2.2 Network Security
| < Day Day Up > |
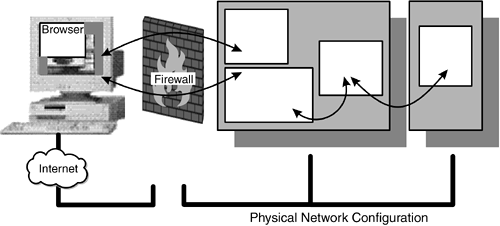
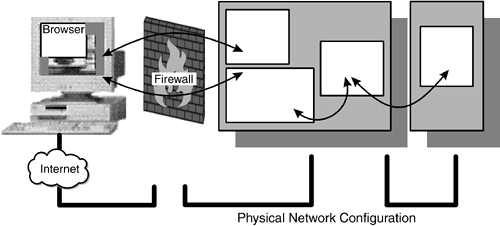
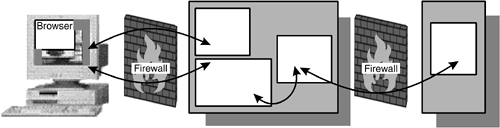
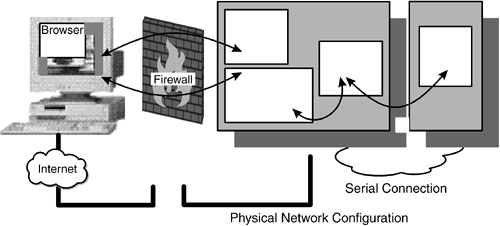
| The classic three- tier architecture pictures can hide other attack routes. Figures 2.2, 2.3, and 2.5 imply that there are separate connections between the client and the Web server/gateway and between the gateway and the end server. However, the real network may not be configured that way. For simplicity or cost, there might be only a single network interface on the Web server, as shown in Figure 2.6. Figure 2.6. Web Server with One Network Interface In this case, the third-tier server is on the same network and can potentially be accessed directly from the firewall. Perhaps the firewall is configured correctly and will prevent direct access to the end server. However, will this be true tomorrow, after additional services have been added? For very little extra cost, the networks can be physically separated by providing two network interfaces in the Web server, as shown in Figure 2.7. Figure 2.7. Separating the Third Tier Or, a second firewall system can be used. This configuration has the benefit that even if the Web server is compromised, the second firewall still restricts access to the rest of the network. It is more expensive to provide such a demilitarized zone (DMZ) (Figure 2.8), but if such a configuration is already required to provide safe Internet connection, there is no extra cost. The cost of a second firewall is likely to be less than the value of the data it protects, so a value assessment needs to be made. Figure 2.8. DMZ Network Environment One additional security barrier to consider using is the type of network. The gateway and the end server could be linked by using SNA protocols or by a small custom-built program communicating over a dedicated serial link. These approaches effectively use the network connection as another firewall; if TCP/IP cannot travel over it, many hacking techniques are simply not possible. However, if the Web server is totally compromised, the hackers have all the communications software at their disposal if they can discover it. Therefore, the third-tier server still needs to be guarded (see Figure 2.9). Figure 2.9. Protection Using Mixed Connection Protocols |
| < Day Day Up > |
EAN: 2147483647
Pages: 164