Administration Tools
| < Day Day Up > |
| Windows Server 2003 Terminal Services provides administration tools that can help you manage remote sessions. Connecting to the ConsoleAny one of the following methods can be used to connect to the console:
Remote Desktops MMCAdministrators can host multiple Terminal Services connections with the Remote Desktops MMC snap-in. The snap-in can be used to manage servers that are running the Windows Server 2003 family or Windows 2000 Server. The Remote Desktops snap-in provides a navigable tree display that allows Administrators to view, control, and quickly switch between multiple sessions from a single window, as shown in Figure 15.4. As with the RDC tool, remote computers can be configured to run specific programs upon connecting, and to redirect local drives to appear in the remote session. Logon information and client screen area also can be configured from the snap-in. Remote console sessions to Windows servers can be initiated using the snap-in. Figure 15.4. Remote Desktops MMC.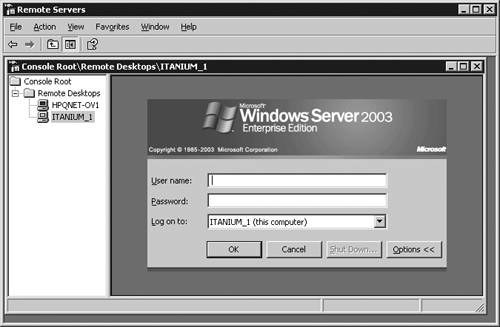 Terminal Services ManagerThe Terminal Services Manager, tsadmin.exe, is used to manage Terminal Services users, sessions, and processes on any server running Terminal Services on the network. This tool can be used to connect and disconnect, log off, reset, and remotely control sessions. Other functions provided by tsadmin include connecting to other servers in trusted domains, managing sessions on a remote server, sending messages to users or logging them off, and terminating processes. Terminal Services ConfigurationReset and disconnect timeouts and default encryption settings are configured using the Terminal Services Configuration tool, tscc.msc. To configure reset and disconnect timeouts for individual accounts, use the Sessions tab of the user 's Account Properties page. Note that these settings can be overridden by Terminal Services Group Policy or Windows Management Instrumentation (WMI). Event ViewerThe Event Viewer, eventvwr.msc, can be used to view events that might have occurred as pop-up dialog boxes on the server console. Command-Line UtilitiesThe following command-line utilities can be used to manage Terminal Servers:
Enhanced Management FeaturesThe features in the following sections enhance the manageability of Terminal Services in Windows Server 2003. Group PolicyGroup Policy can be used to configure Terminal Services properties of groups of servers simultaneously . Properties that can be modified by Group Policy include setting the Terminal Services profile path , automatic logon, home directories, and starting programs on connection. Windows Server 2003 includes a number of enhanced settings that affect Terminal Services. Security Policy EditorTerminal Server user rights for individual users or groups can be assigned using the Security Policy Editor. This can be used to give users the right to log on to a Terminal Server without having to be a member of the Remote Desktop Users group. Remote Desktop User GroupTerminal Services permissions can be granted to individual users or groups, or users can inherit permissions as a result of being a group member. To control permissions, add users to the built-in group Remote Desktop Users or add them to a list in the Terminal Services Connection Configuration (TSCC) program. For example, to allow everyone access to the Terminal Server, add the Everyone group to the Remote Desktop Users group. Note that you must still use TSCC for Network Interface Card (NIC) permissions on multi-NIC servers. To manage who can connect remotely to the server, Administrators can use either the Remote Desktop Users group or set permissions on the RDP-Tcp connection in TSCC. When setting permissions for individuals or groups, remember that denial of permission overrides an inherited permission. Windows Management Instrumentation (WMI)A full WMI provider allows for a scripted configuration; of Terminal Services settings. A number of WMI aliases are included to provide a simple front end for frequently used WMI tasks . Microsoft KB article 290720 ("How to Add a User to Terminal Services RDP Permissions by Using WMI ") describes how to use WMI to add users or groups to Terminal Services Remote Desktop Protocol permissions. Refer to the "Windows Management Instrumentation (WMI)" section in Chapter 10, "System Administration," of this book for more information on implementing WMI. Active Directory Service InterfacesAn Active Directory Service Interface (ADSI) provider gives programmatic access to per-user, Terminal Services profile settings such as home directory, remote control permissions, and others. ADSI extension is a special Common Object Model (COM) object that allows extension of a COM object and can be used to add functionality to a directory object and simplify administration tasks. Administrators can use ADSI extension for Terminal Services user configuration to write scripts that will automate maintenance of Terminal Services-specific user properties. It includes the dual interface called IADsTSUserEX, which can be used to examine and configure Terminal Services user properties such as logon, home directory, remote control, session, and environment properties of the ADsTSUserEx class. Printer RedirectionUsing Terminal Services, printing jobs can be routed to a printer attached to a computer or to a printer that the client can map on the network. Clients can access local printers through either automatic printer redirection via the RDC or with the manual method used for 16-bit clients , Windows-based terminals, or printers that require older drivers. Printer redirection can be disabled for a connection using the Terminal Services Configuration or Group Policies. Terminal Services ManagerLarge arrays of servers are easier to manage due to reduced automatic server enumeration. Lists of favorite servers can be built, which makes it easy for Administrators to manage a selected group of servers. Terminal Server License ManagerWith Terminal Server License Manager, it's easier to activate a Terminal Server license server and to assign licenses to it. Single Session PolicyAdministrators can limit users to a single session, regardless of whether it is active ”even across a farm of servers. Client Error MessagesMore than 40 new client error messages make it easier to diagnose client connection problems. For a list of errors, refer to Appendix D, "Terminal Server Client Error Messages and Troubleshooting." EncryptionRemote Desktop Protocol connections use 128-bit bidirectional RC4 encryption by default. Older clients can connect using lower encryption unless only high-encryption clients are permitted. FIPS Compliant is an additional encryption level added to Terminal Server in Windows Server 2003. This level of security encrypts data with the Federal Information Processing Standard (FIPS) encryption algorithms using Microsoft cryptographic modules. Software Restriction PoliciesLocking down Terminal Servers is simplified in Windows Server 2003 by using Group Policy software restriction policies. These policies limit specified programs to be run by certain users. note Use Group Policy software restriction policies to lock down Terminal Servers on Windows Server 2003. This built-in Windows feature replaces the Application Security (AppSec) tool used in previous versions of Terminal Services. See http://www.microsoft.com/windowsxp/pro/techinfo/administration/restrictionpolicies/default.asp for more information. Another lock-down method is using a common user environment through GPO user configuration. Further restriction can be imposed by using a GPO to allow only Windows applications. Session DirectoryTerminal server "farms" allow clusters of load-balanced servers to appear to their users as a single instance. With the new Session Directory feature, users can reconnect to the specific disconnected session they left within the farm instead of being directed to the least loaded server. This avoids the problem of being reconnected to a server other than the one from which the user was disconnected. This feature is beneficial when you have a policy limiting the user to one session at a time, which might be necessary because of licensing limitations or application compatibility. Member servers of the Terminal Server farm must be running the Enterprise or Datacenter Edition of Windows Server 2003. Session Directory can use the Windows Load Balancing Service or a third-party load balancer. tip Use the Terminal Services Session Directory logging feature for trouble-shooting as described in Microsoft KB article 327508, "How to Turn On the Terminal Services Session Directory Logging Service," at http://support.microsoft.com/default.aspx?scid=kb;en-us;327508. Group Policy Editor and Session DirectoryThe Session Directory configuration settings of multiple servers can be managed using the Group Policy Editor to set Group Policies. TSCC is a good way to manage individual servers, but for managing groups of machines, Group Policies are an efficient way to centrally configure Session Directory settings. note Manage individual users with TSCC and groups of users with Group Policy. Session Directory Group Policy SettingsThe Session Directory Group Policy settings can be found in Computer Configuration/ Administrative Templates/Terminal Services/Session Directory. The settings are
If the Session Directory server field is left blank or has an invalid server name or IP address, the Terminal Server generates an error in the event log indicating that the server cannot be found. The event log entries generated by Session Directory are
If AD is not being used, there will be no centralized Group Policy. However, Group Policy Editor can still be used to manage these settings by running GPEdit.msc locally on each machine. For detailed steps on setting up the Session Directory Service, refer to Microsoft KB article 301923, "How to Configure Terminal Services Session Directory Service." Unattended InstallationIn Windows Server 2003, the entries that you make in answer files for Terminal Server unattended installations have been changed. For example, this setting determines whether Application Server is installed (the default is OFF ): [Components] TerminalServer=ONOFF This setting selects whether Terminal Services connections are allowed (for Windows Server 2003 the default setting is and for Windows XP the default is 1 ): [TerminalServices] AllowConnections=10 note Refer to Microsoft KB article 278513, "Changes to the Terminal Services Installation in Windows Server 2003," for new unattended installation settings for Windows Server 2003. |
| < Day Day Up > |
EAN: N/A
Pages: 214