Implementation
|
|
Now comes implementation time. The following pages will provide guidelines for implementing wireless networks in a variety of settings.
Putting Together a Home Wireless Network
It is fairly simple to set up a home network. The advantage of going wireless at home is that one can use the DSL or cable connection in other rooms besides where the service comes in the house. For example, with a good wireless connection, you can sit outside on a nice day and answer emails and surf the Web. Also, a wireless connection can extend the broadband service to your living room and other parts of the house.
For the most part, it's okay to mix and match equipment from different vendors. The setup is relatively simple. You essentially plug the AP/router into the DSL or cable modem and run a short configuration program. Change your service set identifier (SSID) from the default value to something not too obvious. Then set up the client access card in much the same way. Use the same SSID for both your AP and client cards. Once you have it working without the WEP key, the most important part is to use the same WEP key for all the computers in your household and change it often. You can take some other security precautions such as limiting access using MAC filtering.
However, the WEP key department does have some gotchas. Older APs support only 40-bit WEP keys, whereas the new products support both 40 and 128 bit, but it does not stop there. The format of WEP key can be different from one manufacturer to another. Some vendors have you enter a pass phrase and others have you enter ASCII characters. The common denominator is the hex key, so the trick is to use the pass phrase to generate a hex key and use that everywhere else.
Putting Together a Larger Enterprise Wireless Network
In a larger enterprise, two things become a challenge. First of all, more than one AP will be required. This means a site survey and a frequency plan become necessities. Furthermore, APs will need to be of the commercial variety because they will need to be powered over the Ethernet and located in the ceiling. The other challenge is that security becomes more than the small matter of securing Aunt Jane's good jokes and your Quicken books. The company's trade secrets are at stake. A single WEP key now is no longer secure. Other security measures are now necessary, such as 802.1x/EAP and virtual private networks (VPNs). It's also necessary to document all your work so that it can be maintained.
Putting Together a School Wireless Network
A wireless school network can help students by bringing the computer lab to the students, rather than bringing the students to the computer lab. This means that computer applications can be used in classes like English, science, and math, rather than being taught as a side course. By having wireless computers, the deployment and setup becomes much simpler. Rather than having to wire every classroom for Ethernet, the school can be set up for wireless. Then about 16 laptops or so with integrated 802.11b cards can be put on a laptop cart that contains a bank of chargers. The advantage of using wireless connections is that students don't trip over the cords. The laptops will last a good morning on a charge. With an extra set of batteries, the laptops can be used again in the afternoon.
The real savings are in the space. The mobile computer lab requires very little room to store. Thus, the computer lab can be used as an extra classroom. The school requires about one AP per four classrooms on average. A typical elementary school requires about 10 APs, a middle school needs about 15 to 20, and a high school between 20 and 30.
The one difficulty with a wireless school network is the two classes of security. It's very important to separate the teacher's network where grades and attendance are kept from the network the students use to access the Internet and store files. However, this does not mean the two networks have to be completely separated from one another. By using Cisco's products, a virtual LAN (VLAN) can be set up for the students on a publicly broadcast SSID. It's probably best to make the SSID the same throughout the school district so that students can use their own personal digital assistants (PDAs) not only in their schools, but when visiting others in the same school district. An authentication scheme using 802.1x and an EAP scheme can be used to limit the access on the network. Username/password EAPs work well for older students that want to use their own computers and PDAs at school. The lab equipment will work well with 802.1x and EAP/TLS (Transport Level Security), which uses a certificate. This way, students don't have to enter usernames and passwords to use the lab machines, but the network is not left open to hackers, spammers, and others wanting to use the wireless connection to launch viruses.
Cisco's products also enable other hidden SSIDs to be associated with other VLANs. Those other VLANs can be routed such that they require authentication using an 802.1x and some EAP scheme. Soon EAP/SIM will be available so that only holders of an Subscriber Identity Module (SIM) card or a USB SIM plug will have access to the network. As an alternative, a VPN can be set up for teachers. The added benefit is that they can access their school computing resources from home.
How to Set up a Hotspot out of the Box
Net Near You,[13] Pronto,[14] and Toshiba[15] make it very simple to set up a hotspot for your local coffee shop, hotel, truck stop, or bed and breakfast. The best locations are those that want to promote more customers, that want customers to stay longer, and that are looking for ways to get repeat customers. It's as simple as ordering a DSL or cable connection that enables a resale of the circuit, or bringing in a wireless WAN (WWAN) connection from your wireless backbone and installing the hotspot in a box according to the directions (see Figure 7-30).
![]()
Figure 7-30: Using a hotspot in a box
The hotspot in a box may also contain the AP, or it may simply be a box between the AP and the DSL or cable modem. Depending on what is offered by the network, the box contains a capture portal, authentication software, a firewall, and a router.
The capture portal intercepts the initial web page and puts up an initial login page instead. The authentication software will assist in authenticating the user's username and password. Authentication may also include some identity from a scratch-off ticket or a number given to the user by the barista at the counter by the point-of-sale equipment (similar to the way car washes give you a five-digit number).
If you are a do-it-yourselfer interested in building a community hotspot, check out http://nocat.net. A group in Sonoma County, California, has built an authentication system called NoCatAuth. It makes shared Internet services possible by authenticating participants of the free network to a central authentication server. The server makes it possible to have three different classes of users authenticated by the box. The priority class is an optional class that allows the gateway owner (and anyone else he or she sees fit) priority access to the gateway's resources. The coop class is a mandatory class of service, which gives access to all participants of the cooperative. The public class is open to any unauthenticated roaming client and has the lowest access priority to gateway resources. This class is mandatory and may be defined that the public class is not open to everyone.
With NoCatAuth, a typical logon process goes like this: A roaming user associates with the AP and is immediately issued an Internet Protocol (IP) address from the Dynamic Host Configuration Protocol (DHCP) server in the NoCatAuth box. The user only has access to the authentication service. The user then opens up a web browser to an arbitrary page. Instead of getting the default page, the user's page is redirected to a secure login page. The user can make one of three choices: Click on a link to find out about the service that is being offered for membership, enter the login information, or click a "Skip Login" button.
If the login procedure is successful, the wireless gateway modifies its firewall rules to grant access to the user and brings up the original web page that the user was trying to access. Another small popup window is opened on the user's display that brings up the login page every few minutes. If the user moves out of range or closes the popup window, the connection is closed.
How to Set up a Hotel or MDU Hotspot
Setting up 802.11 in a hotel or multiple dwelling unit (MDU) is a little more complicated than setting it up in a coffee shop. It's likely that more than one AP will exist, the Internet connection must be shared for Internet access, and some wiring inside the hotel is needed. One way to do this is to run fiber from a centralized phone closet to all the floors of the hotel where switches that connect to APs are located, as shown in Figure 7-31. An authentication firewall prevents access to the Internet until the credentials for access have been presented. The hotel's access to the Internet is separate from the part that provides WLAN service. The hotel has its own firewall to prevent hackers on the Internet or the WLAN from gaining access to the corporate network. The authentication authorization and accounting for this type of deployment are similar to the options in a cafe-style hotspot. This type of installation works well when it is possible to pull fiber through the building. Installation of the fiber can account for 40 to 50 percent of this project's cost.
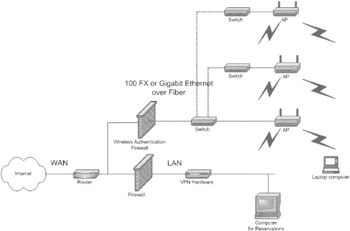
Figure 7-31: Hotel or MDU using fiber
However, when it's not possible to pull fiber, consider using the existing or surplus telephone wiring with a long-range Ethernet (LRE) router and modems. Figure 7-32 shows the architecture of such a system. LRE works well and is fairly inexpensive. However, many hotels don't have spare telephone lines or have the ability to reuse them.
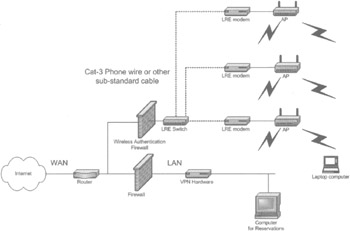
Figure 7-32: Hotel or MDU using LRE
As a last measure, you can bet the hotel has a cable television (CATV) plant. The option shown in Figure 7-33 is the most costly, but it requires very little installation. The broadband router is quite pricey at a cool $20,000 or so. One requirement is that the hotel has a two-way cable system. This means that at worst case all the line extenders need to be upgraded to two-way. The line extenders can run $1000 apiece.
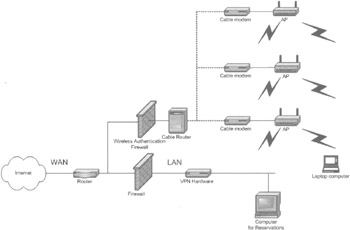
Figure 7-33: Hotel or MDU using CATV
How to Set up a Layered Office Hotspot
Layering allows an enterprise to share its WLAN for public access. Public hotspots can be created simply by allowing public users to share the WLAN and Internet infrastructure securely. Layering allows the enterprise to sell off its excess bandwidth or to allow public use of their Internet facilities to vendors and contractors without allowing them onto the corporate network. This same concept can be extended into residential areas if the DSL or cable service agreements allow resale of the Internet connection. Two companies, Sputnik and Joltage, have developed layering opportunities within the home network and in small office, home office (SOHO) markets.
To enable layering within an enterprise network, one can use an architecture similar to the one shown in Figure 7-34. Only the public SSID is broadcast. However, users can associate with either the public or the private SSID. The public one is used by the public users and the private one is used by the enterprise itself. The two SSIDs are linked to their own VLAN. The public SSID links to the public VLAN and the private SSID links to a VLAN that belongs to the enterprise. After being authenticated and authorized, users of the public SSID can access the Internet. In the same way, users of the private SSID can access the corporate network. The switch and router shunt traffic according to its VLAN ID.
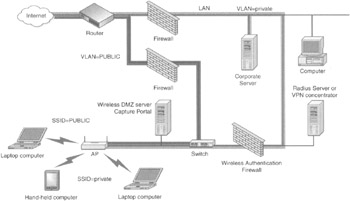
Figure 7-34: Using layering to provide hotspot service
Many VLAN systems allow up to 16 separate VLAN IDs. The 802.11 standard currently allows the broadcast of only a single SSID. The rest have to remain hidden but can be associated with the system. If the 802.11 rules could be slightly bent, up to 16 broadcast SSIDs could be supported by sending a different SSID in each broadcast message. This would allow multiple service providers to be supported.
As-Built Documentation
After installing a project, all areas by the installation need to be documented and photographed so that when a modification needs to be done, the As-Built documentation can be used as a reference.
A nice tool called NetViz[16] can be used to document the initial installation and any modification that is done to the network. NetViz is a program that helps you capture your network at all layers. You can import Visio drawings, CAD drawings, text files, and pictures showing rack elevations and installations. The diagrams enable you to drill-down from a nationwide or citywide view all the way down to the IP level.
[13]www.nnu.com.
[14]www.prontonetworks.com.
[15]www.csd.toshiba.com.
[16]www.netviz.com.
|
|
EAN: 2147483647
Pages: 96