Chapter 6. Solaris Security
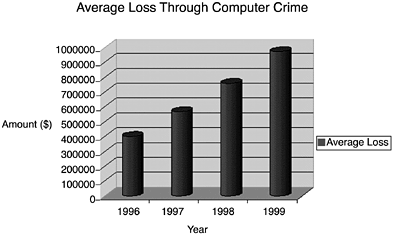
| B USINESSES AROUND THE WORLD ARE MAKING as much use as possible of Internet technologies to break into new global markets. As companies become ever more dependent on the Internet for their business relationships, the importance of computer security increases as well. More and more people and businesses are connecting every day, and with that comes more potential for security threats. Single-site, centralized data centers, with equally centralized security requirements, are fast disappearing and are being replaced by new, modern, distributed corporations with sites not just in different towns and cities, but in different countries as well, all communicating together and sharing confidential company information. It is a system cracker's paradise if there is no security policy in place ”they can just march in and wreak havoc. Hacker or Cracker The term hacker is usually referred to in the news as an external malicious attacker of computer systems. Within the IT industry however, the term cracker is used to define the malicious attacker or virus perpetrator. A hacker is someone who is not malicious but who, through unsupervised access, can often cause unintentional damage to a computer system, normally because of inexperience rather than a deliberate action. That distinction between the two concepts is used in this text. But it's not the external cracker who actually causes the most damage; those instances are merely the most widely reported . Perhaps surprisingly, various studies have shown that by far the largest cause of security incidents comes from within ”that is, someone already authorized to use the computing resources of a company, such as a disgruntled employee who was passed over for promotion or was refused a raise. This employee could do something as simple as delete important files, for example, but a more sophisticated employee could write and introduce a destructive virus into the system. The possibilities are many. The Computer Crime and Security Survey, carried out each year in the United States by the Computer Security Institute/Federal Bureau of Investigation (CSI/FBI), analyzes and highlights the effect of computer crime/abuse. The findings clearly show a marked increase each year. To put this into perspective, Figure 6.1 shows the average financial loss suffered for the last four years as a result of computer crime. The average loss is taken from the number of companies that were able to put a dollar value on the loss encountered . Figure 6.1. The disturbing upward trend toward computer crime highlights the need for increased computer security and incident reporting. The system manager is responsible for maintaining the integrity of the systems that he manages and for ensuring that there is no unauthorized access to confidential data. In larger corporations, the system manager might be assisted by a dedicated computer security section, whose role is to implement a company security policy. Sadly, a large number of businesses do not have a corporate policy, and various departments implement their own ad hoc computer security, often lacking consistency and the capability to ensure that it is enforced. This chapter aims to address some of the issues surrounding the need for better security in a Solaris environment, and it takes a brief look at some of the security products that are available ”both with the Solaris operating environment and also from the public domain. |
| Top |
EAN: 2147483647
Pages: 101