Goals of Information Security
|
|
What does the SSCP CBK say about the actual goals of security? Why do we work so hard and what are those things that every security professional strives for? Security experts agree that there are three main goals within information security towards which everyone works. Loss of any of these things can impact an organizations ability to function. These are also referred to as CIA and are considered the most important characteristics of a secure network:
-
Confidentiality
-
Integrity
-
Availability
| Test Day Tip | Confidentiality, integrity, and availability are the CIA of security. Although other pieces of the puzzle, such as non-repudiation and accountability are also important, they are most often considered to be directly integrated into one of the three base concepts of CIA. If the question appears on the exam, do not confuse availability with accountability. |
Confidentiality
Confidentiality means that the information on the system or network is safe from disclosure to unauthorized individuals. We have maintained confidentiality when we successfully ensure that no individuals are looking at or using information they are not authorized to access. The loss of confidentiality could have detrimental effects on the organization.
The Department of Defense (DoD) considers a loss of confidentiality as something that could negatively impact the security of the entire nation. When considered on a corporate level, the loss of confidentiality could lead to a poor corporate reputation or potentially the demise of the organization. As an example, consider the results if a bank lost the confidentiality of the customer records stored on its information systems. Patient privacy within the medical industry is also an issue of confidentiality.
As an example, consider a Human Resource department within a large organization that is pursuing a sexual harassment complaint. All of the information associated with the complaint is considered highly sensitive, including:
-
The complaint itself
-
Information on the person making the complaint
-
Information on the accused
-
And any other information concerning activities towards resolution
Inadvertent disclosure could result in embarrassment to the parties or public relations issues. The Human Resources person working the case accidentally leaves the information out on the desk overnight. The cleaning staff comes in later in the evening and finds the documentation. At this point, confidentiality of the information has been lost. Individuals with no authorization to view the information have had access to it. This type of incident could result in civil suits against the organization for improper handling of privacy information or severe damage to the reputation of the organization.
Integrity
Integrity of information within an organization means the information is whole and complete and has not been altered in any way, except by those authorized to manipulate it. The integrity of a computer or information system could impact the integrity of the critical information contained therein. Losing the integrity of a system or the information in that system means that the information can no longer be trusted.
Consider how important it is to know that the financial records the bank keeps on a person's account maintains their integrity. Mistakes in an account, intentional or unintentional, could cause a person to lose trust in the bank. Computer forensics also depends heavily on the integrity of data and evidence gathered in an electronic investigation. The loss of integrity of that evidence will mean it cannot be trusted and will most likely be thrown out of court as unreliable.
The violation of integrity can be either intentional or accidental. Employees of an organization that inadvertently make changes to customer information violate integrity because those changes are not authorized and may not be correct. Defacement of a Web site is an intentional violation of an organization's integrity by an outsider. If the Web site is a financial or news site, the information on that site becomes suspect due to the intrusion. When a customer cannot trust the content on an organization's Web site, the organization is in danger of losing those customers and facing a public relations nightmare.
Availability
Availability is just as important as confidentiality and integrity. Availability is having the information available right when it's needed. When availability is considered with respect to the critical information within an organization, it is easy to see why it becomes so crucial that it is always there when it is needed. An easier way to think of this is to consider availability as the inability of an intruder to take access of the data away from legitimate users on the system.
Consider the electrical utility co-op that provides power to a large region of the country; the power company relies on the availability of information on electricity production, especially supply and demand. Loss of availability of that information means they cannot adequately perform their mission and could result in an under-production of electricity and rolling blackouts.
A violation of availability could be as simple as failing to back up critical data within an organization. If primary servers experience a power surge that knocks out their hard disks, the information on those disks may not be available when it is needed for mission completion. An intruder could cripple an organization by making critical information unavailable when it is required. Denial of service (DoS) attacks violate availability by making important servers unavailable to the organization or customers.
Access Control
There are three types of access control mechanisms intended to help ensure the CIA of a system. They are Mandatory Access Control (MAC), Discretionary Access Control (DAC), and Role-based Access Control (RBAC). Each method uses a different implementation of access control to protect the system.
Mandatory Access Control
Mandatory access controls (MACs) are generally hard-coded into the operating systems being used on the system. Versions of UNIX, Linux, Windows, BSD, and mainframe operating systems all contain MAC processes. When users log in, they are prompted for their username and associated password. Once authenticated to the system, access to files, peripherals, objects, or processes is restricted to only those allowed by their access level. The processes within the system are also subject to the MAC within the system. Neither the owner nor the user of the system can change the way that MAC operates within the system, thus it become non-discretionary.
MAC allows for a high level of granularity when defining the various access levels within the system. Access to all objects within the operating system is controlled by these access levels. These access levels are universally applied to every object within the system. In some instances, even the applications residing on the system may have MAC hard-coded to add an extra layer of security within the system.
Consider a server that has a mission critical database service running that processes data considered highly sensitive to an organization. Normal users will not have access to the database files or the database processes running on the system. This is controlled by MACs. Furthermore, the processes created by normal users within the system will not be allowed access to the database files and processes. However, when database administrators or system administrators log in to the system, the access levels assigned to them by MAC will allow them to manipulate the data and/or the processes as necessary.
Discretionary Access Control
DACs are those that are implemented by the users on the system. They are not hard coded and are not automatically implemented within the system. DAC only works for those objects (processes, files, and so on) that are owned and controlled by the user. A normal user cannot change the access levels for objects already defined through MAC, unless they are the owners of those objects. And, as opposed to MAC, DAC levels that have been defined by the user can also by the user to someone else on the system. These access levels are completely discretionary and controlled by the user who created them.
For example, UNIX systems automatically protect critical system files and processes by allowing only administrators on the system to alter those objects. Normal users utilizing the system, however, must be allowed to create their own objects (files or processes) in order to perform their work-related duties. For each file a normal user creates, they obtain DAC privileges. Users can restrict access to themselves only, or they can allow the entire world to read or execute the object. DAC levels are not hard coded into the operating system, but are assigned by the owner of the system.
Role-based Access Control
RBAC is implemented based on the "group" concept. Users are put into groups by the system owner. Access to the various objects within the system is granted based on the access levels given to the group. Group-based control is common to most operating systems, including Windows, UNIX, Linux, and NetWare. But RBAC actually goes a step further because the "group" concept lacks the granularity that helps ensure security within a system.
Roles are defined within the system based on the use required by each job function within the organization. Access levels are then defined for each role. As opposed to groups, where every user in a group has the same access, RBAC restricts access to objects based on the job function (or role) for the individual.
Exercise 3.01: Viewing Discretionary Access Control Settings on UNIX
Current versions of most operating systems allow users and/or administrators to view the DAC levels on file and objects within the system. The only real restriction is your current level of access and on which objects you can view these settings. For this exercise, you will use a general UNIX-based command to allow a user to view these permissions. This exercise should work with most any version or UNIX, including Linux and BSD distributions.
Access control under UNIX is granted for read, write, and execute (RWX) on all objects. Some objects are assigned default settings when a system is installed, and may only be viewed or changed by the administrator of the server. Others are set by the user creating the object. RWX is also broken out into three groups of access for each object; owner, group, and other.
The owner is the individual that creates and/or owns the object on the system. The group consists of whatever access groups the individual is a member of, such as the "wheel" group, which is sometimes used for groups of individuals with administrator (root) access to the box. other is comprised of everyone else.
Let's try an example:
Once you have logged in to the UNIX server, you want to list the files and objects that exist in the current working directory. By using the correct syntax of the list command, you can also view the DAC level associated with each object.
test_system:/etc >ls –l total 1668 -rw-r--r-- 1 root root 20 Aug 11 16:25 HOSTNAME drwxr-xr-x 15 root root 4096 Jun 13 2002 X11/ -rw-r--r-- 1 root root 2561 Feb 24 2002 a2ps-site.cfg -rw-r--r-- 1 root root 15067 Feb 24 2002 a2ps.cfg drwxr-xr-x 3 root root 4096 May 16 2002 acpi/ -rw-r--r-- 1 root root 49 Nov 25 06:49 adjtime -rw-r--r-- 1 root root 14021 Oct 31 13:51 analyze.conf
We ran the command ls –l on the /etc directory. What you see here is just a small piece of the actual output. If you look at the first file, "HOSTNAME," you see that the permissions are -rw-r- -r- -. The first dash in the permissions output tells you what type of object it is. If it lacks a character, then the object is a simple file. After this point, the characters are broken into the three sets of RWX; owner, group, and world.
Looking back at the file "HOSTNAME," we see that the owner of the file (who happens to be root) has both read and write access to the file. The group that root belongs to (the root group) has the next three chracters, r- -. This means that the group "root" only has read access to the file. The last three sets of characters define the access level granted to everyone else (world). The world group also has permissions of r- - so they are only allowed to read the file.
It should be noted that even though the world of the file appears to only have read and write access to the file, the owner can still control the discretionary access levels on that file. They can grant themselves the right to execute the file as well. Users in the group and world designations do not have that same right and will not be allowed to manipulate the DAC on objects they do not own.
The permissions on these files can be extremely important to system security. Having the wrong world permissions on a file or directory can make a system easier to compromise. As a quick example, Web site files with world permissions mean that anyone or any process on the system can alter those files and change the Web site.
Consider the Entire Life Cycle of Information
Along with the concepts of CIA, it is important to understand that good security does not come easily. You cannot implement a single security tool and expect that to be the end. Security works in a continuous cycle of improvement where new security models are tested and adjustments made for further improvement.
An often-used life cycle model for information security is illustrated in Figure 3.1 and consists of the following steps:
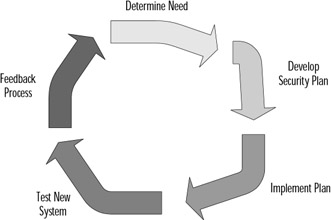
Figure 3.1: The Life Cycle of Information Security
-
Analysis of current system to determine need.
-
Development of security implementation plan to fit needs.
-
Implementation of security components within the plan.
-
Testing process of security implementation.
-
Feedback process provides suggestions for improvement of system.
-
Cycle starts over from the top.
The life cycle provides security organizations with a methodology to continue progression towards the most secure system possible while still allowing the system to function. Through this constantly revolving process, security administrators continually come closer and closer to their goal of a system that is both functional yet secure. Always remember that security is a process, not a destination. Initially, when the security process begins, significant progress will result. Figure 3.2 shows how the progress associated with the information assurance process slows down dramatically after an initial level of effort. After this time, the security of the organization steadily improves at a slower pace with an increased level of effort.
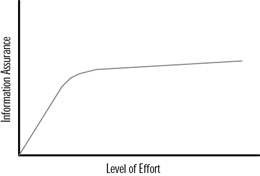
Figure 3.2: Impact of Effort on Information Assurance
|
|
EAN: 2147483647
Pages: 135