11.4 Managing Storage: A Plan of Attack
| Storage professionals need to harness and shape their IT departments with a coordinated plan of attack. The Data Mobility Group , led by John Webster and Perry Harris, has created just such a plan. This section presents their research. The race to recapture time and storage resources, such as unused capacity, led to the creation of dozens of storage management products. Primarily software-driven, these products range from point solutions for specific tasks such as volume allocation to broader management oversight of large enterprise storage deployments. For a storage professional looking to deploy a storage management solution, the product landscape can be overwhelming. Organizationally, the scope of functions that fall under the storage management domain can span several individuals. The first steps to achieving management simplicity require a framework to address broader issues of managing storage domain. What should a storage management group within the larger enterprise IT department look like? What skill sets should be represented within this group? How should the group be structured? What disciplines should be practiced? These are just a few of the questions that need to be answered . While it would be a gross oversimplification to say that storage was once a simple matter of plugging an array into a SCSI port, compared to the array of alternatives available today, the past was clearly a lot simpler. The days of one-size-fits-all SCSI are long gone. Storage as an enterprise core competency is becoming exceedingly complex as this brief, but by no means exhaustive, list of technologies involved with the new world of networked storage illustrates:
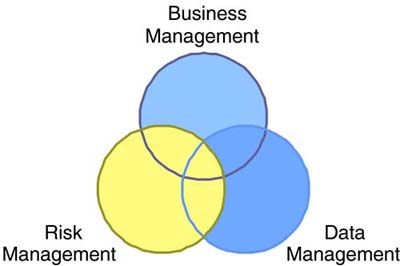
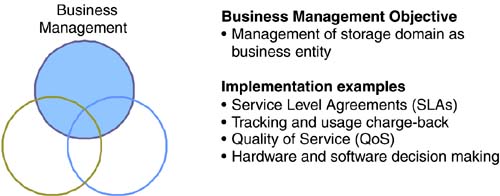
Given this complexity, it is becoming increasingly common to find storage management groups within enterprise IT departments. Once a decision is made to form such a group, the next challenge is how to break management into manageable pieces and determine which disciplines each group member should represent. 11.4.1 Practice DisciplinesThink of enterprise storage management as a practice composed of a number of definable discipline areas. Each area can be further broken down into specific disciplines or tasks. Both management tasks and software-based management applications can be grouped under each discipline area. For the purposes of this outline, we consider three discipline areas: managing the storage environment as a business entity, managing data from the standpoint of the storage environment, and using the storage environment to manage and mitigate corporate risk. There are no hard boundaries between discipline areas. In fact, management practices and products that fall under one area could also overlap with the other two. For example, copy functions that have been placed under the data management heading are also a critical component of business continuance (under risk management) and are becoming critical enablers of content distribution services (under business management). The discipline areas and overlap are shown in Figure 11-5. Figure 11-5. Practice disciplines for managing the storage domain. (Source: The Data Mobility Group) Dividing storage management first into discipline areas provides a method for identifying and assigning specific disciplines to each group member. Depending on the specifics of the organization, it may also be useful to add or further subdivide practice areas. 11.4.2 Business ManagementThe business management discipline area includes management of the storage domain as a business entity, complete with customer service levels (both internal and external) and a method for tracking usage and applying charge-back. The basic functions of this grouping are outlined in Figure 11-6. Figure 11-6. Business management practice objectives and implementation examples. A quick look back in storage history to storage service providers (SSPs) helps clarify this discipline. In spite of their hyperbolic track records, SSPs were successful in understanding at least one key component of storage ”that storage provisioning is a business. By implementing sophisticated systems to administer and track usage across multiple customers, the SSP model evolved into a storage utility, analogous to an electric or other utility-based service. Today, many IT managers are looking to reproduce such storage utility models within their own enterprises . In the case of an enterprise-based storage utility, customers are users represented by departments or applications and can be managed the same way that SSPs managed their outsourcing customers ”via service level agreements (SLAs). Many of the provisions covered in SLAs fall under this discipline area, including on-demand capacity provisioning, quality of service (QoS), continuous availability, and performance monitoring and management. Since the storage utility is run as a business, amortizing the cost across the entire user base provides a lower cost to each user than does operating independent environments. A comprehensive overview of storage service provider models was covered in Chapter 7, "Options for Operational Agility." The business management practice also includes hardware and software selection. Balancing the double-edged sword of choice, this group must decide between fewer vendors favoring a simplified support model with less price flexibility and a multivendor solution favoring a potentially more complex support model but with greater price flexibility. Since the business management practice understands the ultimate needs of the customers (departments, specific applications, service levels), this group should lead product selection. However, for practical implementation reasons, all discipline areas should be involved in choosing new products. 11.4.3 Risk ManagementRisk management includes the use of the storage domain to mitigate corporate risk through the use of well-established backup and recovery procedures, business continuance, disaster recovery, and most recently, security functions. The storage domain is also a good place to focus attention when implementing compliance with regulatory requirements. Examples in the United States include the Securities and Exchange Commission (SEC) for public companies and the Health Insurance Privacy and Accountability Act (HIPAA) for health-care organizations. A tightly integrated combination of storage hardware, software, and networking services can be used to secure and protect data from unforeseen catastrophic events, human error, or malicious intent. Consequently, storage platforms can now be thought of as places to manage and mitigate enterprise risk. With the increasing dependence on corporate data, concentrating risk management into a discipline area ensures proper oversight and organizational management of this function. The primary areas of risk management are outlined in Figure 11-7. Figure 11-7. Risk management practice objectives and implementation examples. (Source: The Data Mobility Group) Four major IT disciplines relating to risk management can be applied to the storage environment:
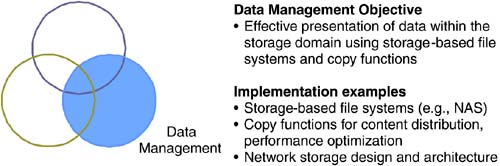
11.4.4 Data ManagementThe data management practice includes the effective presentation of data contained within the storage domain through storage-based file systems and copy functions. It also includes effective storage infrastructure design for maximum performance. The primary objective and implementation examples are shown in Figure 11-8. Figure 11-8. Data management practice objectives and implementation examples. (Source: The Data Mobility Group) This discipline area serves as a foundation for business management and risk management with basic functions acting as building blocks for other areas. Data management will become more important over time as more file management capabilities move into the storage domain. Storage-based file management systems can protect shared data ”accessed by multiple applications, servers, or users ”from loss or corruption while maintaining a high degree of data availability for all authorized applications or users. Copy functions fall into the data management practice. These functions are essential to the storage domain's risk management capabilities for functions such as backup and replication. Copy functions also enable new Web- facing applications by presenting data in multiple forms for specific use. Additionally, copy functions can enhance performance by distributing content to multiple locations, simplifying access across geographic areas. A subset of policy-based automation also falls under the data management practice. As mentioned earlier in this chapter, few, if any, industries are immune to regulatory oversight, and many require long-term retention of digitized records. The automation of corporate policies covering records retention can be programmed such that user productivity is enhanced and storage management is greatly simplified. An example would be an email management application that sorts through an email user's in-box and offloads certain documents to a centralized records retention facility, relieving users of this burden and freeing up disk space on email servers. 11.4.5 Shaping Storage Domain ManagementThe storage management plan outlined through the business, risk, and data management practices can be implemented within an existing enterprise IT department with minimal disruption. This plan can also be used to structure the operational and organizational management of a new team formed to absorb the larger responsibilities of a growing IT storage domain. IT skills related to backup and recovery, performance, security, and networking have existed for years in the data center. Implementing this organizational plan gives these traditional skills a networked storage focus. It further leaves room to incorporate additional skills to align an enterprise storage management group with present and future business needs. Implementation of the plan mandates attention to specific management policies for the storage domain. The following section presents a sampling of such policies. It is by no means an all-inclusive list, but rather intended to assist in the creation of company- and department-specific storage domain management. |
EAN: 2147483647
Pages: 108