5.4 Measuring Returns
| Measuring returns on technology investments can be a tricky business. The breadth and depth of large-scale computing projects leaves even the most intricate analysis open for debate. In the preceding sections, we covered both the defensive and offensive approaches to derive value from storage networking investments. Keeping both of these approaches in mind helps to better evaluate and measure the actual returns for individual companies. This section covers some general guidelines for savings through networked storage, then outlines a couple of useful frameworks to keep both the defensive and offensive approaches at hand for further analysis. 5.4.1 Cost Savings with Storage Area NetworksCalculating returns for technology investments comes down to savings of both operational and capital costs along with incremental revenue from new opportunities. These added-value categories span both defensive and offensive strategies for networked storage. Common customer savings exist through the following:
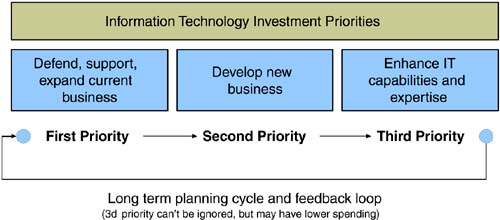
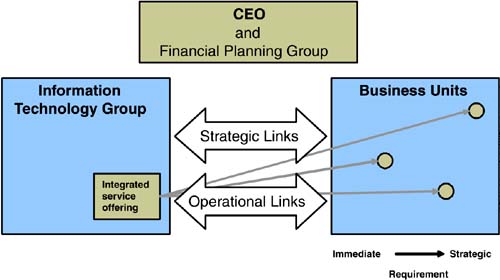
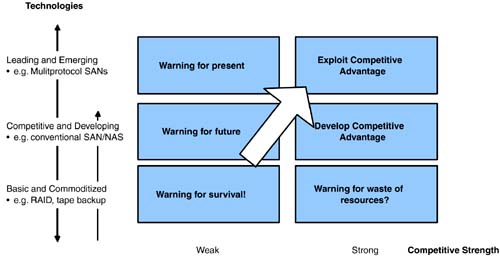
Use of IP networking technology also adds considerable offensive-focused strategies for operational agility such as the ability to use familiar and ubiquitous IP networks for storage. This prevalent and mature platform has lower intangible costs than traditional Fibre Channel networks, particularly in the areas of management, training, and time to deployment. The IP networking platform delivers enhanced functionality with unrestricted topologies, cross-vendor platforms, and advanced routing, management, and security. Scalability adds to cost savings through the ability to build SANs with large numbers of nodes, high-speed links, and long-distance connections. Most importantly, the investment in an IP fabric is well protected through the options of handling Fibre Channel, iSCSI, or multifunction traffic, including NAS. 5.4.2 Defining Information Technology GoalsThe largest returns from IT investments come through correlating cost with business unit priorities. IT managers must keep these priorities in mind when calculating the return on the technology investment (Figure 5-15). The first priority is to defend, support, and expand current business. If the underlying technology isn't supporting existing revenue streams, approximate calculations can determine the amount of lost revenue and justify technology investments. Figure 5-15. Setting information technology business priorities. The second priority, developing new business, can be more difficult to justify, yet it is exactly this skill that can set one company apart from the next . Taking calculated risks on technology investments propels new business that can in turn develop ongoing revenue streams. Finally, the third priority enhances IT capabilities and expertise. These investments should be made when the economic climate affords the opportunity. Long- term planning helps determine the timing for such investments, as it can take up to a year or more to develop a core set of inhouse skills that will then drive first and second priority investments. 5.4.3 Tying Technology Capabilities with Business ProcessesFar too often, technical capabilities are developed independent of business process and planning. Because of the ongoing strain on IT organizations, incremental technology investments typically focus on meeting immediate targets for current business functions. This logical step solves short-term needs, but lack of integral communication between the IT department and the business units dooms this relationship to a never-ending catch-up cycle. Technology and business integration starts from the CEO down. By creating operational and strategic links, IT teams accomplish goals of meeting current requirements and designing service offerings that span existing and future needs. Figure 5-16 outlines a basic framework for new technology offerings across business units. By accomplishing both immediate requirements and longer term strategic needs, the total cost of the technology investment can be amortized across a larger number of business units, generating sizable returns from integrating technical and business functions. Figure 5-16. Creating strategic and operational links between IT groups and business units. 5.4.4 Storage Networking as Competitive AdvantageThe intersection of storage and networking represents massive market forces. The data networking market and storage markets each measure in the hundreds of billions of dollars. The surrounding ecosystems add to the end-to-end solutions though applications, service, and diagnostics tools, training efforts, and certifications. This makes the market for networking equipment, for example, larger than that of the product shipments alone. Similar market size escalation also exists for storage subsystems. Regardless of technology merits, pros and cons, personal preferences, or ownership debates, the sheer size of integrating two multihundred billion-dollar markets opens windows of opportunity. Those opportunities come as investments for those tracking public company performance, market direction, and stock price; in terms of new product windows for startups and larger companies filling smaller integration gaps; in terms of cost savings for CFOs looking to negotiate among storage and networking providers; and in terms of competitive advantage windows for IT department to create sustainable advantages. Companies that operate with mission-critical applications residing on large storage repositories will, by default, need inhouse storage networking expertise. As covered in later chapters, that expertise might be a small team supervising outsourced contracts to an IBM Global Services or EDS-like supplier. Alternatively, that expertise might be a dozen or more talented storage professionals who can construct, operate , and maintain the infrastructure to support business needs. When large market forces collide, those with the greatest inhouse expertise must adopt a strategy to maximize competitive advantage. Today, with the storage and networking markets in the first stage of overlap, those strategies require immediate formulation and deployment. Figure 5-17 maps technologies to competitive strengths to help companies identify storage competence areas that can be exploited. On the vertical axis, technologies range from those that are basic and commoditized like RAIDs to leading and emerging technologies such as IP storage networks and mutliprotocol SANs. This simplified chart splits technologies into three categories, but a detailed analysis could include more segments. Competitive strength covers the horizontal axis, ranging from weak to strong, and the technology strategies to exploit competitive advantage fit accordingly . Figure 5-17. Storage technologies and opportunities for competitive advantage. Companies must place inhouse resources on projects most likely to develop into competitive advantage, while avoiding contributing too much time or effort to commoditized functions. The market windows opening for the storage networking market are wide and will reward those able to seize and exploit advantages of an optimized storage infrastructure. |
EAN: 2147483647
Pages: 108
- Using SQL Data Manipulation Language (DML) to Insert and Manipulate Data Within SQL Tables
- Using Data Control Language (DCL) to Setup Database Security
- Using Keys and Constraints to Maintain Database Integrity
- Performing Multiple-table Queries and Creating SQL Data Views
- Retrieving and Manipulating Data Through Cursors