Using Terminal Services on Pocket Devices
| < Day Day Up > |
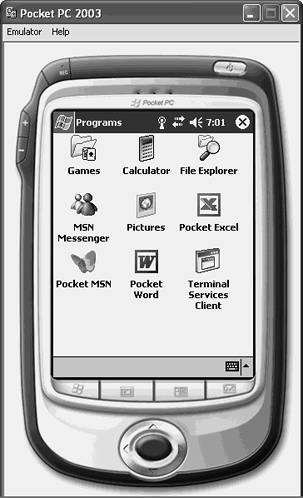
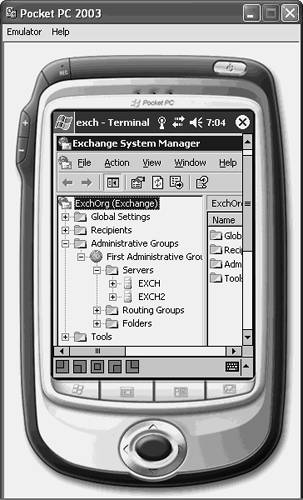
| Many mobile devices, such as pocket PCs, have Terminal Services Client components built in to the device's operating system, as shown in Figure 21.5. The Terminal Services Client connects to the server as a client computer would connect, using Remote Desktop for Administration. After it's connected, as shown in Figure 21.6, administrators can manage the Exchange Server 2003 server from the mobile device the same way they would if they were logged in locally. The obvious downside to using a mobile device is the screen size. Although some mobile devices can resize the screen to accommodate the entire desktop on it, the screen size and resolution is limited. Figure 21.5. The Terminal Services Client component on a Pocket PC device. Figure 21.6. Managing an Exchange Server 2003 server from a Pocket PC device. Locking Down PDA Terminal ServicesSecuring mobile devices, such as the Pocet PC illustrated in the figure, is often more challenging than securing a client computer or another server. Because the device is designed for mobility, it opens up the possibility of losing the device or having it stolen. Then an unauthorized person could use it to gain access to the network environment. An obvious deterrent is securing access to the mobile device's useability. For instance, a person has to use a password in order to use the mobile device. If the mobile device were stolen or found, the person with the device would have to figure out the password before gaining access to the mobile device. Pocket PC 2002 and higher support four-digit PIN numbers (similar to a bank ATM card) and strong, alphanumeric passwords. In addition, each time the wrong password is entered, a timed delay increases before the person can attempt to reenter a PIN or password. The time delay increases exponentially after each unsuccessful logon attempt. Another important aspect to secure is mobile device communications with the rest of the world. The type of security that can be used depends on how the mobile device is configured to communicate. Most devices, however, support using SSL or Wired Equivalent Protocol (WEP). NOTE Although viruses for mobile devices are rare, it is important to implement virus protection software. Antivirus software can also help prevent tracing or monitoring applications from being installed that could record everything that is entered into the mobile device, including passwords. |
| < Day Day Up > |
EAN: 2147483647
Pages: 393