RDP Architecture and Deployment Planning
| < Day Day Up > |
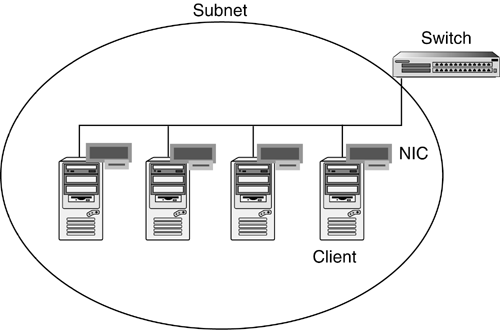
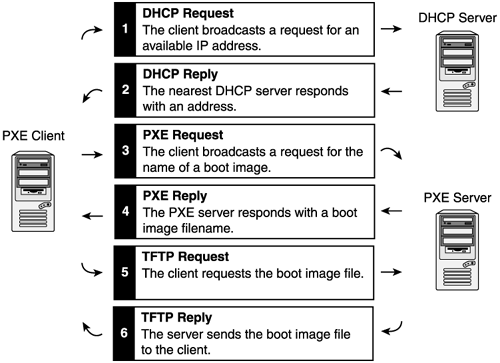
| This section assumes that you have a basic understanding of networking terminology including terms such as NIC, subnet, switch, client, and server. These basic networking components are illustrated in Figure 9.1. Figure 9.1. Basic network structure. Network Services ComponentsThe RDP is designed to perform optimally with Dynamic Host Configuration Protocol (DHCP) and Pre-Boot Execution Environment (PXE) incorporated within the network infrastructure. This section provides a basic overview of DHCP and PXE. DHCP and PXE are not required to use the RDP. Other alternatives, such as boot floppy disks, are available, but are not discussed in this chapter. To realize the full benefit of automation features incorporated into RDP, HP recommends the use of DHCP and PXE. ClientA client is any computer that has a Network Interface Card (NIC) and is connected to a network. A PXE client is any computer with a NIC that contains PXE support in its firmware. Newer ProLiant servers have PXE support in their NICs, whereas older servers support PXE through the addition of a standup NIC. For complete details on PXE support in ProLiant servers, refer to the HP ProLiant Essentials Rapid Deployment Pack ”Windows Edition Support Matrix or HP ProLiant Essentials Rapid Deployment Pack ”Linux Edition Support Matrix at http://www.hp.com/servers/rdp . DHCPDHCP is a network service that allows clients to obtain an IP address from a pool of addresses (scope). note If you are concerned about using dynamic addresses for servers, it is possible to use DHCP during the initial deployment phase and then assign a static address during the OS installation phase. PXEPXE is a network service that enables PXE clients to download and execute a boot image. This is analogous to booting from a floppy disk. The boot image, or network bootstrap program (NBP), uses the Universal Network Device Interface (UNDI) provided by the PXE client firmware to access the network. UNDI enables one boot image to work with different PXE-capable NICs, because the specifics for each NIC are handled by the PXE client firmware. note A NIC-specific driver can be used instead of the UNDI driver. However, doing so causes the boot image to work only on clients with NICs supported by that driver. The PXE client downloads the boot image using the Trivial File Transfer Protocol (TFTP) or on some PXE servers using Multicast TFTP (MTFTP). MTFTP allows a PXE server to simultaneously send a boot image to multiple clients PXE Boot ProcessWhen a client performs a PXE boot, it starts a sequence of transactions ( requests and responses) between itself and the DHCP and PXE services. Two sequences are possible, based on the physical locations of the DHCP service and the PXE service:
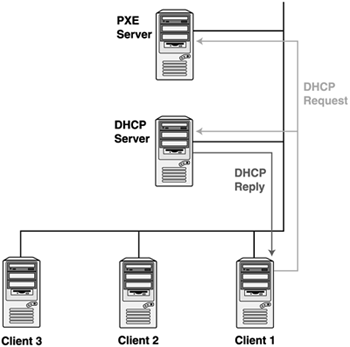
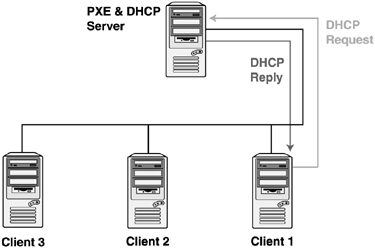
Sequence 1Figure 9.2 conceptually illustrates the transactions between the PXE client and the DHCP and PXE services during the PXE boot process, when the DHCP and PXE services are provided by different servers. Figure 9.2. DHCP and PXE boot sequence 1. Sequence 2Figure 9.3 conceptually illustrates the transactions between the PXE client and the DHCP and PXE services during the PXE boot process when the DHCP and PXE services are provided by a single server. In BINL proxy mode, the DHCP server uses an extra field (Option 60) in the DHCP offer response to tell the client that the PXE service is located on the same server. Figure 9.3. DHCP and PXE boot sequence 2.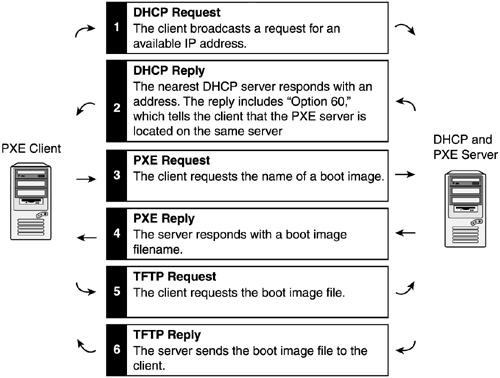 DHCP and PXE InfrastructureDHCP and PXE can be implemented in an enterprise environment as one of three basic scenarios. These scenarios are based on the physical locations of the DHCP service, the PXE service, and the PXE clients as follows :
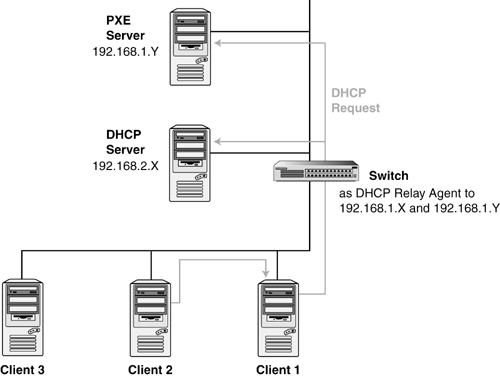
note The terms "service" and "server" are used interchangeably depending on whether DHCP and PXE are located on the same server or on different servers, respectively. Scenario 1The first scenario (shown in Figure 9.4) consists of a simple network in which the DHCP service and PXE service are provided by different servers and are on the same subnet as the PXE clients: Figure 9.4. Scenario 1 DHCP and PXE on the same subnet. Scenario 2The second scenario (shown in Figure 9.5) consists of a simple environment in which the DHCP service and PXE service are provided by a single server and are on the same subnet as the PXE clients. This scenario is typical of labs, isolated networks, or loading areas. Figure 9.5. Scenario 2 DHCP and PXE on the same server and subnet. Scenario 3The third scenario consists of an enterprise environment in which the DHCP and PXE services are provided on a different subnet than the PXE clients. When a PXE client attempts a network boot, it broadcasts a message to search for a DHCP service. However, switches are intended to constrain broadcast traffic to certain subnets so, by default, they do not forward these DHCP messages. To forward DHCP requests and responses between the PXE client and a DHCP service on another subnet, a DHCP relay agent must be used. A computer (proxy DHCP server), or a switch (configured to forward requests and responses) can act as a DHCP relay agent. The installation of DHCP relay agents allows the use of one centralized DHCP service for a large network. note For Cisco switches, DHCP relay is accomplished by using the IP-helper address command. note The switches must be configured to activate the ports for the PXE clients as soon as a link is detected. Certain negotiation protocols, such as Spanning Tree Protocol (STP), EtherChannel Protocol, and Port Aggregation Protocol (PAgP), delay the activation of switch ports after a link is detected . This delay can be longer than the standard PXE client timeout; in which case, the PXE boot fails. For Cisco switches, the PortFast option must be enabled to cause the port to be activated immediately. For some Cisco 28xx series switches, the PortHost option must also be set. If using EtherChannel or PAgP, set the port to manual mode to avoid longer delays associated with auto mode. Figure 9.6 illustrates how a Proxy DHCP server can be used to forward requests and responses between the PXE clients and the DHCP and PXE services. A Proxy DHCP server is required in each subnet. If the DHCP and PXE services are running on different servers, then the Proxy DHCP server must be configured to forward all requests to both servers. Figure 9.6. Scenario 3 Proxy and DHCP server in different subnets. Proxy DHCP server software can be obtained for both Windows and Linux. For Windows, Microsoft provides the Microsoft DHCP Relay Agent. For Linux, the Internet Software Consortium provides the Internet Software Consortium DHCP Relay Agent. Figure 9.7 illustrates the use of a switch to forward requests and responses between the PXE clients and the DHCP and PXE services. The switch must be configured to forward messages to the IP address of the DHCP server. If the DHCP and PXE services are running on different servers, the switch must be configured to forward all requests to both of the servers. Figure 9.7. Switch as DHCP and PXE relay. DHCP and PXE Security ConsiderationsBecause PXE is a relatively new protocol to datacenter environments, you need to understand the security considerations. A list of typical security issues follows, along with ways to avoid or alleviate them:
|
| < Day Day Up > |
EAN: N/A
Pages: 214