12.5 Bluetooth Security
| Bluetooth offers three different modes of security.
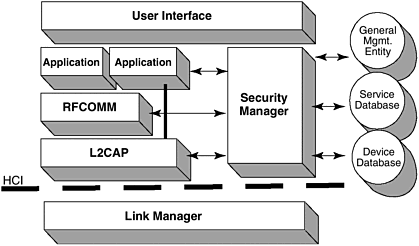
Security Mode 1 is a nonsecure mode. Security Mode 2 is handled by higher layers based on the access policies and procedures defined at the service levels. No security procedures are initiated before channel establishment on the L2CAP level. Security Mode 3 involves link-level security procedures before the link is set up and before the channels are established. Figure 12-8 shows the security architecture. The security manager is the key functionality that manages the security keys and performs security procedures for different protocol layers. The rest of the security discussion is limited to Mode 3. Figure 12-8. Bluetooth security architecture. Table 12-2 shows the four different entities that are used for maintaining security at the link layer: a public address that is unique for each Bluetooth device, two secret keys, and a random number that is different for each new transaction. The secret keys are derived during initialization and are further never disclosed. Normally, the encryption key is derived from the authentication key during the authentication process; however, the encryption key can also be regenerated when needed. The authentication algorithms are based on 128 bits. For encryption algorithms, the key size can vary between 1 and 16 octets (8-128 bits) to accommodate different cryptographic algorithms in different countries , but the size is fixed for a specific device unit. The encryption key length is negotiated between the master and the slave devices to an acceptable size in octets as determined by the each application. The RAND is a random number generated by a pseudorandom generator in the Bluetooth unit. Table 12-2. Entities Used to Maintain Security at the Link Layer
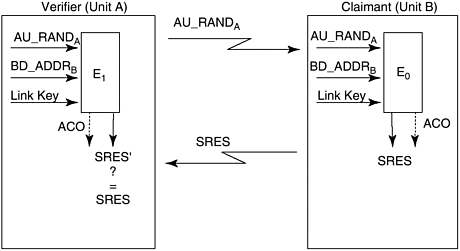
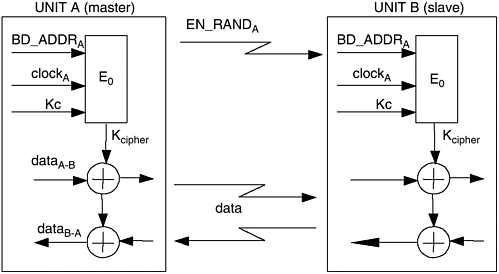
Bluetooth security is not foolproof and has some limitations. For instance, it performs only device authentication but does not support user-level authentication; however, it can be implemented at higher layers. Another aspect relates to lack of support for unidirectional traffic, although the access control checks can be performed asymmetrically at connection setup. 12.5.1 AuthenticationThe entity authentication in Bluetooth uses a challenge-response scheme in which the claimant's knowledge of a secret key is checked through a two-move protocol using symmetric keys, as shown in Figure 12-9. The verifier, either the master or slave, challenges the claimant to authenticate a random input, AU_RAND A , with an authentication code, E 1 , and return the result SRES to the verifier. This value is verified against the one, SRES', generated by the verifier itself. Figure 12-9. Challenge response authentication. The link key is the current link key shared by the A and B Bluetooth units. The use of BD_ADDR B is to prevent a simple reflection attack. For a successful authentication, the value of ACO (authenticated ciphering offset) is retained. This authentication mechanism is only one way. Certain applications need only one-way authentication. For peer-to-peer communications, both devices perform the authentication in each way to authenticate the other. 12.5.2 EncryptionEncryption is used to protect the user packet payload and is carried out with a stream cipher called E that is resynchronized for every payload. But the access code and the packet header are never encrypted. Figure 12-10 shows the encryption procedure. Figure 12-10. Encryption with E . The stream cipher system E consists of three parts : generation of payload key, generation of key stream bits, and encryption and decryption. The payload key generator simply combines the input bits in an appropriate order and shifts them into the four linear feedback shift registers (LFSRs) used in the key stream generator. In the second part of the cipher system, the key stream bits are generated by a method derived from the summation stream cipher generator attributable to Massey and Rueppel. The cipher algorithm E uses the master Bluetooth address, 26 bits of master real-time clock, and the encryption key K c as input. The random number, EN_RAND, is issued by the master as plaintext over the air. The encryption algorithm E generates a binary keystream , K cipher, which is modulo 2 added to the data to be encrypted. The cipher is symmetric; decryption is performed exactly the same way using the same key as the encryption. |
EAN: 2147483647
Pages: 164