Using Remote Desktop Access
| Windows NT Server 4.0 introduced the Terminal Services capability that allows Windows Server to host multiple virtual terminal sessions, accessed by remote clients able to run on downlevel (earlier) versions of the Windows operating system. Applications running within each virtual terminal session operate on the server system; the mouse and keyboard of the client system provides input to the server while the video output is routed back to the client. Starting with Windows Server 2000, Terminal Services was implemented in two versions: application mode could be configured to allow multiple client systems to access a virtual terminal running under a licensed Terminal Services session, whereas a limited-access version of the Terminal Services connectivity could be used by up to two concurrent users for the purposes of remote administration. This administrative mode did not require a Terminal Services Licensing server to function, and was loaded within the Add/Remove Programs wizard after server setup. In Windows XP, Microsoft introduced a client-accessible version called the Remote Desktop. This is a single-user modified version of the Terminal Services capability, enabling a user to connect to an existing console session on a remote Windows XP system. Windows Server 2003 introduces a more refined version of the Remote Desktop capability, merging enhancements from the Windows XP Remote Desktop Protocol (version 5.1) into the multiple-terminal capability of the full Terminal Services server. The new implementation of the Remote Desktop Protocol (version 5.2) adds a number of new options, such as
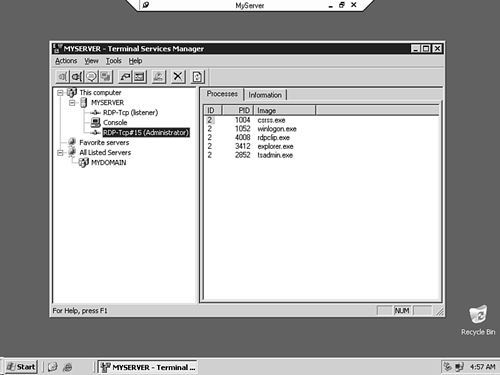
Terminal ServicesMicrosoft makes use of several components running on the Terminal Services host server to manage remote access, including
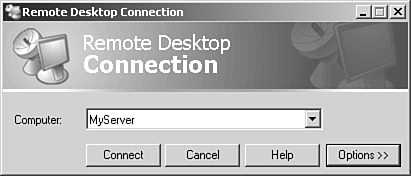
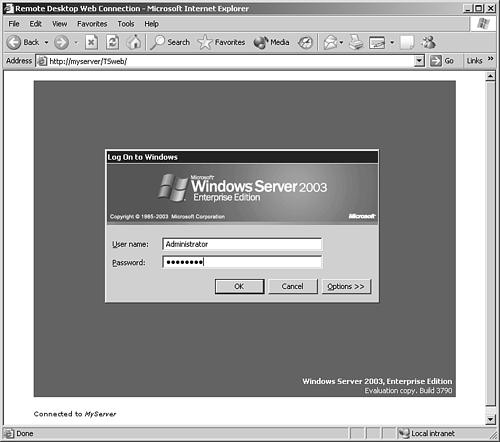
Microsoft has also included many new remote access options within the MMC snap-in utilities, as well as many policy settings. One security policy setting you might have noticed in Chapter 2 is Allow Login to Terminal Services Only, which restricts users to Remote Desktop connections only, rather than the Log on Locally permission that was mandated in Windows Server 2000 implementations . Remote Desktop ConnectionsClients can connect to a Microsoft Windows Server 2003 Terminal Server or Remote Desktop for Administration connection using the Remote Desktop client, shown in Figure 3.21, which is familiar to anyone who has used the interface between Windows XP systems. Figure 3.21. The Remote Desktop client in its basic form. By expanding the Options button on the RDC, it's possible to configure the connection's settings and then save the RDC settings as a shortcut that can be easily used by clients to open the preconfigured session, as shown in Figure 3.22. Figure 3.22. A Remote Desktop session to MyServer displaying the Terminal Services Configuration MMC snap-in showing this connection. In addition to the single-console RDC ( mstsc.exe ), Windows Server 2003 also includes the multi-connection Remote Desktops MMC snap-in utility (refer to Figure 3.1), as well as an ActiveX Web-based connection utility that can be used to open a Terminal Services connection using Internet Explorer, as shown in Figure 3.23. Figure 3.23. A Remote Desktop session to MyServer using the Remote Desktop Web Connection ActiveX component.
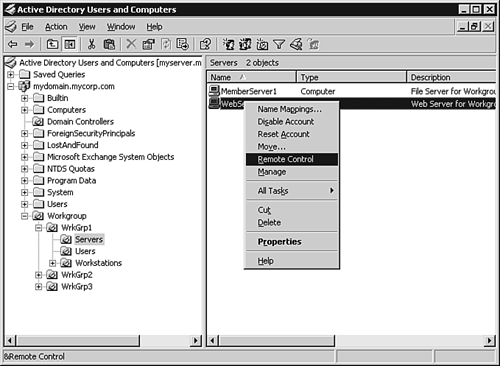
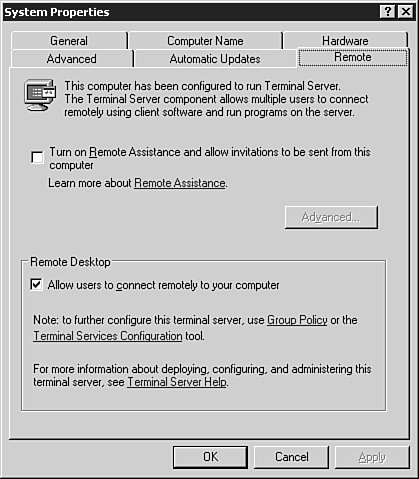
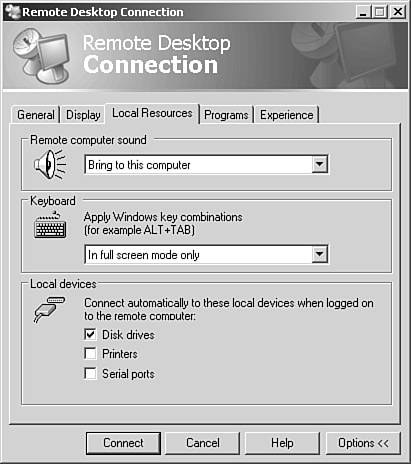
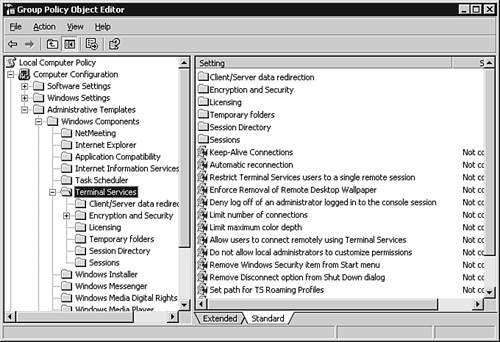
Microsoft has also provided an add-in to the Active Directory Users and Computers MMC snap-in that extends the Remote Control functionality to this administration utility, as shown in Figure 3.24. This additional component can be downloaded at the following Web site: http://www.microsoft.com/downloads/details.aspx?FamilyID=0a91d2e7-7594-4abb-8239-7a7eca6a6cb1&DisplayLang=en. Figure 3.24. The Remote Control option added to the Active Directory Users and Computers MMC snap-in. Allowing Remote ConnectionsBefore any remote terminal sessions can be created, it's first necessary to allow users to connect remotely to your computer, which is accomplished on the Remote tab of a server's System Properties dialog box, as shown in Figure 3.25. Figure 3.25. The Remote tab of the System Properties dialog box. User accounts must be granted the proper permissions to connect via Remote Access, which can be accomplished by inheritance from membership in the Remote Desktop Users group. Additional Terminal Server settings can be configured within the Active Directory Users and Computers MMC snap-in for a user or group, through the RDP's advanced options (see Figure 3.26), through Group Policy settings (see Figure 3.27), and within the Terminal Server Configuration MMC snap-in (see Figure 3.28). Figure 3.26. Remote Desktop client environment options. Figure 3.27. Terminal Services GPO settings node within the Group Policy Object Editor. Figure 3.28. Terminal Server configuration within the Terminal Server Configuration MMC snap-in.
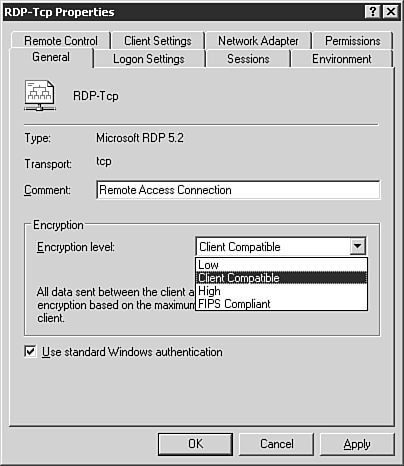
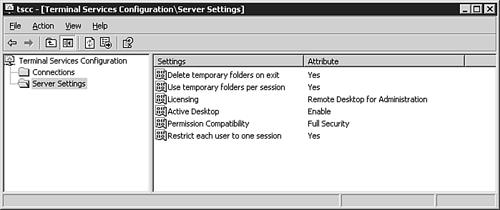
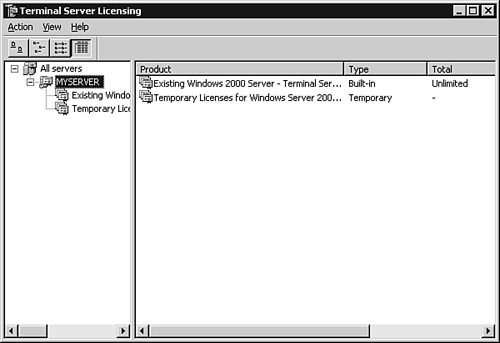
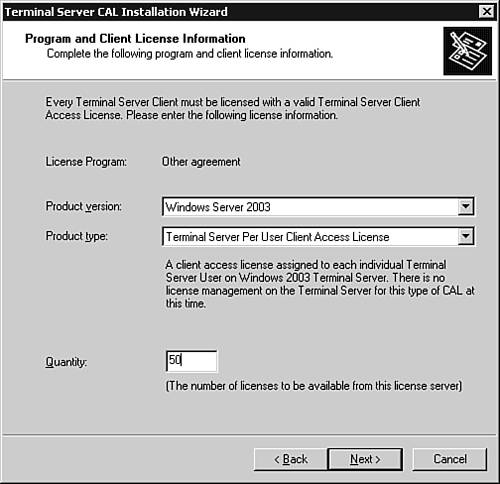
Configuring Terminal ServicesWhen Terminal Services will be used in Application mode, it is necessary to install the Terminal Services Configuration utility (see Figure 3.29) from within the Add/Remove Programs Wizard. The Terminal Services Licensing service (see Figure 3.30) can also be installed here if this server will be used to provide licensing for servers running the Terminal Services service within your enterprise, forest, or domain. Figure 3.29. The Terminal Services Configuration MMC snap-in. Figure 3.30. The Terminal Services Licensing MMC snap-in. After installation of the Terminal Services Configuration MMC snap-in, you can configure the properties of each connection available on a host server running the Terminal Server service. To utilize the licensing capability of a Terminal Services Licensing server, the server must first be activated within the Terminal Services Licensing MMC snap-in by right-clicking the target server and selecting Activate Server. Activation can be accomplished automatically, via HTTP connection, or by telephone. Connections that are not associated with Terminal Server licenses, such as those used for remote administration, will be displayed within the Temporary Licensing node of the Terminal Server Licensing MMC snap-in. When licenses are added, the type and quantity of each set of licenses must be provided (see Figure 3.31) along with the appropriate licensing key. Figure 3.31. The Terminal Server CAL Installation Wizard showing the installation of 50 licenses for Windows Server 2003 per-user licensing. When Terminal Server Licensing problems arise, it is possible to easily diagnose the current license allocation within this MMC snap-in as well. |
EAN: 2147483647
Pages: 132