Backscatter and Tracebacks
| | ||
| | ||
| | ||
Backscatter and Tracebacks
In this section, we'll explore creative uses of decoy networks to detect attacks and spoofing and also to help track down the miscreant.
Backscatter
It seems fitting after all of this discussion on decoy networks and DDoS attacks to mention the notion of backscatter. For an entire semester during my freshman year in college, I wrote letters (yes, the physical kind) to various friends who were moving around a lot. Being the absent-minded individual that I am, I would consistently write the wrong return address on my envelopes. I'd forget to put my dorm suite number on them, or it would be completely illegible (I had discovered beer). Occasionally, one of my friends that I wrote would have moved and the letter I'd sent them bounced back to me with a post office notification stating "return to sender." Only, since my return address was written incorrectly, the bounce-back didn't go to me, it went to the resident office downstairs who called me and let me know (by matching my name ) I had again written my return address wrong and there was a letter waiting for me to pick up and resend. That "return to sender" bounce-back is a form of backscatter. Of course, the backscatter indicated to the resident office that I had been sending mail (and to whom).
On the Internet, when party A intends to perform a denial-of-service attack against party B, but party A wants to conceal his identity, he normally writes the wrong source address on his attack packets (the IP headers are forged to look like they came from parties A-Z, for example, only A-Z in IPv4 is 2^32 permutations ). During such attacks, routers and other network devices along the path inevitably send back a variety of messages that range from connection resets to quench requests to unreachable notifications. Since these messages are "returned to sender," and since the sender is forged, parties A-Z all receive them and thus gain knowledge of the attack on party B, just as the resident office gained knowledge of the mail I was sending. This is depicted in Figure 10-5.
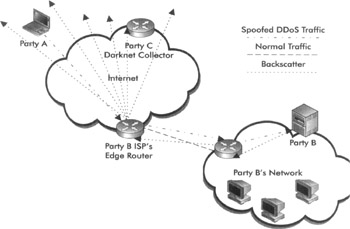
Figure 10-5: An example of backscatter during a DDoS attack
In today's packet filtering world, most of these backscatter messages are silently discarded by our firewalls because they are seen as responses to a message we did not send. But with an external darknet network implemented as explained earlier, we can look for these backscatter packets and determine when our address space is being implicated as one of the sources of an attack on another party. The following types of packets appearing in a darknet may be classified as backscatter and indicate your (darknet) address space is being implicated as one of the sources of an attack:
| ICMP Packets | Description |
|---|---|
| 3.0 | Network unreachable |
| 3.1 | Host unreachable |
| 3.3 | Port unreachable |
| 3.4 | Fragmentation required |
| 3.5 | Source route failed |
| 3.6 | Destination network unknown error |
| 3.7 | Destination host unknown error |
| 3.10 | Host administratively prohibited |
| 3.11 | Type of service network unreachable |
| 3.12 | Type of service host unreachable |
| 3.13 | Communication administratively prohibited |
| 11.0 | TTL expired during transit |
| 11.1 | Fragment reassembly timeout |
| TCP Packets | Description |
|---|---|
| RST bit set | TCP Reset |
Traceback
Now that we have a handle on backscatter, how can we use it? In a network with multiple Internet transit gateways, it may be useful during a debilitating attack to locate the ingress point of the "bad packets." This technique, known as a traceback, is useful in that once we identify the specific ingress point on our (or our ISP's) network, we may be able to drop the traffic there and reduce the load on our links, potentially even allowing "good" traffic to flow (through alternate gateways), unlike the simpler DDoS blackhole protection tactic discussed earlier. Traceback allows us to utilize the backscatter we collect in our darknet(s) as a means of finding the point where the attack is entering the network. Unfortunately, this is really only viable for ISPs or for far-reaching data networks with many Internet gateways. Some dependencies beyond that description include utilization of the blackhole defense mechanism at every Internet gateway. Since major ISPs do this along with a handful of global enterprise networks, it seems fitting to at least explain the process.
Assuming you have the network setup as described above, you can perform a traceback in the midst of a denial-of-service attack in three easy steps:
-
Identify the target and verify that the attack traffic is being spoofed (if it isn't, this traceback tactic will be fruitless).
-
Blackhole the route for the specific hosts (/32s likely) being attacked at each of your gateways. Exercise caution and follow the guidelines in Chapter 2 concerning the use of forwarding to the discard interface in lieu of using a packet filter to drop the attack packets. This blackhole operation will cause this gateway router to begin generating ICMP unreachable messages, which are (attempted to be) returned to the spoofed sources of the attack packets.
-
Inside your darknets, use your darknet tools you've put into place to look for the backscatter traffic (probably in the form of ICMP unreachables) with your gateway routers' IP address in it. Any IP addresses of your gateways you see as the source of these backscatter packets validate that those gateways are actually the ingress point(s) of the attack traffic. Voil, you've found where the attack is entering the network. Even if you don't have your sophisticated darknet tools set up, a simple access list applied to the router interface of your darknet can do the trick for you as depicted below:
access-list 105 permit icmp any any unreachables log access-list 105 permit ip any any
Then, if you enter terminal monitoring mode on this access list (or simply tail the log), you'll get a poor man's backscatter report that you can look inside for the IP addresses of your gateways.
Note The traceback tactic and the blackhole defense against DDoS attacks are useful in situations where the floods of malicious traffic have forged (spoofed) headers. This was the customary way of performing such attacks until recently. But with the proliferation of zombied machines and botnets (see Chapter 17), many attackers have stopped spoofing DDoS packets all togetherthere's no reason to forge headers if your army of attacking systems are everywhere. Likewise, spoofed DDoS attacks have declined significantly as a result of the widespread deployment of uRPF and ingress filtering.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120