19-11 ip ospf message-digest-key key-id md5 password
| < Free Open Study > |
19-11 ip ospf message-digest-key key-id md5 passwordSyntax Description:
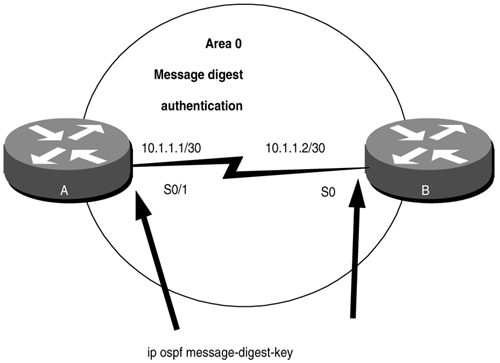
Purpose: If message digest authentication is enabled in Area 0 then all interfaces in the area need to be configured with the same authentication type. This command is used to configure message digest authentication on an OSPF interface. In Cisco IOS Software Release 12.0 and later, interface authentication can be configured independent of the authentication applied to an area (see Sections 19-1 to 19-4). Initial Cisco IOS Software Release: 11.0 Configuration Example 1: Message Digest Authentication on an OSPF InterfaceIn Figure 19-8, message authentication has been enabled for Area 0. The serial interfaces in Area 0 are configured with message digest authentication using a key ID of 1 and a password of cisco. Figure 19-8. Prior to Cisco IOS Software Release 12.0, if Message Digest Authentication Is Enabled in an OSPF Area, Then Message Digest Authentication Must Be Enabled on All Interfaces in the Area Router A interface Loopback0 ip address 1.1.1.1 255.255.255.255 ! interface Serial0/1 ip address 10.1.1.1 255.255.255.252 ip ospf message-digest-key 1 md5 cisco clockrate 64000 ! router ospf 1 area 0 authentication-message digest network 10.1.1.0 0.0.0.3 area 0 network 1.1.1.1 0.0.0.0 area 1 _________________________________________________________________ Router B interface Loopback0 ip address 2.2.2.2 255.255.255.255 ! interface Serial0 ip address 10.1.1.2 255.255.255.252 ip ospf message-digest-key 1 md5 cisco ! router ospf 1 area 0 authentication message-digest network 10.1.1.0 0.0.0.3 area 0 network 2.2.2.2 0.0.0.0 area 2 VerificationVerify that authentication has been enabled for Area 0. rtrA# show ip ospf Routing Process "ospf 1" with ID 1.1.1.1 and Domain ID 0.0.0.1 Supports only single TOS(TOS0) routes Supports opaque LSA It is an area border router SPF schedule delay 5 secs, Hold time between two SPFs 10 secs Minimum LSA interval 5 secs. Minimum LSA arrival 1 secs Number of external LSA 0. Checksum Sum 0x0 Number of opaque AS LSA 0. Checksum Sum 0x0 Number of DCbitless external and opaque AS LSA 0 Number of DoNotAge external and opaque AS LSA 0 Number of areas in this router is 2. 2 normal 0 stub 0 nssa External flood list length 0 Area BACKBONE(0) Number of interfaces in this area is 1 Area has message digest authentication SPF algorithm executed 41 times Area ranges are Number of LSA 8. Checksum Sum 0x404DC Number of opaque link LSA 0. Checksum Sum 0x0 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Flood list length 0 Area 1 Number of interfaces in this area is 1 Area has no authentication SPF algorithm executed 18 times Area ranges are Number of LSA 2. Checksum Sum 0x1A57A Number of opaque link LSA 0. Checksum Sum 0x0 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Flood list length 0 _________________________________________________________________ rtrB# show ip ospf Routing Process "ospf 1" with ID 2.2.2.2 Supports only single TOS(TOS0) routes It is an area border router Summary Link update interval is 00:30:00 and the update due in 00:21:19 SPF schedule delay 5 secs, Hold time between two SPFs 10 secs Number of DCbitless external LSA 0 Number of DoNotAge external LSA 0 Number of areas in this router is 2. 2 normal 0 stub 0 nssa Area BACKBONE(0) Number of interfaces in this area is 1 Area has message digest authentication SPF algorithm executed 4 times Area ranges are Link State Update Interval is 00:30:00 and due in 00:21:19 Link State Age Interval is 00:20:00 and due in 00:11:18 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Area 2 Number of interfaces in this area is 1 Area has no authentication SPF algorithm executed 2 times Area ranges are Link State Update Interval is 00:30:00 and due in 00:21:16 Link State Age Interval is 00:20:00 and due in 00:11:16 Number of DCbitless LSA 0 Number of indication LSA 0 Number of DoNotAge LSA 0 Verify that message digest authentication is enabled on the serial interfaces. rtrA# show ip ospf interface serial 0/1 Serial0/1 is up, line protocol is up Internet Address 10.1.1.1/30, Area 0 Process ID 1, Router ID 1.1.1.1, Network Type POINT_TO_POINT, Cost: 1562 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:02 Index 1/2, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 2 Last flood scan time is 0 msec, maximum is 4 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 2.2.2.2 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 1 _________________________________________________________________ rtrB# show ip ospf interface serial 0 Serial0 is up, line protocol is up Internet Address 10.1.1.2/30, Area 0 Process ID 1, Router ID 2.2.2.2, Network Type POINT_TO_POINT, Cost: 64 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:07 Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 1.1.1.1 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 1 Verify that Routers A and B have established an OSPF neighbor relationship. rtrA# show ip ospf neighbor Neighbor ID Pri State Dead Time Address Interface 2.2.2.2 1 FULL/ - 00:00:37 10.1.1.2 Serial0/1 Configuration Example 2: Changing Keys and PasswordsFor additional security, you may choose to periodically change your key and password. With clear-text authentication, when you change passwords there will be a loss of OSPF connectivity from the time you change the password on one end interface until you change the password on the other interfaces in the area. With MD5 authentication, you can configure a new key and password on an OSPF interface while leaving the old key and password in place. The old key and password will continue to be used until the new key and password are configured on the other interface. Modify the key and password on the serial interfaces on Routers A and B. First, add a new key and password to Router A in order to observe the behavior when the new key and password have only been configured on one end of the serial network. Router A interface Serial0/1 ip address 10.1.1.1 255.255.255.252 ip ospf message-digest-key 1 md5 cisco ip ospf message-digest-key 2 md5 budman clockrate 64000 Examine the effect of adding a new key and password on only one end of the serial link. rtrA# show ip ospf interface serial 0/1 Serial0/1 is up, line protocol is up Internet Address 10.1.1.1/30, Area 0 Process ID 1, Router ID 1.1.1.1, Network Type POINT_TO_POINT, Cost: 1562 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:04 Index 1/2, flood queue length 0 Next 0x0(0)/0x0(0) Last flood scan length is 1, maximum is 2 Last flood scan time is 0 msec, maximum is 4 msec Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 2.2.2.2 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 2 Rollover in progress, 1 neighbor(s) using the old key(s): key id 1 Notice that both keys are being used for authentication. Configure the new key and password on Router B while leaving the old key and password in place. Router B interface Serial0 ip address 10.1.1.2 255.255.255.252 ip ospf message-digest-key 1 md5 cisco ip ospf message-digest-key 2 md5 budman VerificationVerify that Router B is now using the new key and password. rtrB# show ip ospf interface serial 0 Serial0 is up, line protocol is up Internet Address 10.1.1.2/30, Area 0 Process ID 1, Router ID 2.2.2.2, Network Type POINT_TO_POINT, Cost: 64 Transmit Delay is 1 sec, State POINT_TO_POINT, Timer intervals configured, Hello 10, Dead 40, Wait 40, Retransmit 5 Hello due in 00:00:00 Neighbor Count is 1, Adjacent neighbor count is 1 Adjacent with neighbor 1.1.1.1 Suppress hello for 0 neighbor(s) Message digest authentication enabled Youngest key id is 2 You can now remove the old key and password from Routers A and B. Router A interface Serial0/1 no ip ospf message-digest-key 1 md5 cisco _________________________________________________________________ Router B interface Serial0 no ip ospf message-digest-key 1 md5 cisco Troubleshooting
|
| < Free Open Study > |
EAN: 2147483647
Pages: 236
- ERP Systems Impact on Organizations
- Challenging the Unpredictable: Changeable Order Management Systems
- Distributed Data Warehouse for Geo-spatial Services
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare