Reconnaissance Attacks
|
|
When dealing with warfare or combat, one of the best ways to eliminate the enemy is to gather intelligence about them, learn their weaknesses (and strengths), and then destroy them with it. This is very similar to the attack patterns of hackers performing reconnaissance attacks. This section of the chapter looks at what the SSCP needs to be aware of when dealing with reconnaissance-based attacks and how to deal with them effectively.
Sniffing
Sniffing means eavesdropping on a network. A sniffer is a tool that enables a machine to see all packets that are passing over the wire (or through the air on a wireless network), even the ones not destined for that host. This is a very powerful technique for diagnosing network problems, but it can also be used maliciously to scan for passwords, e-mail, or any other type of data sent in the clear. TCPDump is the most common UNIX sniffing tool, and also comes with many Linux distributions. Snoop is the Solaris equivalent. These two programs are command-line-based, and will simply begin dumping all of the packets they see in a readable format. They are fairly basic in their functionality, but can be used to gain information about routing, hosts, and traffic types. For more detailed command line scanning, Snort, a freeware tool, offers many more functions than TCPDump, such as the ability to dump the entire application layer, and to generate alerts based on types of traffic seen. Even more advanced, Ethereal is a fully graphical sniffing program that has many advanced features. One of the more powerful features of Ethereal is the ability to reassemble TCP streams and sessions. After capturing an amount of data, an attacker can easily reassemble Web pages viewed, files downloaded, or e-mail sent, all with the click of the mouse. The threat from sniffing is yet another argument for the use of encryption to protect any kind of sensitive data on a network.
Another type of eavesdropping is established by using Trojan horse programs. Tools like SubSeven and Back Orifice can log all user keystrokes and capture screens that can be secretly sent to an attacker's machine.
Exercise 8.03 looks at how easy it is to crack FTP with a sniffer.
Exercise 8.03: Capturing FTP with a Sniffer
In this exercise, you will use a protocol analyzer (Sniffer Pro) to capture FTP traffic on the network. You will look at someone logging into an FTP site with their credentials, and because the network is being sniffed, you will be able to capture the credentials to use later to get into the server.
-
First, open your protocol analyzer. Sniffer Pro was used for these screenshots, but you can use any protocol analyzer you are comfortable with.
-
Build a filter to pick up only FTP-based communications. The filter shown in Figure 8.2 was built to capture only FTP-based traffic. Creating your own filter for this exercise is not absolutely necessary, but makes it much easier to look for FTP traffic when that is the only type of traffic that has been captured.
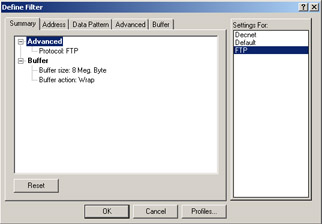
Figure 8.2: Building a FTP-based Filter for Your Protocol Analyzer -
Once you have made the profile for the filter, you can specify only FTP traffic will be allowed through it, as seen in Figure 8.3. This is important because you do not want to alter the default profile. Make a new one and then select only FTP under TCP. This will allow you to capture only FTP-based traffic.
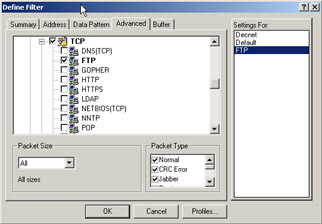
Figure 8.3: Setting FTP as the Only Protocol to Capture with the Sniffer -
Now that you have your filter defined and ready to use, start to capture traffic and simulate a logon to a FTP server. We chose to log on to Novell's FTP site at ftp.novell.com. Below, you can see everything that we did from logging on to exiting the server.
-
You must make sure that you position your sniffer where it will be able to capture such data. In this exercise, you can run the sniffer from your local machine on which you are using FTP.
Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:\Documents and Settings\rshimonski>ftp ftp> open ftp.novell.com Connected to kmpec.provo.novell.com. 220 ftp.novell.com NcFTPd Server (licensed copy) ready. User (kmpec.provo.novell.com:(none)): anonymous 331 Guest login ok, send your complete e-mail address as password. Password: ***************** 230-You are user #12 of 400 simultaneous users allowed. 230- 230-This content is also available via HTTP at http://ftp.novell.com 230- 230-Other FTP mirror sites of ftp.novell.com are: 230-ftp2.novell.com (United States) 230-ftp3.novell.com (United States) 230-ftp.novell.com.au (Australia) 230-ftp.novell.de (Germany) 230-ftp.novell.co.jp (Japan) 230-ftp.novell.nl (Netherlands) 230- 230-World Wide Web Novell Support sites: 230-http://support.novell.com (United States) 230-http://support.novell.com.au (Australia) 230-http://support.novell.de (Germany) 230-http://support.novell.co.jp (Japan) 230- 230-webmaster@novell.com 230- 230 Logged in anonymously. ftp> bye 221-Thank you and have a nice day. 221 C:\Documents and Settings\rshimonski>
-
Next, you can stop your sniffer. Examine the traffic it captured. Figure 8.4 clearly shows that FTP traffic has been captured and is being displayed. You should also be aware that you have captured a password with credentials in this capture. Figure 8.5 shows a close up of the captured password. All of this information comes from running the sniffer and capturing your logon.
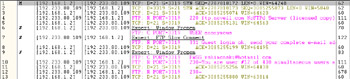
Figure 8.4: Viewing Captured FTP Data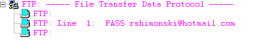
Figure 8.5: A Closer Look at the Captured Password
Scanning
A port is, in its simplest meaning, a point where information enters or leaves a computer. The TCP and UDP protocols use port numbers to provide separate "subaddresses" to identify what service or application incoming information is destined for or from which outgoing information originates.
The term port scanner, in the context of network security, refers to a software program that hackers use to remotely determine what TCP/UDP ports are open on a given system and thus vulnerable to attack. Scanners are also used by administrators to detect vulnerabilities in their own systems, in order to correct them before an intruder finds them. Network diagnostic tools such as the famous Security Administrator's Tool for Analyzing Networks (SATAN), a UNIX utility, include sophisticated port-scanning capabilities.
Scanning is used for several purposes prior to penetration and/or attack:
-
Target Enumeration Locating host systems that are open to attack
-
Target Identification Identifying the target system
-
Service Identification Identifying the vulnerable services or ports on the target system
A common saying among hackers is "A good port scanner is worth a thousand passwords." A good scanning program can locate a target computer on the Internet (one that is vulnerable to attack), determine what TCP/IP services are running on the machine, and probe those services for security weaknesses. Nmap (www.insecure.org/nmap) is a popular open source port scanner available free on the Web. Many scanning programs are available as freeware on the Internet. For a good resource for information about scanning and some popular scanning techniques and software, see www.garykessler.net/library/is_tools_scan.html.
Port scanning refers to a means of locating "listening" TCP or UDP ports on a computer or router and obtaining as much information as possible about the device from the listening ports. TCP and UDP services and applications use a number of well-known ports (see "Who's Listening?" the "On the Scene" sidebar in this section), which are widely published. The hacker uses his knowledge of these commonly used ports to extrapolate information.
For example, Telnet normally uses port 23. If the hacker finds that port open and listening, they knows that Telnet is probably enabled on the machine. They can then try to infiltrate the system by, for example, guessing the appropriate password in a brute force attack.
Who's Listening?
The official well-known port assignments are documented in RFC 1700, available on the Web at www.freesoft.org/CIE/RFC/1700/index.htm. The port assignments are made by the Internet Assigned Numbers Authority (IANA). In general, a service uses the same port number with UDP as with TCP, although there are some exceptions. The assigned ports were originally those from 0-255, but the number was later expanded to 0-1023.
Some of the most used well-known ports include:
TCP/UDP port 20: FTP (data)
TCP/UDP port 21: FTP (control)
TCP/UDP port23: Telnet
TCP/UDP port 25: SMTP
TCP/UDP port 53: DNS
TCP/UDP port 67: BOOTP server
TCP/UDP port 68: BOOTP client
TCP/UDP port 69: TFTP
TCP/UDP port 80: HTTP
TCP/UDP port 88: Kerberos
TCP/UDP port 110: POP3
TCP/UDP port 119: NNTP
TCP/UDP port 137: NetBIOS name service
TCP/UDP port 138: NetBIOS datagram service
TCP/UDP port 139: NetBIOS session service
TCP/UDP port 194: IRC
TCP/UDP port 220: IMAPv3
TCP/UDP port 389: LDAP
Ports 1,024-65,535 are called registered ports; these numbers are not controlled by IANA and can be used by user processes or applications. Some of these are traditionally used by specific applications (for example, SQL uses port 1,433) and could be of interest to hackers.
A total of 65,535 TCP ports (and the same number of UDP ports) are used for various services and applications. If a port is open, it responds when another computer attempts to contact it over the network. Port-scanning programs such as Nmap are used to determine which ports are open on a particular machine. The program sends packets for a wide variety of protocols, and by examining which messages receive responses and which do not, creates a map of the computer's listening ports.
| Test Day Tip | Please make sure you memorize basic port information for the SSCP exam. You do not have to be intimate with www.iana.org and its extensive port listing, but you should be familiar with basic well-known ports such as Telnet - 23, SMTP - 25, POP3 - 110, as well as the others listed within the chapter. |
Port scanning in itself does no harm to a network or system, but it provides hackers with information they can use to penetrate a network. Because people conducting port scans are often up to no good, they frequently forge the source IP address to hide their identity.
Should Scanning Be Illegal?
Some in the IT industry argue that port scanning should not be illegal, because "no harm is done." They say port scanning is similar to ringing someone's doorbell to see if anybody is home-not in itself a crime. However, laws are enacted not just to protect from actual physical harm but also to protect people's privacy and their interests in their own property. Those on the other side of the argument say that port scanning is really more like the virtual equivalent of someone who goes from door to door in an apartment building, trying each one to find out whether it is locked and whether there is an easy way in. Although this practice might not do any actual harm if the "door scanner" only collects information and does not enter the premises, and although the person might have the right to be in the public hallway, in most jurisdictions such behavior would, at the very least, cause discomfort to the apartments' residents and attract the attention of the police.
In 2000, in Moulton v. VC3, a U.S. District Court in Georgia ruled that port scanning does not damage a network and thus does not constitute a crime or create a cause of action for civil suit. Although the federal laws in regard to computer fraud and abuse were changed by the passage of the USA Patriot Act in 2001, there is still a requirement that loss or damage must occur in order to charge a violation. For more information on the ethics and legality of port scanning, see the article at http://rr.sans.org/audit/ethics.php on the SANS Institute's Web site. For an opinion paper that holds that scanning is not legal despite the Moulton ruling, see the article from the Journal of Technology Law and Policy at http://grove.ufl.edu/~techlaw/vol6/Preston.html.
Half scans (also called half open scans or FIN scans) attempt to avoid detection by sending only initial or final packets rather than establishing a connection. A half scan starts the SYN/ACK process with a targeted computer but does not complete it. (See the description of this process in the following section on TCP/IP exploits.) Software that conducts half scans, such as Jakal, is called a stealth scanner. Many port-scanning detectors are unable to detect half scans.
| Note | A good port-scanning resource for network administrators is www.doshelp.com/trojanports.htm, which details the ports that should be blocked for best security. |
|
|
EAN: 2147483647
Pages: 135