Network Monitoring
|
|
Your network is vulnerable to all sorts of attacks and penetration efforts by attackers. Network-monitoring techniques help you track what is happening in your network. Monitoring can occur in real time (for example, when using a network sniffer) or by following events as they occur in your system using log files and security systems (when using an Intrusion Detection System).
More than likely, the building you occupy has a perimeter security system. This system might not keep a determined burglar from breaking into your building, but it will keep out most people. Most office buildings also have video cameras, motion detectors, and other devices to detect intruders and notify authorities about a break-in on your property. Your building probably has fire and smoke detectors, water sensors, and any number of other safety and security devices installed. All of this equipment, working together, provides a reasonably safe work environment. Your computers and network need the same things.
Network monitoring helps ensure a safe environment. You can help secure your computer's environment by installing tools to automatically monitor the environment and report unusual events that occur. You can monitor your network by merely reviewing system logs on a regular basis or by installing complex software that performs these activities for you and then reports anything unusual. This process is much like the fire suppression system in your building. When a fire is detected, elevators return to the basement, sprinklers automatically activate, and the local fire department is notified. When a computer security breach occurs, the network will isolate the affected systems, notify the administrators, and even attempt, if necessary, to shut down the systems.
Network monitoring on a regular basis is important to determine what types of events are occurring in your network. Without this information, you are really shooting in the dark. As a security professional, you want to primarily deal with what is happening in your network as it occurs. You also want to establish preventative measures to reduce the fear of the unknown.
The following section introduces you to the types of network traffic you will encounter on most networks. This includes a wide variety of protocols such as TCP/IP, IPX, and NetBEUI. Each of the protocols in this section operates with its own rules and methods. In general, these protocols do not interact with each other, and they are oblivious to the existence of the other protocols.
Types of Network Traffic
Your network probably uses several network protocols and services to communicate. This section will briefly explain which network protocols and services are common in networks. The most common protocol in use in Wide Area Networks today is the TCP/IP protocol. Many networks also run protocols unique to Novell, Microsoft, Network File Systems, and AppleTalk. This section will introduce you to these protocols and identify potential threats to your networks.
TCP/IP
As you may recall, the TCP/IP protocol suite supports a wide variety of protocols used to transport information inside and outside the LAN. The protocols that are the most susceptible to attacks are IP, TCP, UDP, ICMP, and IGMP. Chapter 2, "Know Your Enemy," discussed these protocols in detail. The important thing to remember is that each of these protocols may be vulnerable because of the unsecure nature of TCP/IP or a weakness in the implementation of the protocol by the software manufacturer.
Novell
Novell, Inc. has long been a significant player in the network environment with its NetWare product line. NetWare, a server-based environment, offers both network protocols, services, and applications. Novell is a bitter rival of Microsoft, and they have a large and loyal following. In addition to TCP/IP, NetWare supports two proprietary protocols:
IPX/SPX Internetwork Packet Exchange (IPX) and Sequenced Packet Exchange (SPX) are two of the proprietary protocols unique to Novell 4.x and earlier networks. IPX and SPX are common protocols in both large and small networks. These protocols are very fast and efficient, and they are well documented. They are also susceptible to communications interception using internal monitoring.
NDS and eDirectory Novell introduced a directory management service called NetWare Directory Services (NDS) to manage all of the resources in a network. NDS provides a database of all of the network objects or resources. Figure 4.1 shows an NDS tree. The key point to remember here is that NDS is a network-based service. Notice that the NDS tree treats print devices, disk volumes, users, and groups as leaf objects, or resources, in the tree. Earlier versions of NetWare used bindery services. The bindery kept track of resources on a server-by-server basis.
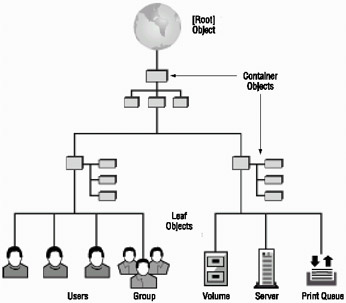
Figure 4.1: A typical NDS tree structureIn the newer versions of NetWare, NDS has been expanded to a service called eDirectory. Novell changed the environment so that it now operates using TCP/IP as the native network protocol.
Novell also provides a number of applications, tools, and products that compare favorably to other network-based products. Two of the more popular Novell products are GroupWise, an e-mail and collaboration system similar to Microsoft Exchange, and a software and configuration distribution product known as ZENWorks. NetWare is susceptible to DoS attacks, as are most TCP/IP-based environments.
Microsoft
Microsoft and IBM were early leaders in PC network technologies. Early PC systems supported a rudimentary peer-to-peer networking environment that was very fast and required little overhead. Of course, networks in those days were very simple and high levels of functionality were not expected. The two original network protocols available for PCs were NetBIOS and NetBEUI. This section also includes a brief discussion of the WINS Service. Although WINS is not technically a protocol, it is an integral part of the traffic on a Microsoft network.
NetBIOS Network Basic Input Output System (NetBIOS) is the native protocol of Windows PCs. NetBIOS provides a 15-character naming convention for resources on the network. NetBIOS is a broadcast-oriented network protocol, in that all traffic is available to all devices in a LAN. The protocol can be transported over NetBEUI, TCP/IP, or IPX/SPX.
NetBEUI The NetBIOS Extended User Interface (NetBEUI) is used to transport NetBIOS traffic in a LAN. NetBEUI and NetBIOS were originally packaged as a single product. As network technologies advanced, NetBIOS was turned into a separate protocol. NetBEUI is a nonroutable protocol. NetBEUI traffic is easy to intercept internally using a network sniffer. Figure 4.2 shows a network running only NetBEUI.
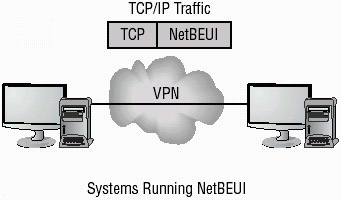
Figure 4.2: NetBEUI network using a VPN over a TCP/IP networkWINS Service The Windows Internet Naming Service (WINS) translates NetBIOS addresses to TCP/IP addresses. WINS runs as a service on a server, such as Windows 2000 Advanced Server. WINS provides name translation for networks, similar in nature to DNS. If WINS is not available, a Windows system can use a local file, such as a LMHOSTS, to resolve NetBIOS names to TCP/IP addresses. In Figure 4.3, a WINS server provides a NetBIOS name to TCP/IP addresses in a LAN. This resolution process has been coupled by DNS with Windows 2000 products.
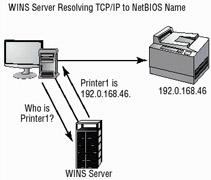
Figure 4.3: WINS Server resolving TCP/IP addresses to names
Over the years, Microsoft has introduced a number of other protocols and services to facilitate communication between Windows network systems. Microsoft has stated that future network products will utilize TCP/IP, which is now replacing most of these protocols.
Network File System
Network Files System (NFS) is the default file-sharing protocol for UNIX systems. NFS allows a remote user to mount drives on a machine in the network. To be secure, NFS requires a special configuration. NFS is also referred to as Distributed File System (DFS). Figure 4.4 shows a remote system mounting a drive on a local machine using NFS.
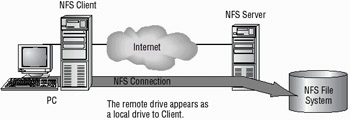
Figure 4.4: An NFS device being mounted by a remote UNIX system
| Note | NFS will be discussed in greater detail in Chapter 5, "Implementing and Maintaining a Secure Network." |
Apple
Apple Computers has been a network player for many years. The Apple networking protocol, AppleTalk, is a routable protocol (although it has a lot of routing overhead), and it has been a standard on Apples and Apple printers for many years. Most manufacturers of network products support the Apple- Talk protocol, which is not intended for secure applications. Modern Mac systems can also use TCP/IP for connections.
Network Monitoring Systems
Several monitoring mechanisms are available to track traffic. Monitoring can occur on individual systems, on servers, or as a separate component of the network. The connection used when monitoring occurs on a network is called a tap. Figure 4.5 illustrates some of the places where a network tap can occur. Each location presents a different view of the network. For an effective security process, multiple taps are probably needed.
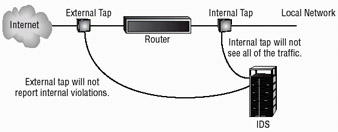
Figure 4.5: Tap locations used to monitor network traffic
Your system faces both internal and external threats. If all of your monitoring activities are oriented toward external threats, discovering internal security breaches as they occur may be difficult.
In a busy network, identifying what types of activities are occurring is very difficult because of the sheer volume of traffic. Heavy traffic makes it necessary to dedicate personnel to monitoring. Network activity is also reported in systems logs and audit files. Although it is a good practice to periodically review these files, doing so can be a daunting and extremely boring undertaking at times. Automated tools, which will make this process more manageable, are coming to the market.
|
|
EAN: 2147483647
Pages: 167