8-7 neighbor ip-address peer-group-name distribute-list ip-access-list-number-or-name prefix-list-nameout
| < Free Open Study > |
8-7 neighbor { ip-address peer- group - name } distribute-list { ip-access-list-number-or-name prefix-list-name }outSyntax Description:
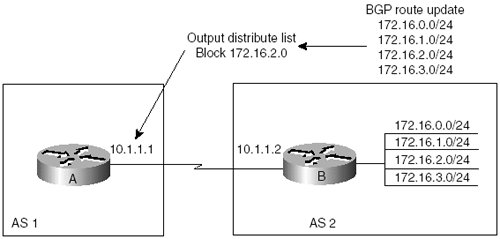
Purpose: To filter outgoing route updates to a particular BGP neighbor. Only one distribute list can be used per neighbor. The operation of the output distribute list is identical for both IBGP and EBGP neighbors. Cisco IOS Software Release: 10.0. Peer group support was added in Release 11.0, support for named access lists was added in Release 11.2, and prefix list support was added in Release 12.0. Configuration Example 1: Block a Particular RouteIn Figure 8-9, Router B is advertising four network prefixes to Router A. Router B filters the route update to Router A in order to reject the 172.16.2.0 network. Loopbacks are used on Router B to simulate the advertised networks, as shown in the following configuration. Figure 8-9. Scenario for the Use of the neighbor distribute-list out Command Router A ! interface Serial0 ip address 10.1.1.1 255.255.255.252 ! router bgp 1 neighbor 10.1.1.2 remote-as 2 ___________________________________________________________________________ Router B ip subnet-zero ! interface Loopback0 ip address 172.16.0.1 255.255.255.0 ! interface Loopback1 ip address 172.16.1.1 255.255.255.0 ! interface Loopback2 ip address 172.16.2.1 255.255.255.0 ! interface Loopback3 ip address 172.16.3.1 255.255.255.0 ! interface Serial0 ip address 10.1.1.2 255.255.255.252 clockrate 64000 ! router bgp 2 network 172.16.0.0 mask 255.255.255.0 network 172.16.1.0 mask 255.255.255.0 network 172.16.2.0 mask 255.255.255.0 network 172.16.3.0 mask 255.255.255.0 neighbor 10.1.1.1 remote-as 1 Before proceeding to the distribute list example, verify that Router A is receiving the routes from Router B: rtrA# show ip bgp BGP table version is 5, local router ID is 172.17.1.1 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.0.0/24 10.1.1.2 0 0 2 i *> 172.16.1.0/24 10.1.1.2 0 0 2 i *> 172.16.2.0/24 10.1.1.2 0 0 2 i *> 172.16.3.0/24 10.1.1.2 0 0 2 i Modify the BGP configuration on Router B to filter the 172.16.2.0 prefix that is being sent on Router A: Router B router bgp 2 neighbor 10.1.1.1 remote-as 2 neighbor 10.1.1.1 distribute-list 1 out access-list 1 deny 172.16.2.0 0.0.0.255 access-list 1 permit any The distribute list always references an IP access list. For this example, the access list number is 1. The first statement in access list 1 rejects the 172.16.2.0/24 network. The second line in the access list is necessary because there is an implicit deny any at the end of every IP access list. Without the permit any statement, all routes to Router A would be rejected. VerificationVerify that Router B is using the access list: rtrB# show ip bgp n BGP neighbor is 10.1.1.1, remote AS 1, external link Index 1, Offset 0, Mask 0x2 BGP version 4, remote router ID 172.17.1.1 BGP state = Established, table version = 6, up for 00:00:25 Last read 00:00:25, hold time is 180, keepalive interval is 60 seconds Minimum time between advertisement runs is 30 seconds Received 47 messages, 3 notifications, 0 in queue Sent 63 messages, 0 notifications, 0 in queue Prefix advertised 32, suppressed 0, withdrawn 1 Outgoing update network filter list is 1 Connections established 7; dropped 6 Last reset 00:00:50, due to User reset 0 accepted prefixes consume 0 bytes 0 history paths consume 0 bytes Connection state is ESTAB, I/O status: 1, unread input bytes: 0 Local host: 10.1.1.2, Local port: 11054 Foreign host: 10.1.1.1, Foreign port: 179 Check the BGP routing table on Router A to ensure that the 172.16.2.0/24 network has been filtered: rtrA# show ip bgp BGP table version is 4, local router ID is 172.17.1.1 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.0.0/24 10.1.1.2 0 0 2 i *> 172.16.1.0/24 10.1.1.2 0 0 2 i *> 172.16.3.0/24 10.1.1.2 0 0 2 i Configuration Example 2: Allow a Particular Route and Block All OthersFor this example, we will allow network 172.16.2.0/24 and block all other route advertisements to Router A. The access list required on Router B is access-list 1 permit 172.16.2.0 0.0.0.255 The BGP router configuration on Router B remains unchanged. Because there is an implicit deny any at the end of every access list, we will let this implicit statement block the remaining routes. VerificationAs in the previous example, check the BGP table on Router A to verify that only network 172.16.2.0/24 is in the BGP table: rtrA# show ip bgp BGP table version is 2, local router ID is 172.17.1.1 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.2.0/24 10.1.1.2 0 0 2 I Configuration Example 3: Allow an Aggregate Route and Block the More-Specific RoutesAssume that Router B is advertising an aggregate advertisement for 172.16.0.0/22 and the four more-specific routes 172.16.0.0/24, 172.16.1.0/24, 172.16.2.0/24, and 172.16.3.0/24. The BGP configuration for Router B would become router bgp 2 network 172.16.0.0 mask 255.255.255.0 network 172.16.1.0 mask 255.255.255.0 network 172.16.2.0 mask 255.255.255.0 network 172.16.3.0 mask 255.255.255.0 aggregate-address 172.16.0.0 255.255.252.0 neighbor 10.1.1.1 remote-as 1 The BGP table on Router A would contain rtrA# show ip bgp BGP table version is 5, local router ID is 172.17.1.1 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.0.0/24 10.1.1.2 0 0 2 i *> 172.16.1.0/24 10.1.1.2 0 0 2 i *> 172.16.2.0/24 10.1.1.2 0 0 2 i *> 172.16.3.0/24 10.1.1.2 0 0 2 i *> 172.16.0.0/22 10.1.1.2 0 0 2 i If we want to allow only the aggregate route and block the more-specific routes, a standard IP access won't work. To allow the aggregate using a standard IP access list while blocking the more-specific routes, we could try the following access list: access-list 1 deny 172.16.0.0 0.0.0.255 access-list 1 deny 172.16.1.0 0.0.0.255 access-list 1 deny 172.16.2.0 0.0.0.255 access-list 1 deny 172.16.3.0 0.0.0.255 access-list 1 permit 172.16.0.0 0.0.255.255 Unfortunately, the first statement also blocks the aggregate route. If we rearrange the statements, we could try this: access-list 1 permit 172.16.0.0 0.0.255.255. access-list 1 deny 172.16.0.0 0.0.0.255 access-list 1 deny 172.16.1.0 0.0.0.255 access-list 1 deny 172.16.2.0 0.0.0.255 access-list 1 deny 172.16.3.0 0.0.0.255 Now the first statement allows all the routes. The only way to permit the aggregate and reject the specific routes is to use an extended IP access list. Normally, the second address/mask pair in an extended IP access list signifies the destination address and mask. For a distribute list, the second address/mask pair indicates the mask size . Therefore, we can use this: Router B router bgp 2 neighbor 10.1.1.1 distribute-list 100 out access-list 100 permit 172.16.0.0 0.0.3.255 255.255.252.0 0.0.0.0 VerificationBy examining the BGP table on Router A, we can verify that the extended access list has permitted only the aggregate address. rtrA# show ip bgp BGP table version is 2, local router ID is 172.17.1.1 Status codes: s suppressed, d damped, h history, * valid, > best, i - internal Origin codes: i - IGP, e - EGP, ? - incomplete Network Next Hop Metric LocPrf Weight Path *> 172.16.0.0/22 10.1.1.2 0 2 i Troubleshooting
|
| < Free Open Study > |
EAN: 2147483647
Pages: 300