Attack Strategies
|
|
An attack occurs when an individual or a group of individuals attempts to access, modify, or damage your systems or environment. These attacks can be fairly simple and unfocused, or they can appear to be almost "blitzkrieg" in their intensity.
Attacks occur in many different ways and for different reasons. These attacks generally try to accomplish one or more of these three goals:
-
An access attack is one in which someone wants access to your resources.
-
A modification and repudiation attack is one in which someone wants to modify information in your systems.
-
A denial of service attack is one in which someone wants to disrupt your network and services.
The people attacking you may be attacking you for the fun of it, they may be criminals attempting to steal from you, or they can be individuals or groups who are using this attack to make a political statement or commit an act of terrorism. In any event, your job is to protect the people you work with from these acts of aggression. You are, in many cases, the only person in your organization charged with the responsibility of repulsing these attacks.
This section deals with the general types of attacks you will see.
Access Attacks
The goal of an access attack is straightforward. Access attacks are an attempt to gain access to information that the attacker is not authorized to have. These types of attacks focus on breaching the confidentiality of information. These attacks occur either through internal or external access. These attacks also occur when physical access to the information is possible.
Dumpster diving is a very common physical access method. Companies generate a huge amount of paper in the normal course of events. Most of the information eventually winds up in dumpsters or recycle bins. These dump- sters may contain information that is highly sensitive in nature. In high security and government environments, sensitive papers are either shredded or burned. Most businesses do not do this. The advent of "green" companies has created an increase in the amount of recycled paper. This paper may contain all kinds of juicy information about a company and the individuals in the company.
A second common method used in access attacks is to capture information en route between two systems. Some common types of these access attacks include:
Eavesdropping Eavesdropping is the process of listening in or overhearing parts of a conversation. Eavesdropping also includes attackers listening in on your network traffic. This type of attack is generally passive. A coworker may overhear your dinner plans because your speakerphone is set too loud. Eavesdropping is a passive process in which the opportunity to overhear a conversation meets the carelessness of the parties in the conversation.
Snooping Snooping occurs when someone looks through your files in the hopes of finding something interesting. These files may be either electronic or paper. In the case of physical snooping, people might inspect your dumpster, recycling bins, or even your file cabinets. Computer snooping, on the other hand, involves someone searching through your electronic files trying to find something interesting.
Interception Interception can be both an active or passive process. In a networked environment, a passive interception would involve someone who routinely monitors network traffic. Active interception might include putting a computer system between the sender and receiver to capture information as it is sent. From the perspective of interception, this process is a covert process. The last thing a person on an intercept mission wants is to be discovered. Intercept missions can occur for years, without the knowledge of the intercepted parties.
Government agencies routinely run intercept missions to gather intelligence about the capabilities and locations of enemies. The FBI has several products that they install on ISPs to gather and process e-mail looking for keywords. These keyword searches become the basis of an investigation.
The major difference in these types of attacks is how they are accomplished. The ultimate objective is to gain access to information that is not authorized.
Modification and Repudiation Attacks
Modification attacks change or modify information in an unauthorized manner. These attacks are similar to access attacks in that these attacks require access to information on servers. The motivation for this type of attack may be to plant information, change grades in a class, fraudulently alter credit card records, or any number of other reasons. A variation of a modification attack is a repudiation attack.
Modification attacks involve the deletion, insertion, or alteration of information in a manner that appears genuine to the user. These attacks can be very hard to detect. In general, the attacker enters your system using an access attack and then proceeds from there. Website defacements are a very common form of modification attack.
Repudiation attacks make data or information that is used invalid or misleading, which can be even worse. An example of a repudiation attack might be someone accessing your e-mail server and sending inflammatory information to others. This information can prove embarrassing to you or your company if this happens. Repudiation attacks are fairly easy to accomplish because most e-mail systems do not check outbound mail for validity. Repudiation attacks usually begin as access attacks.
A common type of repudiation attack would involve a customer who claims that they never received a service for which they were billed. In this situation, the burden of proof is on the company to prove that the information used to generate the invoice is accurate. If the data has been modified by an external attacker, accuracy verification of the information may be difficult.
Denial of Service Attacks (DoS)
Denial of service (DoS) attacks prevent access to resources by users authorized to use those resources. An attacker may attempt to bring down an e-commerce website to prevent or deny usage by legitimate customers. DoS attacks are very common on the Internet. They have hit large companies such as Amazon, Microsoft, and AT&T. These attacks are often widely publicized in the media. Most simple DoS attacks occur from a single system, and a specific server or organization is the target.
Several different types of attacks can occur in this category. These attacks can deny access to information, applications, systems, or communications. In a DoS attack on an application, the attack may bring down the website while the communications and systems continue to operate. In a denial of access to a system, the operating system is crashed. A simple reboot may restore the server back to normal operation. A DoS attack against a network is designed to fill the communications channel and prevent authorized users access. A common DoS attack involves opening as many TCP sessions as possible. This type of attack is called a TCP SYN flood DoS attack.
An attack that is similar in objective is called a Distributed Denial of Service Attack. This type of attack amplifies the concepts of a DoS by using multiple computer systems to conduct the attack.
Distributed Denial of Service Attacks (DDoS)
A relatively new type of DoS attack called a Distributed Denial of Service Attack (DDoS) uses multiple computers to attack a single organization. These attacks exploit the inherent weaknesses of dedicated networks such as DSL and cable. These permanently attached systems do not usually have much, if any, protection. An attacker can load an attack program onto dozens or even hundreds of computer systems that use DSL or cable modems. The attack program will lay dormant on these computers until they get an attack signal from a master computer. This signal triggers these systems, which launch an attack simultaneously on the target network or system. Figure 2.1 shows an attack occurring and the master controller orchestrating the attack. The master controller may be another unsuspecting user. The systems taking direction from the master control computer are referred to as zombies. These systems merely carry out the instruction they have been given by the master computer.
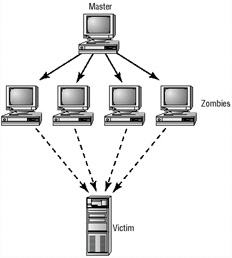
Figure 2.1: Distributed Denial of Service attack
The nasty part of this type of attack is that the machines used to carry out the attack belong to normal computer users. The attack gives no special warning to those users. When the attack is complete, the attack program may remove itself from the system or infect the unsuspecting user with a virus that destroys the hard drive, thereby destroying the evidence.
In general, there is very little you can do to prevent DoS or DDoS attacks. Your best method of dealing with these types of attacks involves countermeasures and prevention. Many operating systems are particularly susceptible to these types of attacks. Fortunately, most operating system manufacturers have implemented updates to minimize the effects of these types of attacks. Make sure that your operating system and the applications you use are up to date and current.
Common Attacks
The common attacks that are encountered in a system are briefly described in this section. These attacks are designed to exploit potential weaknesses in the implementation of programs, as well as weaknesses in the protocols used in networks. Many of these types of attacks require a high level of sophistication and are rare. You need to know about them so that you can identify what has happened in your network.
Back Dor Attacks
The term back door can have two different meanings. The original term back door referred to troubleshooting and developer hooks into systems. During the development of a complicated operating system or application, programmers add back doors or maintenance hooks. These back doors allow them to examine operations inside the code while the code is running. The back doors are stripped out of the code when it is moved to production. When a software manufacturer discovers a hook that has not been removed, they release a maintenance upgrade or patch to close these back doors. These patches are very common when a new product is initially released.
The second type of back door refers to the entry and placement of a program or utility into a network that creates a back door for an attacker. These attacks are initiated by gaining access to a network and inserting a program or utility that creates the back door for the attacker. The program may allow a certain user ID to log on without a password, or gain administrative privileges. Figure 2.2 shows how a back door attack can be used to bypass the security of a network. In this example, the attacker is using a back door program to utilize resources or steal information.
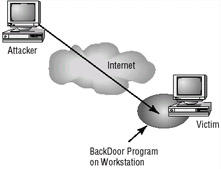
Figure 2.2: A back door attack in progress
In either case, this attack is usually used as either an access or modification attack. A number of tools exist to create back door attacks on systems. One of the more popular tools used to create backdoors is Back Orifice. Back Orifice has been updated to work with Windows 2000. Another popular backdoor program is NetBus. Fortunately, a lot of conventional antivirus software will detect and block these types of attacks.
| Note | Back Orifice and NetBus are remote administration tools used by attackers to take control of Windows systems. These packages are typically installed using a Trojan Horse program. BO and NetBus allow a remote user to take full control of the systems that have these applications installed. Back Orifice and NetBus run on all of the current Windows operating systems. |
Spoofing Attacks
A spoofing attack is simply an attempt by someone or something to masquerade as someone else. This type of attack is usually considered an access attack. A very common spoofing attack that was popular for many years involved a programmer writing a fake logon program. This program would prompt the user for a user ID and password. No matter what the user typed, the program would indicate an invalid logon attempt and then transfer control to the real logon program. The spoofing program would write the logon and password into a disk file, which was retrieved later. This attack was very popular on early UNIX and other timesharing systems. Figure 2.3 shows a spoofing attack occurring as part of the logon process on a computer network. The attacker in this situation impersonates the server to the client attempting to login. No matter what the client attempts to do, the impersonating system will fail the login. When this process is finished, the impersonating system disconnects from the client. The client then logs into the legitimate server. In the meantime, the attacker now has a valid userid and password.
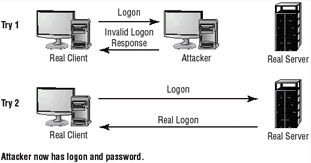
Figure 2.3: A spoofing attack during logon
The important point to remember is that a spoofing attack is accomplished to trick something or someone into thinking something legitimate is occurring.
Man in the Middle Attacks
Man in the middle attacks tends to be fairly sophisticated. This type of attack is also an access attack, but it can be used as the starting point for a modification attack. The method used in these attacks places a piece of software between a server and the user. The software intercepts and then sends the information to the server. The server responds back to the software, thinking it is the legitimate client. The attacking software then sends this information on to the server, etc. The man in the middle software may be recording this information, altering it, or in some other way compromising the security of your system. Figure 2.4 illustrates a man-in-the-middle attack. Notice how both the server and client assume that the system they are talking to is the legitimate system. The man in the middle appears to be the server to the client, and to be the client to the server.
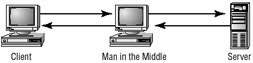
Figure 2.4: A man in the middle attack occurring between a client and a web server
Replay Attack
Replay attacks are becoming quite common. These attacks occur when information is captured over a network. Replay attacks are used for access or modification attacks. In a distributed environment, logon and password information is sent between the client and the authentication system. The attacker can capture this information and replay it again later. This can also occur with security certificates from systems such as Kerberos. The attacker resubmits the certificate hoping to be validated by the authentication system. Figure 2.5 shows an attacker presenting a previously captured certificate to a Kerberos-enabled system. In this example, the attacker gets legitimate information from the client and records it. Then, the attacker attempts to use the information later to enter system. The attacker later relays information to gain access.
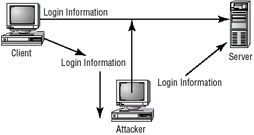
Figure 2.5: A replay attack occurring
If this attack is successful, the attacker will have all of the rights and privileges from the original certificate. This is the primary reason that most certificates contain a unique session identifier and a time stamp. If the certificate has expired, the certificate will be rejected and, hopefully, an entry made in a security log to notify system administrators.
Password Guessing Attacks
Password guessing attacks occur when an account is attacked repeatedly. This is accomplished by sending possible passwords to the account being attacked in a systematic manner. These attacks can occur using either a brute force or a dictionary method, and are initially done to gain passwords for an access or modification attack. The two types of password guessing attacks are:
Brute Force Attack A brute force attack is an attempt to guess passwords until a successful guess occurs. This type of attack usually occurs over a long period. Passwords should be longer than two or three characters. This makes it more difficult to guess a password.
Dictionary Attack A dictionary attack is an attack which uses a dictionary of common words to attempt to find the password of a user. Dictionary attacks can be automated, and several tools exist in the public domain to execute a dictionary attack.
Some systems will identify whether an account ID is valid and whether the password is wrong. Giving the attacker a clue as to a valid account name is not a good practice. If you can enable your authentication to either accept a valid ID/password group or require the entire logon process again, you should.
|
|
EAN: 2147483647
Pages: 167
- ERP Systems Impact on Organizations
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Distributed Data Warehouse for Geo-spatial Services
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare
- Development of Interactive Web Sites to Enhance Police/Community Relations