3.1 PASSIVE ATTACKS
3.1 PASSIVE ATTACKS
As mentioned earlier, a passive attack "attempts to learn or make use of information from the system but does not affect system resources" [1]. As such, it primarily threatens the confidentiality of data being transmitted. The situation is illustrated in Figure 3.1. The data transmitted from the originator (on the right side) to the recipient (on the left side) may be observed by the intruder (in the middle).[1] This data may include anything, including, for example, confidential e-mail messages or usernames and passwords transmitted in the clear. In fact, the cleartext transmission of authentication information, such as usernames and passwords, is the single most important vulnerability in computer networks and distributed systems today.
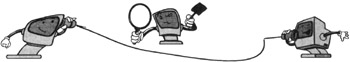
Figure 3.1: A passive attack threatens the confidentiality of data being transmitted.
In regard to the intruder's opportunities to interpret and extract the information that the transmitted data encodes, passive wiretapping and traffic analysis attacks are usually distinguished:
-
In a passive wiretapping attack, the intruder is able to interpret and extract the information that the transmitted data encodes. For example, if two parties communicate unencrypted, a passive wiretapper is trivially able to extract all information that is encoded in the data.
-
In a traffic analysis attack, the intruder is not able to interpret and extract the information that the transmitted data encodes. Instead, traffic analysis refers to the inference of information from the observation of external traffic characteristics. For example, if an attacker observes that two companies—one financially strong, the other financially weak—begin to trade a large number of messages, he or she may infer that they are discussing a merger. Other examples occur in military environments.
The feasibility of a passive attack primarily depends on the physical transmission medium in use and its physical accessibility for an intruder. For example, mobile communications is by its very nature easy to tap, whereas metallic transmission media at least require some sort of physical access. Lightwave conductors also can be tapped, but this is quite expensive. Also note that the use of concentrating and multiplexing techniques, in general, makes it more difficult to passively attack data in transmission.
It is important to note that a passive attacker does not necessarily have to tap a physical communications line. Most network interfaces can operate in a so-called "promiscuous mode." In this mode, they are able to capture all frames transmitted on the local area network segment they are connected to, rather than just the frames addressed to the machine of which they are part. This capability has useful purposes for network analysis, testing, and debugging (e.g., by utilities such as etherfind and tcpdump in the case of the UNIX or Linux operating system). Unfortunately, this capability also can be used by attackers to snoop on all traffic on a particular network segment. Several software packages are available for monitoring network traffic, primarily for the purpose of network management (e.g., Sniffer Pro[2] from Network Associates, Inc.). These software packages are dual-use, meaning they can, for example, be effective in eavesdropping and capturing e-mail messages or usernames and passwords as they are transmitted over shared media and communications lines.
Given the availability and ease of use of contemporary sniffer tools, one may wonder whether there are technologies to protect against passive attacks. Fortunately, the use of switching technologies makes it more difficult for an attacker to passively attack and eavesdrop on a network segment, because network traffic is directed only to the intended network interfaces. Furthermore, a new family of tools is being developed and deployed. These tools try to reveal the mere existence of systems with network interfaces that operate in promiscuous mode. For example, AntiSniff is a tool developed by L0pht Heavy Industries, Inc., and commercially distributed by Security Software Technologies, Inc. The tool "allows tests to be run that determine, through a variety of fashions, whether a remote system is capturing and analyzing packets that are not destined to its hardware address." For example, the tool may generate an Ethernet frame with a randomly chosen MAC address and a correct IP address for a remote system under consideration. The IP packet may encapsulate an ICMP request message. If the system responds with an ICMP message, one may argue that its network interface is operating in promiscuous mode. This is because the system has responded to a message it should not have been able to receive in the first place (because the MAC address is randomly chosen). Similarly, AntiSniff implements and is able to run a number of tests that are briefly explained in an unpublished technical paper.[3]
There are several technologies that can be used to protect against passive wiretapping attacks. For example, the use of data encryption is both effective and efficient. In fact, data encryption is still the technology of choice to protect against passive wiretapping attacks in today's computer networks and distributed systems. In Part III, we discuss many cryptographic security protocols that have been developed, implemented, and deployed to encrypt data as it is being transmitted in TCP/IP-based networks.
Contrary to passive wiretapping attacks and the use of data encryption, protection against traffic analysis attacks is much more complicated and requires more sophisticated security technologies. For example, the use of encryption techniques does not protect against traffic analysis. In fact, there are only a few technologies available today that can be used to protect against traffic analysis. Exemplary technologies include traffic padding and onion routing as proposed and developed by a group of researchers at the U.S. Naval Research Laboratory (NRL) [3–7].[4] Unfortunately, technologies to protect against traffic analysis generally do not meet the requirements and needs of packet-switched networks. In either case, these technologies are beyond the scope of this book. Keep in mind, however, that it is possible and very likely that privacy enhancing technologies (PETs) will become very important in the future, and that technologies to protect against traffic analysis also represent PETs.
[1]Note that many publications on network security use names, such as "Alice" and "Bob," to refer to the sending and receiving network entities, and other names, such as "Eve," to refer to a possible intruder. This is a convenient way of making things unambiguous with relatively few words, because the pronoun "she" can be used for Alice, and "he" can be used for Bob. However, the advantages and disadvantages of this naming scheme are controversial, and we are not going to use it in this book.
[2]http://www.sniffer.com
[3]http://www.securitysoftwaretech.com/antisniff/tech-paper.html
[4]http://www.onion-router.net
| Team-Fly |
EAN: 2147483647
Pages: 144