Stand-alone Systems in the DMZ
| | ||
| | ||
| | ||
As we noted in the introduction, a traditional DMZ typically consists of stand-alone systems residing between a border router and a firewall, while a modern DMZ typically consists of stand-alone systems behind a firewall, yet not on the internal network. A more advanced DMZ design consists of hierarchical firewalls. For organizations utilizing these methods, we point out potential weaknesses and methods to mitigate risk of intrusion.
We see three basic designs in deployment of DMZ systems:
-
Traditional DMZ
-
Border router (screening router)
-
DMZ system(s)
-
Firewall (with internal network behind the firewall)
-
-
Modern DMZ
-
Border router (screening router)
-
Firewall
-
External interface
-
Internal interface
-
One or more "DMZ" interfaces on the firewall
-
-
-
Advanced Hierarchical Firewalls
-
Border router (screening router)
-
Perimeter firewall
-
DMZ inside perimeter firewall
-
DMZ systems reside here
-
-
Internal firewall
-
Traditional DMZ
Again, a traditional DMZ may be viewed as a "moat" separating the outside wall from the inside wall. While not as common today, we still see this type of DMZ deployed. We don't advocate this type of design but it can be made secure with proper use of security zones. A myopic view would see this as the DMZ security zone. We posit that the zone includes the border router (access control between the Internet and the DMZ) and the firewall (access control between the DMZ and the internal network). Figure 6-5 depicts a traditional DMZ.
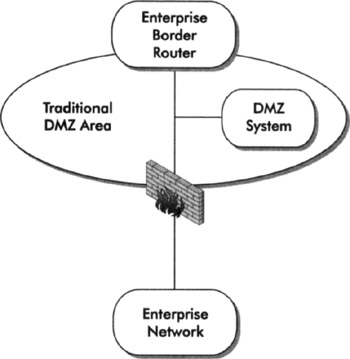
Figure 6-5: A traditional design for a DMZ
This design is simple and effective if secured properly. Building on what you learned in Chapter 4, you should define the security zone for systems in a traditional DMZ, which should include the border router, the firewall, and the DMZ system. The checklist in Table 6-2 may be used to develop defenses throughout the zone.
| Security Zone Component | Defensive Technique |
|---|---|
| Border router access control | Explicitly allow only those protocols/services necessary for Internet users to access the system; deny everything else |
| DMZ host operating system | Harden the host operating system, disable all unused/dangerous services, and ensure patches are current |
| System administration | Use a secure remote administration mechanism (encryption), or console-only access. Use strong authentication and authorization methods, and data integrity functions (TripWire, etc.) |
| Trust relationships between DMZ host and internal/external systems | Where possible, use VLANs to restrict traffic between DMZ hosts (if more than one), and/or use host-based firewall to establish trust relationships between other systems, perform egress filtering on both border router and firewall |
| Firewall access control | Ensure strict access control for trusted internal systems to access DMZ host, and for DMZ host to access trusted internal data stores (authentication data, application data) |
| Intrusion Detection/Prevention Systems (IDS/IPS) | Proper logging and IDS/IPS can alert you to possible attacks before they succeed |
| Flow statistics collection on the border router | Correlate flow data with IDS/IPS and system logging to provide rapid alert mechanism in case of attack/intrusion |
There are benefits in using a properly secured, traditional DMZ design, but this method doesn't scale well in large networks. Table 6-3 summarizes some of the risks and benefits of this approach.
| Risks | Benefits |
|---|---|
| Capital expense may be prohibitive if you have hundreds or thousands of systems to deploy. | If systems are completely isolated from the internal network, compromise is limited to that specific system (complete isolation is rare occurrence; there is typically some trust relationship with internal systems). |
| If proprietary/confidential data is stored locally on DMZ system, data theft/disclosure is more likely. | Stand-alone systems can be "lean and mean," optimized to serve a specific application. |
| Weak trust relationships/filtering with internal systems may give attackers the "keys to the kingdom" (this applies to all designs of DMZ networks). | Reduced resource utilization on the firewall since DMZ hosts are external. |
| A border router cannot typically provide in-depth , stateful inspection of packets destined for the DMZ host, and may leave it vulnerable to specific attacks. |
Modern DMZ
A more common DMZ design we see today is a DMZ LAN attached to a tertiary interface on a firewall. One or more interfaces may be used for DMZ systems, in addition to the untrusted/external and the trusted/internal interface. In this case, the security zone might include the border router, external network (between the border and firewall), the firewall, the DMZ LAN, and possibly the internal LAN. As you can see in Figure 6-6, this zone covers many security devices.
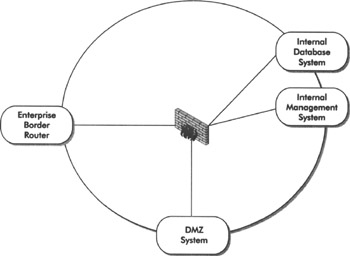
Figure 6-6: A modern DMZ design
This design is seen more frequently today, and many variations of this design exist. The checklist for developing defenses in Table 6-2 applies to this design also. However, this design provides more granular control and flexibility than the traditional DMZ. Table 6-4 summarizes some of the risks and benefits of this approach.
| Risks | Benefits |
|---|---|
| Higher resource utilization on the firewall, since it is now protecting the host. | Combination of border router and firewall filtering provides greater defense-in-depth. |
| If DMZ host is compromised, attacker may be "deeper" inside your infrastructure. | Stateful packet inspection and strict filtering on the firewall provides more granular protection for DMZ host. |
| Capital expense may be prohibitive if you have hundreds or thousands of systems to deploy. | More granular control between DMZ and internal network, if DMZ host accesses data stores there. |
Advanced DMZ Design Using Hierarchical Firewalls
A more advanced design for modern DMZs may consist of two or more firewalls layered within the network topology to provide maximum benefit of stateful packet filtering and access control between different security zones. An example of this design is depicted in Figure 6-7.
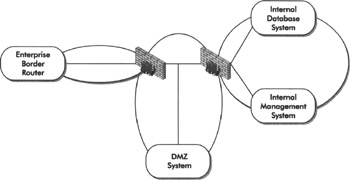
Figure 6-7: A DMZ design with hierarchical firewalls
For small networks, this design may be overkill, but in very large networks, this design can provide a high degree of flexibility, segregation of security zones, and trust between zones. The entire network in this example may be considered a security zone, but it makes more sense to segregate this network into at least three distinct zones; we'll call them the Perimeter, DMZ, and Internal zones. Given this segregation, you may wish to deploy systems in all three zones and establish specific trust relationships and packet filtering based on the function of these systems. The following table provides an example of systems you might deploy in each zone and the relationships between those systems.
| Security Zone | System Deployed | Trust Relationships |
|---|---|---|
| Perimeter | Mail relay | Corporate mail server and management console in Internal zone |
| Perimeter | Corporate Web Server (Internet information site) | Management console in Internal zone |
| DMZ | Extranet Web Server (customer web portal) | Backend database server and management console in Internal zone |
| Internal | Management Console | Systems in DMZ and Perimeter zones |
This is a complex design, with nuances too numerous to cover in this chapter, but the following table enumerates some of the risks and benefits of this design.
| Risks | Benefits |
|---|---|
| Policy management is more complex, and human error may lead to unintended attack or intrusion. | More granular filtering and policy enforcement between security zones. |
| Capital and operating expense may be prohibitive due to additional systems to manage and complexity of policy enforcement. | Strict policy enforcement between zones helps isolate intrusion to a specific zone. |
| Denial-of-service attacks are more difficult to sustain. |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120