1.5 Audience and Text Overview
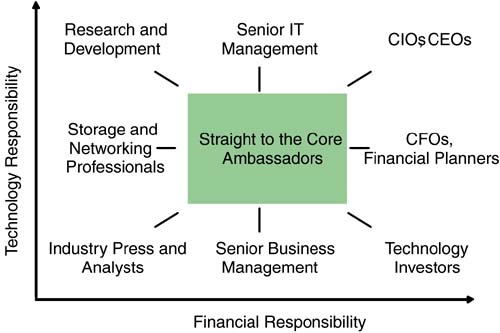
1.5.1 Target AudienceIP Storage Networking ”Straight to the Core was written to serve IT and business managers. As these two groups need to understand each other's objectives to develop coherent action plans, it makes sense to cover considerations for both sides. On the business side, the book covers strategies for storage network deployment, options for outsourcing, and insight into storage vendor control points. On the technical side, the book presents comprehensive infrastructure explanations along with new and emerging developments in storage networking, specifically the recent integration of storage with mainstream IP networking. This area, which brings networking and storage professionals together for a common cause, presents the greatest opportunities for organizations to deploy innovative and valuable infrastructure. Beyond senior IT and business management, the book addresses a wider range of constituents involved, directly or indirectly, with the deployment of enterprise storage. CIOs, CEOs, and CFOs will benefit from understanding the mix between technical and financial opportunities, particularly in the case of multimillion dollar deployments with disaster recovery plans that may require board approval. Research and development teams will benefit by seeing new architectural designs for application deployment. Technology investors, industry press, and analysts will benefit from a deeper understanding of the market forces behind the technology innovation. All of these groups have a stake in the enterprise storage industry, and as such, can be considered "straight to the core" ambassadors, as shown in Figure 1-3. Figure 1-3. Target audience for IP Storage Networking ”Straight to the Core. 1.5.2 Text OverviewChapters 2 and 3 cover the background of storage hardware and software respectively. Storage professionals will likely grasp these details easily. However, Chapter 2, "The Storage Architectural Landscape," pays special attention to the differences between network-attached storage, operating at the file layer, and storage area networks, operating at the block layer. As these two useful storage technologies merge to a common communications medium of IP networking, a review of each should prove helpful. Chapter 3, "The Software Spectrum," presents a detailed overview of the software spectrum around data storage management. Moving more quickly than other areas of the infrastructure, the software components can make a storage administrator's life easier and provide business value for the corporation. New market segments, specifically virtualization, are particularly interesting given the rapid development underway. While current virtualization software may not be appropriate for all organizations presently, these powerful capabilities will enhance storage administration, and any organization looking toward new investments must keep this component in the design plan. Chapter 4, "Storage System Control Points," and Chapter 5, "Reaping Value from Storage Networks," lay the foundation for building effective storage network roadmaps . Chapter 4 presents a history of data storage architectures and how the intelligence piece of the equation has evolved across server platforms, disk subsystems, and now within networking fabrics . This dynamic shift, if managed appropriately, can be used toward customer advantage in balancing multivendor configurations. Building these kinds of strategies into a storage networking roadmap can provide significant cost savings at future junctures. Similarly, Chapter 5 outlines the defensive strategies for data storage most often associated with disaster recovery and business continuity. IP Storage Networking ”Straight to the Core goes one step beyond the typical analysis by providing offensive strategies for storage deployment, fostering operational agility, and anticipating future changes to the overall architecture. Finally, the chapter concludes with techniques to measure returns on defensive and offensive tacks, allowing business and IT managers to justify expenditures and be recognized for cost efficiency and profit contribution. The primary business continuance applications are covered in Chapter 6, "Business Continuity for Mission-Critical Applications." Most organizations have some or all of these applications running at present. The chapter begins by outlining the business continuity objectives for each application, for example, designing "classes" of storage. It also breaks down the differences between server availability and storage availability, and the required interaction. Storage-specific requirements of these applications are reviewed, particularly, mechanisms to optimize performance while maintaining business continuity. Conclusions about enabling uptime allow business and IT managers to draft the appropriate business continuity plans to meet their objectives. Chapter 7, "Options for Operational Agility," examines means to increase efficiency and productivity, and create a flexible data storage infrastructure to serve the organization through dramatic and unpredictable information growth. By applying business models of ownership, financing, inventory management, and forecasting, business and IT mangers can create solid roadmaps for an agile enterprise. Specific topics covered include the emergence of outsourced storage models, recommendations for managing service level agreements, accelerating application deployment, and incorporating data storage into proven models for corporate asset management. The tactical roadmap begins in Chapter 8, "Initiating Deployment," and extends through Chapters 9 and 10. From an exploration of the infrastructure design shifts to crafting an effective migration, Chapter 8 assists in this decision making. It also includes guidelines for calculating the total cost of ownership and identifying the true cost components of an enterprise data storage deployment. Chapter 9, "Assessing Network Connectivity," serves as a comprehensive review of networking options. In cases of both business continuity and operational agility, the networking component plays a critical role. The ability to network storage devices within and across organizations presents opportunities for innovating architectures. Recently, with the introduction of new IP storage technologies such as iSCSI, choosing the right networking option is more important than ever. Topics such as network technologies, topologies, and carriers are covered thoroughly in this chapter, including security for storage across networks. Rounding out the tactical storage roadmap, Chapter 10, "Long-Distance Storage Networking Applications," reviews specific applications across wide area networks. Historically, storage applications have been designed for the data center, with little consideration for the associated latency of running these applications across long distance. Today, sophisticated techniques exist that mitigate the effects of distance and enable storage applications to run between virtually any locations. These techniques are outlined in the chapter. With the appropriate storage infrastructure in place, business and IT managers still have the task of maintaining and managing storage policies. Chapter 11, "Managing the Storage Domain," presents options for creating overall enterprise storage policies with a focus on data protection and disaster recovery scenarios. As these functions are inextricably linked with the need to administer overall growth, aspects of managing storage expansion are included in this section. |
EAN: 2147483647
Pages: 108