also create your own MMC extensions to the Group Policy snap-in to provide additional policies. The root node of the Group Policy snap-in is displayed as the name of the GPO and the domain to which it belongs. Using Computer and User ConfigurationsBelow the root node, the namespace is divided into two parent nodes: Computer Configuration and User Configuration. They are the parent folders that you use to configure Group Policy settings. Computer-related Group Policy is applied when the operating system boots. User-related Group Policy is applied when users log on to the computer. Working with Software SettingsThree nodes exist under the Computer Configuration and User Configuration parent nodes: Software Settings, Windows Settings, and Administrative Templates. The Software Settings and Windows Settings nodes contain extension snap-ins that extend either or both of the Computer Configuration or User Configuration nodes. Computer Configuration\Software Settings is for software settings that apply to all users who log on to the computer. This folder contains the Software Installation node, and it might contain other nodes that are placed there by independent software vendors. User Configuration\Software Settings is for software settings that apply to users regardless of which computer they log on to. This folder also contains the Software Installation node. Deploying software will be discussed later in this section. Working with Windows SettingsWindows Settings are available under both User Configuration and Computer Configuration in the console tree. Computer Configuration\Windows Settings is for Windows settings that apply to all users who log on to the computer. It includes two nodes: Security Settings and Scripts. User Configuration\Windows Settings is for Windows settings that apply to users regardless of which computer they log on to. It includes three core nodes: Folder Redirection, Security Settings, and Scripts. Note Depending on the various services you have installed, you might see other nodes such as Remote Installation Services, Internet Explorer Maintenance, or the like in this window. Working with Security SettingsThe Security Settings node allows a security administrator to configure security levels assigned to a Group Policy Object or local computer policy. This can be done after or instead of importing or applying a security template. The Security Settings extension of the Group Policy snap-in, shown in Figure 21.18, complements existing system security tools such as the Security tab on the properties page (of an object, file, folder, and so on), and Local Users and Groups in Computer Management. You can continue to use existing tools to change specific settings, whenever necessary. Figure 21.18. Security Settings in the GPO namespace.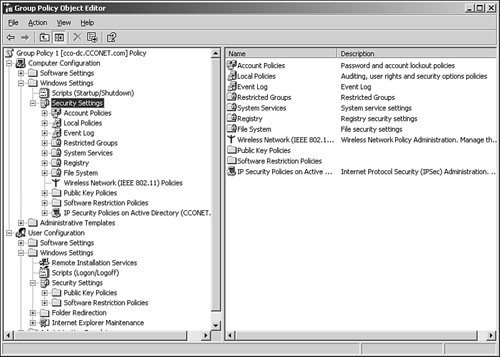 The security areas that can be configured for computers include the following:
Leveraging Administrative TemplatesIn Windows Server 2003, the Administrative Templates node of the Group Policy snap-in uses Administrative Template (.adm) files to specify the Registry settings that can be modified through the Group Policy snap-in user interface. The Administrative Templates node includes all Registry-based Group Policy information. This includes Group Policy for the Windows 2000 and Windows Server 2003 operating systems, its components, and for applications. Policy settings pertaining to a user who logs on to a given workstation or server are written to the User portion of the Registry database under HKEY_CURRENT_USER (HKCU). Computer-specific settings are written to the Local Machine portion of the Registry under HKEY_LOCAL_MACHINE (HKLM). A new Administrative Templates Web view in Windows Server 2003 uses the supported keyword to show you which operating systems are supported clients for individual settings. The Extended tab feature is new. It displays the text that explains the policy setting, as Windows 2000 did, and also indicates which versions of Windows are supported as clients for the setting. This enhancement is very helpful considering Windows Server 2003 adds more than 220 new administrative templates to the Group Policy arsenal. If you prefer a view of the policy setting without the explanatory text, click the Standard tab. To use the view provided by administrative templates, follow these steps:
Deploying Software InstallationsThe Software Installation snap-in can be used to centrally manage software distribution in your organization. You can assign and publish software for groups of users and computers. When applications are assigned to groups of users, all users who require the applications automatically have the application on their desktopswithout requiring the administrator or technical personnel to set up the application on each desktop. When an application is assigned to a group of users, the application is actually advertised on all the users' desktops. The next time a user logs on to her workstation, the application is advertised. This means that the application shortcut appears on the Start menu, and the Registry is updated with information about the application, including the location of the application package and the location of the source files for the installation. With this advertisement information on the user's computer, the application is installed the first time the user activates the application. When the user selects the application from the Start menu the first time, it sets up automatically and then opens. Applications can also be published to groups of users, making the application available for users to install, should they choose to do so. When an application is published, no shortcuts to the application appear on users' desktops, and no local Registry entries are made. That is, the application has no presence on users' desktops. Published applications store their advertisement information in the Active Directory. To install a published application, users can use the Add/Remove Programs applet in the Control Panel, which includes a list of all published applications that are available for them to use. Alternatively, if the administrator has configured this feature, users can open a document file associated with a published application (for example, an .xls file to install Microsoft Excel). Creating and Modifying ScriptsWith the scripts extensions, you can assign scripts to run when the computer starts or shuts down or when users log on or off their computers. For this purpose, you can use Windows Scripting Host to include both Visual Basic Scripting Edition (VBScript) and JScript development software script types. Group Policy Object Editor includes two extensions for script deployment:
This means that the user must have rights to perform the functions of your logon/logoff script. Whether it's a startup/shutdown or a logon/logoff script, the procedure for assigning the script to a computer is the same. To assign computer startup scripts, perform the following steps:
In the Script Name box, type the path and name to the script, as shown in Figure 21.20, or click Browse to search for the script file in the Netlogon share of the domain controller. Figure 21.20. Adding a logon.bat file as a startup script. In the Script Parameters box, type any parameters you want, the same way as you would type them on the command line. Note You must be logged on as a member of the Domain Administrators, Enterprise Administrators, or Group Policy Creator Owners security group to assign scripts. |
EAN: 2147483647
Pages: 499