Chapter 26: Correcting Executable Modules
| | ||
| | ||
| | ||
It is necessary to bear in mind that the correction of executable modules is a difficult task, which requires practical skills and theoretical knowledge. It is impossible to cope with this task without knowing Assembly language. However, I hope that you won't experience difficulties if you have read my book up to this chapter. After all, everything must be OK with your knowledge of the Assembly language! In the Preface, I already substantiated the necessity of investigating and correcting the code of executable modules. I think that both security specialists and hackers are needed in society. In this book, I provide only the required minimum information related to the correction of executable modules.
A Practical Example of Correcting Executable Module
Now, consider a simple [i] example illustrating how to accomplish a job of this type. The problem considered in this section is simple, and it is possible to solve it using only W32Dasm.
The program under consideration is called All Screen 95 Pro. As its name implies, it allows you to capture screenshots of various windows or specific parts of the screen. I downloaded its shareware release from the Internet. This program has been written in Delphi; however, as you'll see, the task can be accomplished even without knowing the development tool, which was used for writing the program. After you start this program, the screen shown in Fig. 26.1 will appear. When you get closely acquainted with this topic, you'll discover that most frequently, it is necessary to locate the program fragment that corresponds to a specific visual effect, such as opening or closing a window or outputting text.
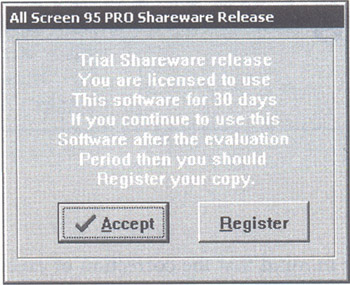
Figure 26.1: Window that appears when the All Screen program is started
After you click the Accept button, there is a delay of approximately six seconds. Then, the program operates normally.
After you start the program 15 times, it displays the window informing that the trial version has expired , and exits.
Thus, you need to solve the following two problems:
-
Eliminate the irritating delay.
-
Correct the program so that it runs correctly no matter how many times you run it.
The window informing the user on the delay is a blunder by the programmer who developed its protection mechanism. The window and its contents can be hidden in the resources. However, when a new record appears in the same window, it becomes the program code. Thus, run W32Dasm and load the All Screen 95 PRO program there. Open the string data reference window and look for the Shareware Delay string there and double-dick it. After closing the window, you'll move to the required location within the program. This fragment is presented in Listing 26.1.
| |
* Referenced by an (U)nconditional or (C) conditional Jump at Address: :004420BC(C) :00442123 33D2 XOR EDX, EDX .00442125 8B83B0010000 MOV EAX, DWORD PTR [EBX+000001B0] .0044212B E8541DFDFF CALL 00413E84 :00442130 33D2 XOR EDX, EDX :00442132 8B83B4010000 MOV EAX, DWORD PTR [EBX+000001B4] :00442138 E8471DFDFF CALL 00413E84 :0044213D 33D2 XOR EDX, EDX :0044213F 8B83B8010000 MOV EAX, DWORD PTR [EBX+000001B8] :00442145 E83A1DFDFF CALL 00413E84 :0044214A BA50000000 MoV EDX, 00000050 :0044214F 8B83BC010000 MOV EAX, DWORD ptr [ebx+000001BC] :00442155 E8D618FDFF CALL 00413A30 * Possible StringData Ref from Code Obj ->"Shareware Delay" :0044215A BAA8214400 MOV EDX, 004421A8 :0044215F 8B83BC010000 MOV EAX, DWORD PTR [EBX+000001BC] :00442165 E8EE1DFDFF CALL 00413F58 :0044216A 33D2 XOR EDX, EDX :0044216C 8B83C0010000 MOV EAX, DWORD PTR [EBX+000001C0] .00442172 E80D1DFDFF CALL 00413E84 :00442177 33D2 XOR EDX, EDX :00442179 8B83C4010000 MOV EAX, DWORD PTR [EBX+000001C4] :0044217F E8001DFDFF CALL 00413E84 :00442184 33D2 XOR EDX, EDX :00442186 8B83C8010000 MOV EAX, DWORD PTR [EBX+000001C8] :0044218C E8F31CFDFF CALL 00413E84 :00442191 8B83CC010000 MOV EAX, DWORD PTR [EBX+000001CC] :00442197 E8E8D4FFFF CALL 0043F684 :0044219C 5B POP EBX :0044219D C3 RET
| |
I intentionally included more lines of code in the listing, among them several starting strings. You see the entire delaying procedure in Listing 26.1. Guessing the meaning of every call command is senseless, although you can discover, for example, that call 00413E84 removes a string from the screen.
To eliminate the delay, it is enough to disable this fragment of code. The easiest way of doing so is inserting the pop ebx / ret commands into its start. Any hex editor, such as HIEW, is suitable for this task. As a result, the delay will be eliminated.
Now, you can tackle the second problem by removing the limitation on the number of times the user can start the program. In one glance at this window, it becomes clear that it is formed in the program. Consequently, to solve this problem, you can try to locate the text displayed on the screen in the program code.
| |
:00443326 8BC0 MOV EAX, EAX :00443328 53 PUSH EBX :00443329 8BD8 MOV EBX, EAX :0044332B 803DEC56440001 CMP BYTE PTR [004456EC], 01 :00443332 7546 JNE 0044337A :00443334 A124564400 MOV EAX, DWORD PTR [00445624] :00443339 E84E2CFEFF CALL 00425F8C :0044333E A1D8564400 MOV EAX, DWORD PTR [004456D8] :00443343 E87816FEFF CALL 004249C0 .00443348 FF05F0564400 INC DWORD PTR [004456F0] :0044334E C605EC56440000 MOV BYTE PTR [004456EC], 00 :00443355 833DF05644000F CMP DWORD PTR [004456F0], 0000000F :0044335C 7E1C JLE 0044337A :0044335E 6A00 PUSH 00000000 :00443360 668B0DB0334400 MOV CX, WORD PTR [004433B0] :00443367 B202 MOV DL, 02 * Possible StringData Ref from Code Obj ->"This Software Has Been Used Over" :00443369 B8BC334400 MOV EAX, 004433BC :0044336E E8BDAEFEFF CALL 0042E230 :00443373 8BC3 MOV EAX, EBX :00443375 E84214FEFF CALL 004247BC * Referenced by an (U)nconditional or (C)onditional Jump at Addresses: :00443332(C), :0044335C(C) :0044337A 33D2 XOR EDX, EDX :0044337C 8B83F4010000 MOV EAX, DWORD PTR [EBX+000001F4] :00443382 E8A52DFFFF CALL 0043612C :00443387 33D2 XOR EDX, EDX :00443389 8B83F8010000 MOV EAX, DWORD PTR [EBX+000001F8] :0044338F E8982DFFFF CALL 0043612C :00443394 33D2 XOR EDX, EDX :00443396 8B83FC010000 MOV EAX, DWORD PTR [EBX+000001FC] :0044339C E88B2DFFFF CALL 0043612C :004433A1 33D2 XOR EDX, EDX :004433A3 8B8314020000 MOV EAX, DWORD PTR [EBX+00000214] :004433A9 E87E2DFFFF CALL 0043612C :004433AE 5B POP EBX :004433AF C3 RET
| |
This time, I included the entire fragment in the listing. Using the cross-reference to the required string, you can easily locate the suspicious command:
CMP DWORD PTR [004456F0], 0000000F JLE 0044337A
Recall that the programs ceases to operate after it has been run exactly 15 times. The simplest way of eliminating this situation is to fill the program fragment from 0044335E to 00443375 with the NOP (90) commands using HIEW.
[i] Simple in relation to the possible problems that might arise when correcting executable modules.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 140