Using Group Policy to Administer Rights and Permissions
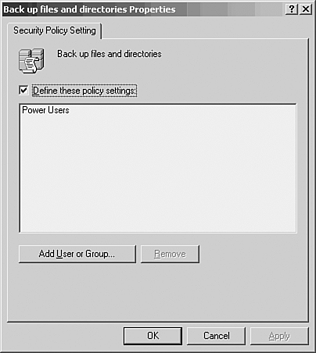
Using Group Policy to Administer Rights and PermissionsTo manage user rights and permissions on a larger scale than simply at the server or workstation level, administrators of Windows Server 2003 Active Directory networks can leverage group policies. Group policies enable directory-based change and configuration management of users and computers. This section focuses on the particular functionality of group policy for access management. For a more comprehensive approach to group policies turn to Chapter 6, "Implementing Group Policies." Assigning Rights with Group PolicyPrevious sections demonstrated using the Local Policy Editor to manage user rights and privileges; you can assign these same user rights and privileges through the Group Policy Editor. The benefit of using group policies to assign user rights is that a larger scope of users or computers can be managed from a single configuration. Assigning user rights with the Group Policy Editor is nearly identical to assigning rights with the Local Policy Editor. The exception is the process by which Group Policy Objects (GPOs) are linked to Active Directory container objects. When you edit the local policy on a workstation or server to assign a particular user privilege, for example to grant the capability to perform backups and restores on a computer, then after the local policy is edited, the configuration is complete. When you make the same configuration at the domain level by creating or modifying a GPO, to enable the configuration, the administrator must also link that GPO to an Active Directory container, for example a particular Organizational Unit (OU). After the GPO is linked to an OU, the policy will apply to all computers contained in that OU. The process of linking a GPO to an AD container can be done in different ways. One way is to modify the properties of the target OU, and create or edit the GPO from that context. To demonstrate this process in detail, the following example details the steps necessary to grant the capability to back up and restore files on all computers contained in the Sales OU to users contained in the local Power Users group of those computers.
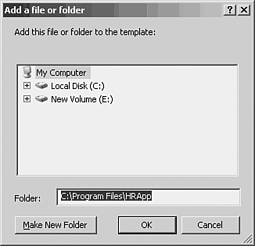
This Process Will Be Different If the Group Policy Management Console is installed on the computer from which group policies are edited, this process will be different. See the section "Enhancing Manageability with GPMC," in Chapter 6 for more information on this new management utility. Assigning user rights through group policies has the added security benefit of preventing changes to the configured settings at the local level. When there are conflicting settings between the local policy and a linked group policy, the group policy settings will override the local settings. Additionally, the local policy cannot be modified, even by a local administrator, if a group policy is in force. Manage User Rights Assignments through Group Policies For environments where a standard security policy is enforced for all workstations (or servers), manage user rights assignments through group policies. To provide flexibility in the environment, set the policies locally and allow local administrators to customize the user settings for particular computers. Granting Access to Files with Group PolicyManaging permissions for files and folders through group policies is similar to the process of editing the Access Control Entries (ACEs) on NTFS file folders and shares. Again, group policies can be used to enforce domain or OU-level security standards across a larger scope of computers. In the case of files and folders, you have the capability to replace the local ACEs on computers contained within the scope of the targeted AD container with ACE settings made in a GPO. In addition to enforcing a security standard on common folder permissions across a broad target of computers, GPO permission settings can also be used to solve access problems that were not evident when initial permission settings were deployed locally. For example, the default local permissions set on the folder, C:\Program Files, limits users to read and execute permissions on this folder and its subfolders in a standard Windows XP workstation. If at a later time a new application is installed on several workstations that create subfolders to which users will need the write permission for proper execution, there will be an access problem that could potentially span hundreds of workstations. The process of changing the local ACE of each workstation would be extremely tedious and time consuming. On the other hand, you can change the ACE through a group policy and fix the problem with just a few keystrokes. The following example modifies permissions on a particular subfolder, C:\Program Files\HRApp, for all user workstations in the Human Resources OU:
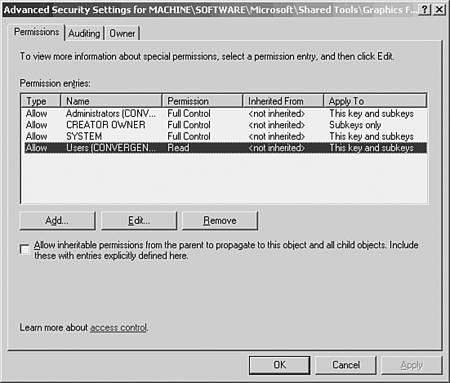
Programs Might Require Modified Permissions In some instances, programs might require modified permissions on only a single file in an otherwise tightly secured folder. This method of replacing permissions via group policy is granular enough to accommodate even single file ACE settings enabling you to maintain the most secure yet functional security policies. Granting Access to Registry Settings with Group PolicyIn addition to being able to modify file and folder permissions, you have the capability to modify security settings in the Registry using group policies. As is the case with file permissions, the functional application of setting Registry permissions with group policies are twofold: you can establish security standards across a greater scope of user permissions on workstations or servers; and you can apply fixes to computers already deployed to a vast population of users. Just as some software requires file permission modifications to run correctly, it is not uncommon to find similar requirements for specific Registry keys. Such requirements, though, might not show up when initial testing and configuration of the software is performed. If an application is deployed to several hundred workstations only to find that a particular functionality does not work with the standard user Registry permissions, it is possible to fix the problem by targeting the workstations with a GPO that addresses the particular Registry security setting. For example, a company might discover after deploying 400 new workstations that standard users cannot change their default JPEG viewer from Internet Explorer to Photo Editor in Windows XP (or vice versa). The workstations will require modified permissions to the following Registry key: HKLM\SOFTWARE\Microsoft\Shared Tools\Graphic Filters. To modify these permissions through group policy, perform the following steps:
Managing Groups with Group PolicyBecause the most efficient way to manage access control to resources is by leveraging groups of various types, it is important to provide a means to manage group memberships across a wide scope of computer objects. To this end, group policies can be defined that limit or set the membership of groups across computer objects contained in the targeted AD container. For example, you might want to limit the membership of the local Power Users group to the Engineering global group for computers contained in the Engineering OU of the domain. By enforcing such a policy, the local Power Users group cannot be modified at the local level to include any other members besides the Engineering global group. To establish this restriction, perform the following steps:
|
EAN: 2147483647
Pages: 325