Auditing Administrative Activities
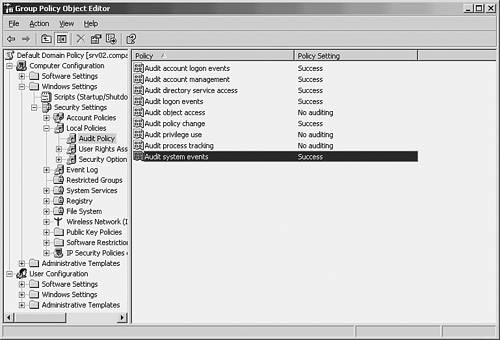
| A key function in managing a centralized/delegated administrative model is proper monitoring of administrative activities. Not only does this give the Network Administrator role the ability to identify security breaches, but also it can provide an essential troubleshooting tool for the Directory Services administrator when permissions and access do not work as expected. To complete this chapter on distributing administration, this section will highlight what should be monitored in a securely distributed administration model. A more detailed account of monitoring is covered in Chapter 21, "Proactive Monitoring and Alerting." Audit Settings on Domain ControllersBecause most administrative delegation occurs in Active Directory, it is wise to monitor administrative activities on domain controllers. You can set the auditing policies for domain controllers by editing the Audit Policy component of the Domain Controller Security Settings as shown in Figure 4.10. Figure 4.10. Editing the Audit Policy for Domain Controllers. On domain controllers, auditing is turned off by default. By defining auditing settings for specific event categories, you can create an auditing policy that suits the security needs of your organization. For each policy setting, you can specify whether to audit successes, audit failures, or not audit the event type at all. Success audits generate an audit entry when the specified type of event succeeds. Failure audits generate an audit entry when the specified type of event fails. To set this value to No Auditing, in the Properties dialog box for a policy setting, select the Define These Policy Settings check box and clear the Success and Failure check boxes. If You Decide to Audit Failure Events in the Account Logon Event Category... you can see if unauthorized users or attackers are trying to log on to your network. Although this can be helpful for intrusion detection, the possibility of a denial-of-service attack increases with the auditing of failure events in the account logon event category. Users who are outside your organization can cause these events to be logged, and as a result they can shut down your network. Collect and Archive Security LogsAn audit trail can contain information about changes that are made to your domain controllers or to Active Directory. If intruders gain administrator rights and permissions, or if delegated administrators abuse their rights and permissions, they can clear the security log, leaving you without a trail of their actions. If you use a tool that regularly collects and saves security log entries across your organization, even if intruders or administrators clear the local security log, you are more likely to be able to trace the actions of intruders or administrators. Microsoft Operations Manager is an example of such a tool. Audit Accounts Management EventsBy auditing success events in the account management event category, you can verify changes that are made to account properties and group properties. Review these events with a keen eye to the administrative groups with the most control ”the Domain and Enterprise Admins groups. If you decide to audit failure events in the account management event category, you can see if unauthorized users or attackers are trying to change account properties or group properties. Although this can be helpful for intrusion detection, the increase in resources that is required and the possibility of a denial-of-service attack usually outweigh the benefits. Size the Security Log AppropriatelyIt is important that the size of the security log be configured appropriately, based on the number of events that your auditing policy settings generate. You can also set a retention period and method of retention for the security logs. |
EAN: 2147483647
Pages: 325