17.7 WIRELESS LANS
|
| < Day Day Up > |
|
17.7 WIRELESS LANS
Experiments on WLANs were conducted more than three decades ago. Those WLANs used a protocol known as ALOHA for medium access. In ALOHA, any station can transmit on the air. If collision is detected (every station is always in receive mode), the transmitting station waits for a random time, and retransmits. This is an inefficient access protocol, but 18% is the channel utilization efficiency because there will be a lot of collisions.
Variations of ALOHA such as slotted ALOHA and reservation ALOHA were developed, which are the basis for CSMA/CD LANs.
As wireless technologies matured and the need for mobile computing increased tremendously, WLANs gained popularity. The IEEE 802.11 family of standards specifies the WLAN standards for different applications. These WLANs can be used in offices for networking of different devices such as desktop, laptop, palmtop, printer, fax machine, and so forth. WLANs also can be used at home to network home appliances.
The two configurations in which a WLAN can work are shown in Figure 17.8.
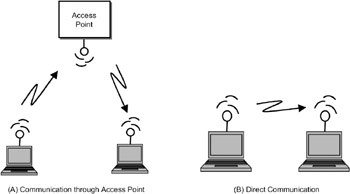
Figure 17.8: WLAN configurations.
In the configuration shown in Figure 17.8(a), a WLAN node (for example, a laptop with a radio and antenna) can communicate with another node via an access point. A WLAN can contain a number of access points. In the configuration shown in Figure 17.8(b), two nodes can communicate directly with each other without the need for a central relay. Such a configuration is known as an ad hoc network. Two or more devices can form a network when they come nearer to one another without the need for a centralized control. Ad hoc networks are very useful for data synchronization. For instance, when a mobile phone comes near the vicinity of a PDA, the two can form a network, and the address book on the PDA can be transferred to the mobile phone.
Wireless LANs operate in two configurations. In one configuration, a node will communicate with another node via an access point. In the other configuration, two nodes can communicate directly without any centralized control.
WLANs based on IEEE 802.11 family standards can be used in offices and homes as well as public places such as airports, hotels, and coffee shops.
IEEE developed the IEEE 802.11 family standards to cater to different industry segment requirements. All the standards in this family use radio as the transmission medium.
17.7.1 IEEE 802.11 Family Standards
The IEEE 802.11 family standards cover the physical and MAC layers of wireless LANs. The LLC layer is the same as discussed earlier. The architecture of the IEEE 802.11 standard for WLANs is shown in Figure 17.9. Each wireless LAN node has a radio and an antenna. All the nodes running the same MAC protocol and competing to access the same medium will form a basic service set (BSS). This BSS can interface to a backbone LAN through an access point (AP). The backbone LAN can be a wired LAN such as Ethernet LAN. Two or more BSSs can be interconnected through the backbone LAN.
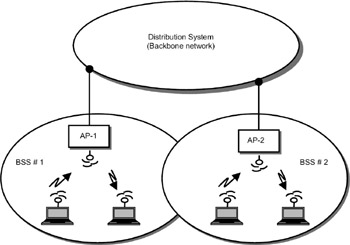
Figure 17.9: IEEE 802.11 wireless LAN.
| Note | In a wireless LAN, there will be a number of access points. These access points are interconnected through a backbone network. The backbone network can be a high-speed network based on Asynchronous Transfer Mode (ATM) protocols. |
The physical medium specifications for 802.11 WLANs are:
-
Diffused infrared with a wavelength between 850 and 950 nm. The data rate supported using this medium is 1Mbps. A 2Mbps data rate is optional.
-
Direct sequence spread spectrum operating in 2.4GHz ISM band. Up to seven channels each with a data rate of 1Mbps or 2Mbps can be used.
-
Frequency hopping spread spectrum operating at 2.4GHz ISM band with 1Mbps data rate. A 2Mbps data rate is optional.
Extensions to IEEE 802.11 have been developed to support higher data rates. The 802.11b standard has been developed that supports data rates up to 22Mbps at 2.4GHz, with a range of 100 meters. Another extension, 802.11a, operates in the 5GHz frequency band and can support data rates up to 54Mbps with a range of 100 meters.
The three physical medium specifications in IEEE 802.11 wireless LANs are: (a) diffused infrared; (b) direct sequence spread spectrum in 2.4GHz ISM band; and (c) frequency hopping spread spectrum operating in 2.4GHz ISM band.
| Note | The Industrial, Scientific and Medical (ISM) band is a free band. No government approvals are required to install radio systems operating in this band. |
17.7.2 Medium Access Control
The MAC protocol used in 802.11 is called CSMA/CA (carrier sense multiple access with collision avoidance). Before transmitting, a station senses the radio medium and, if the channel is free for a period longer than a predefined value (known as distributed inter frame spacing or DIFS), the station transmits immediately. If the channel is busy, the node keeps sensing the channel. If it is free for a period of DIFS, it waits for another period called the random backoff interval and then transmits its frame. When the destination receives the frame, it has to send an acknowledgment (ACK). To send the ACK, the destination will sense the medium. If it is free for a predefined short time (known as the short inter frame space or SIFS), the ACK is sent. If the ACK does not reach the station, the frame has to be retransmitted using the same procedure. A maximum of seven retransmissions is allowed, after which the frame is discarded. Figure 17.10 depicts the CSMA/CA mechanism.
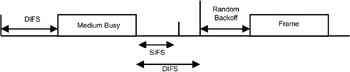
Figure 17.10: Medium access in 802.11 LAN.
The MAC protocol used in IEEE 802.11 is carrier sense multiple access/collision avoidance (CSMA/CA). A node wishing to transmit senses the channel and, if the channel is free for more than a predefined period, it will transmit its data. If the channel is busy, the node will wait for an additional period called the backoff interval.
17.7.3 WiFi
The IEEE 802.11b standard is popularly known as "Wireless Fidelity" (or WiFi) in short. It has become widely popular for wireless LANs in office environments. Proponents of this technology consider it great competition to third generation wireless networks, which also provide high data rate mobile Internet access. WiFi can be used to provide broadband wireless Internet access as shown in Figure 17.11.
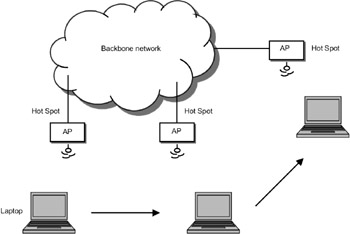
Figure 17.11: Broadband wireless access through wireless LAN.
Access Points (APs) can be installed at various locations in the city. The APs are also called "hot spots". All the APs in a city can be interconnected through an ATM-based backbone network. As the wireless device moves from one location to another, the mobile device is connected to the nearest AP.
The proponents of WiFi consider this architecture, for providing broadband Internet access, to be competitive with third generation wireless networks, which support only 2Mbps data rates. Efforts are now being made to make WiFi a highly secure network so that such an architecture can become widespread. Singapore is the first country to provide mobile Internet access using this approach.
IEEE 802.11b standard is popularly known as Wireless Fideliy or WiFi. The access points are known as hot spots. By installing hot spots at various places in a city, a metropolitan area network can be developed, and this network will be a competitor to 3G wireless networks.
| Note | WiFi hot spots are being installed in many public places such as hotel lounges, airports, restaurants, and so on to provide wireless access to the Internet. |
17.7.4 Mobile IP
When a mobile device moves from one location to another, the packets have to be sent to the router to which the mobile device is attached. Consider a scenario shown in Figure 17.12. The mobile device initially is connected to its home network. The mobile device initiates a very large file transfer from a server located on the Internet. The server delivers the packets to the router, and the router in turn delivers the packets to the mobile device. Now the mobile device is moving in a car and is reaching another ISP (foreign network). The mobile device now has to attach to the router of the new ISP (known as foreign agent). But the packets keep getting delivered to the home agent. The foreign agent assigns a new IP address (called the care- of address) to the mobile device, and this address is made known to the home agent. The home agent forwards all the packets to the foreign agent, which in turn delivers them to the mobile device. If the mobile device has to send packets to the server, it sends them directly via the foreign agent using the care-of address. The requirements for mobile Internet access using mobile IP are:
-
The home agent assigns an IP address to the mobile device, called the home address.
-
The mobile device initiates a connection to the server and the server sends the packets to the home agent (Step 1).
-
As the mobile device approaches the foreign agent, the foreign agent assigns a temporary address to the mobile device, called the care-of address. The care-of address is sent to the home agent. The home agent forwards the packets to the foreign agent (Step 2).
-
The foreign agent delivers the packets to the mobile device (Step 3).
-
If the mobile agent has to send packets to the server, it sends the packet to the foreign agent (Step 4). The foreign agent sends the packet directly to the server (Step 5).
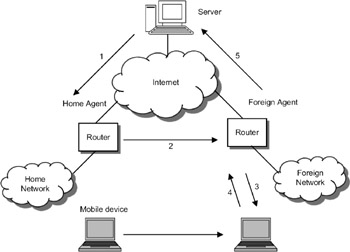
Figure 17.12: Mobile IP.
In mobile IP, the mobile device will have two addresses: home address and care-of aaddress. When the mobile device moves from one network to another network, the packets will be forwarded to the mobile device using those addresses.
17.7.5 IEEE 802.15.3 Standard
The 802.15.3 standard has been developed to meet personal and home area networking needs. This system operates in the 2.4GHz band with a range of 10 meters. Data rates up to 55Mbps are supported. This standard also can be used for industrial applications to network different devices in process control systems. For such industrial applications, the operating temperature has to be from–40°C to 60°C.
17.7.6 HiperLAN2
High performance LAN (HiperLAN) is the standard developed by the European Telecommunications Standards Institute (ETSI) for wireless LANs. The HiperLAN1 standard was developed for providing ad hoc connectivity to wireless devices. It uses the CSMA/ CA protocol. However, HiperLAN1 was not well suited for applications such as voice/video communication, which require real-time performance. HiperLAN2 is the next standard developed by ETSI. HiperLAN2 supports broadband multimedia services as well.
HiperLAN is a wireless LAN standard developed by ETSI. It operates in the 2.4GHz band using TDMA-TDD. Data rates up to 54Mbps are supported to provide broadband multimedia services.
HiperLAN can be used in offices, homes, and public places such as airports, hotels, and so forth. This standard supports both the configuration shown in Figure 17.8. The salient features of HiperLAN2 are as follows:
Modes of operation: There are two modes of operation—centralized and direct. In centralized mode, a mobile device communicates with another device via the access point (Figure 17.8(a)). This mode is used in office environments. In direct mode, two mobile devices communicate directly with each other. This mode is useful for personal area networking at homes and offices.
Medium access control: The medium access control protocol is TDMA-TDD. The TDMA frame is of 2 milliseconds duration during which AP-to-mobile communication and mobile-to-AP communication take place. The time slots are assigned dynamically, based on a request for a connection.
Data rates: Data rates up to 54Mbps are supported. Broadband multimedia services can be supported such as audio and video communication and video conferencing.
Quality of service: In multimedia applications involving voice and video communication, when real-time communication is required, the quality of service parameters are important. For instance, the user should be able to specify that the delay for a particular communication should be less than 10 milliseconds, or the bit error rate should be very low (one error for 100 million bits). HiperLAN2 allows such quality of service parameters by assuring a certain minimum delay or certain maximum throughput. Compared to 802.11 series standards, this standard has this attractive feature.
Summary
This chapter presented the details of local area network protocols and standards. LANs are used to connect devices within a radius of about 10 km. Ethernet, developed in 1978, has become the most popular LAN. Ethernet operates at 10Mbps using carrier sense multiple access with collision detection (CSMA/ CD) protocol for medium access. The IEEE 802.3 standard is based on Ethernet.
The IEEE 802 committee developed a series of standards for LANs using twisted copper pair, coaxial cable, fiber, and radio as the transmission media. The logical link control (LLC) layer, which is common to all the standards, is specified in IEEE 802.2. The IEEE 802.11 family of standards is for wireless LANs.
Wireless LAN based on IEEE 802.11b, popularly known as WiFi (Wireless Fidelity), is the most popular LAN and can be used to provide connectivity in both home and office environments. HiperLAN2 is the wireless LAN standard developed by the European Telecommunications Standards Institute (ETSI). With the availability of wireless LANs that can support up to 54Mbps data rates, wireless LANs are being considered for providing broadband wireless Internet connectivity.
References
-
R.O. LeMire. "Wireless LANs and Mobile Networking Standards and Future Directions", IEEE Communications Magazine. Vol. 34, No. 8, August 1996.
-
S. Xu and T. Saadawi. "Does the IEEE 802.11 MAC Protocol Work Well in Multihop Wireless and Ad Hoc Networks", IEEE Communications Magazine. Vol. 39, No. 6, June 2001.
-
IEEE Communications Magazine. Vol. 39, No. 11, December 2001. This issue contains a number of articles on wireless personal and home area networks.
-
J.P. Macker et al. "Mobile and Wireless Internet Services: Putting the Pieces Together". IEEE Communications Magazine, Vol. 39, No. 6, June 2001.
-
P. S. Henry. "WiFi: What's Next?" IEEE Communications Magazine, Vol. 40, No. 12, December 2002.
-
J. Khun-Jush et al. "HiperLAN2: Broadband Wireless Communications at 5 GHz". IEEE Communications Magazine, Vol. 40, No. 6, June 2002.
-
http://www.ieee.org Web site of IEEE. You can get the IEEE 802 standards documents from this site.
-
http://www.hiperlan2.com Web site of the HiperLAN2 Global Forum.
Questions
-
Explain the Ethernet local area network operation, giving the details of medium access protocol and Ethernet frame format.
-
What is the difference between Ethernet MAC frame format and the IEEE 802.3 MAC frame format?
-
What are the different topologies used for LANs?
-
What are the different MAC protocols used for LANs?
Exercise
| 1. | Measure the throughput of the LAN installed in your office/department. You can use the software package available on your server to find out the effective data rate or throughput. Study the effect of traffic on the throughput by increasing the traffic (by invoking many file transfers simultaneously). | |
| 2. | What are the issues related to security in wireless LANs? | |
| 3. | Work out a detailed plan for installation of a new LAN on your college campus. You need to study the topology, the expected traffic, and how to interconnect different LAN segments located in different buildings. | |
| 4. | Survey the commercially available IEEE 802.11 products. | |
Answers
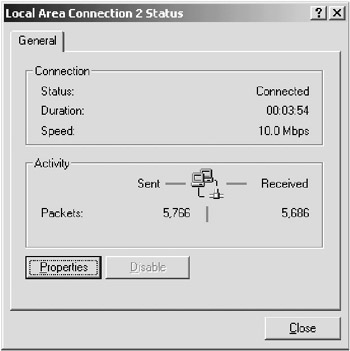
| 1. | You can obtain the LAN connection statistics using the procedure given below. The screen shot given in Figure C.10 shows the LAN activity. It displays the sent packets and received packets as well as connection statistics. On Windows 2000 operating system, you need to do the following: In the Start menu, select My Network Place and then right-click on it. In the pop-up menu that appears, select Properties option. A window with the title Network connections will appear. Right-click on the icon in the Network connections window and select the Status option from the pop-up menu. |
| 2. | Security is a major issue in wireless LANs. The 802.11 standard-based LANs do not provide complete security of information. The security is optional and in many installations, this feature is disabled. The encryption key is common to all the nodes and is stored as a file in the computers. If the computer is stolen, the security key is known to the person who stole the computer. Of course, work is going on to improve the security features of wireless LANs. |
| 3. | To plan a LAN, you need to obtain a map of your campus and find out the traffic requirements. If there are two buildings separated by say, more than 500 meters, you need to install two LAN segments and interconnect them. If laying the cable in a building is not feasible, you need to consider wireless LAN option. |
| 4. | You can get the details of IEEE 802.11 products from http://www.palowireless.com. |
Projects
-
Simulate home agent and a foreign agent on two LAN nodes. You need to study the details of mobile IP to take up this project.
-
Carry out a paper design to develop a wireless LAN for your university campus. You need to do a survey of the various 802.11b products available before doing the design.
-
Interconnect four PCs as a ring using RS232 cables. Develop a Token Ring LAN with these four nodes.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 313