Server Message Block (SMB) and the Common Internet File System (CIFS)
| A common protocol you will find on almost any computer running a Windows operating system, from early LAN Manager products to Windows Server 2003, is the Server Message Block protocol. This is a protocol used for basic file sharing and printer sharing, and for locating other network resources. It is a basic client/server protocol that uses request and response messages. SMB has also been used by many vendors other than Microsoft to provide file and print services, including IBM (OS/2) and Digital Equipment Corporation (now HP) in its Pathworks products. SMB has been around for awhile and has been modified to support new functions as PC networks have evolved. Each new version of the protocol is called a dialect . Table 35.1 shows the dialects in order from the earliest to the latest, and any server implementing a particular dialect must also support interaction with clients of any earlier dialect in this table. This allows for backward compatibility for older clients when parts of the network, such as servers, are upgraded. Table 35.1. SMB Protocol Dialects
SMB Message TypesSMB is a message-oriented protocol in which the client makes a request of the server using a message formatted according to a specific SMB message type. The server responds to the client's request using a specific SMB format. There are many types of messages, which are listed in Table 35.2. Note that not all message types are supported by all clients. The table is subdivided into sections showing at what point in the development of SMB-based networks a particular message type was introduced. Table 35.2. SMB Message Types
From the list in Table 35.2, it is easy to see that SMB has evolved over the years and has a specific command set that provides detailed functionality while maintaining simplicity by using a simple message exchange format. Most LAN analyzers have the capability to decode SMB packets, and you can troubleshoot SMB client/server sessions to observe the interaction of the commands shown in the table. SMB Security ProvisionsSMB has the capability to provide for two kinds of security for file sharing:
The most basic level of security that can be used on an SMB network is share-level security. This approach offers a disk or directory as an available resource on the network, protecting it with a password. Users who want to access a resource that is protected at the share level need only know the name of the resource, the server that offers it, and the password for it to make a connection. This kind of file sharing is usually employed by Windows 9x/Me computers configured as a workgroup, in which using domains and the Active Directory would require too much administrative overhead ”not to mention expense. In a small LAN in which there is not a great need for a high degree of security among users, it is simple to set up and maintain a network based on this model. A superior method that is more likely to be found in the business environment involves making users accountable for accessing resources. A user-level security model dictates that each user should log in using a unique identifier, called a username , which is associated with a password for the user account. After logging in to the network, users are granted access to resources based on the rights accorded their accounts (what the user can do) and the resource protections placed on files or directories (what the user can do with the resource). This user-level method enables you to assign different kinds of access based on username and resource.
In the share-level security model, access to a share enables the user to access any files in the top-level directory of the share and all the files in all the subdirectories that might fall under the top-level directory. In the user-level security model, the administrator can place different access limitations on every directory, subdirectory, and file that exists in the share. The earliest SMB clients do not have the capability to exchange an account name and password with a server and are thus limited in what they can do in a more modern environment. SMB servers will generally provide some functionality for user-level security. For example, if the client computer's computer name matches an account name that is known to the server, and if the password that the client passes as a "share" password matches that of the account, the SMB server can perform a logon for the user and grant access to the resource. Protocol Negotiation and Session SetupSMB has a built-in mechanism that is used by the client and server to determine the other's capabilities so that a common protocol version can be established that the two will use for the network connection. The first SMB message that the client sends to the server is one of the SMB_COM_NEGOTIATE type. The client uses this message to send the server a list of the dialects it understands. The server selects the most recent dialect it understands from the client's list and returns a message to it. The response the server returns depends on the type of client. The information includes the dialect selected and can include additional information, such as buffer sizes, supported access modes, time and date values, and security information. After the client receives this response, it can continue to set up the session by using the SESSION_SETUP_ANDX message type. If the initial server response indicates that user-level security is being used, this message type can be used to perform a user logon. The client sets a value in the message header called the UID (user ID) for the account it wants to use. It also supplies the account name and password to the server by using this message type. If these values are validated by the server, the user can continue to use the UID to make subsequent accesses . Other setup functions that are performed by using SESSION_SETUP_ANDX include the following:
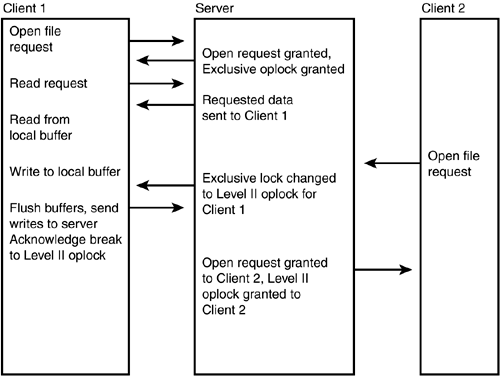
If the VC passed to the server is zero and the server has other circuits open for the client, it will abort those services, assuming that the client has rebooted without freeing those services first. To properly close a session, the client uses the message type LOGOFF_ANDX , which causes the server to close all files associated with the user's UID. Accessing FilesOther SMB message types are used to traverse the resource directory and to open, read, write, and close files. First, the user must connect to the resource by using the TREE_CONNECT message. The message includes the name of the resource (server and share name) and, for earlier clients that do not perform logons , a shared password. The server responds by sending the user a value called the TID (Tree ID) , which will be used in SMBs exchanged for this connection. After the connection has been established, several basic SMB command formats can be used to manipulate files and directories that reside on the share. For example, the CREATE_DIRECTORY message is used to create a new directory in the file share's directory structure. The client passes the pathname for the new directory, and the server creates the directory, provided that the client has the appropriate access rights or permissions. The DELETE_DIRECTORY SMB message can be used to remove a directory, again based on the functions allowed for the username. Opening and Closing FilesThe OPEN message is used by a client to open a file. The path for the file is given, relative to the file share root. The client specifies the access that is desired, such as read, write, or share. If the file is successfully opened, the server returns a File ID (FID) to the client, which is used to further access the file using other SMB message types; it is similar to a file handle, which most programmers will recognize. The server also returns data to the client indicating the actual access that was granted, which is read-only, write-only, or read/write. The CLOSE message is sent by the client to tell the server to release any locks held on the resource file held by the client. After this message, the client can no longer use the FID to access the file, but it must instead reopen the file and obtain a new value. When a client does not know the exact name of a file that it wants to open, the SEARCH message can be used to perform a directory lookup. This function enables wildcards to be used, and the server response can include more than one filename that matches the request. Reading and WritingThe SMB protocol uses the READ and WRITE message types to perform I/O operations on a file for the client. Using the READ request, a client can request that the server return information from the file by specifying a number of bytes and an offset into the file. The server returns the data, indicating the actual number of bytes returned, which can be less than requested if the user tries to read past the end of a file. The WRITE command updates a file in a similar manner. The client sends in the data that will be written, indicating the number of bytes to write and an offset into the file where the write operation will begin. If the request causes a write past the end of the file, the file is extended to make it larger. The server sends a response telling the client the number of bytes that were written. If the number is less than the requested value, an error has occurred. To increase read/write performance, the READ_RAW and WRITE_RAW message types can be used to exchange much larger blocks of information between the client and the server. When these are used, the client must have only one request issued to the server. In one send, the server will respond with data that can be as many as 65,535 bytes in length. The WRITE command works in the opposite direction, allowing the client to send a large buffer of raw data to the server for a write operation. Locking MechanismsLocking allows a particular client exclusive access to a file or a part of a file when it is shared on the network. In SMB, the capability to create a lock is called an opportunistic lock, or oplock for short. This is better explained by looking at the way in which it works. A client can create a lock on a resource using three kinds of locks. The first is an exclusive lock, in which the client has exclusive access to the data held by the lock. A batch oplock is one that is kept open by the server when the client process has already closed the file. A Level II oplock is one in which there can be multiple readers of the same file. The locking process consists of the client requesting the type of lock it wants when it opens the file. The server replies to the client with the type of lock that was granted when it responds to the open request. A lock gives the client the capability to efficiently manage buffer space it uses when accessing a file over the network. For example, if a client has exclusive access to a file and is performing writes to it, it can buffer a lot of the newly written information before having to send it to the server to update the file. This can provide a reduced number of network packets when updating a file. A client that has an exclusive lock on a file can also buffer read-ahead data to make reading a file much faster. These locks are called opportunistic locks for a reason. A client can be granted exclusive access to a file if no other client has it open at the time of the request. What happens when another client needs to read the file? The server notifies the first client that it needs to break the exclusive lock. The client then flushes its buffers so that any data that has not been written to the file is processed . The client then sends an acknowledgment to the server that it recognizes that the exclusive lock has been broken. In Figure 35.1, you can see the interaction between two clients and a server as these messages are exchanged. Figure 35.1. Exclusive oplocks are changed to Level II oplocks when a second client wants to open a file. Batch oplocks are used to reduce the amount of traffic on the network when some programs require continual reopening of a file to obtain commands, as when a batch command procedure is executed. For example, a batch procedure executed by the command processor usually opens a file, locates the next line to be executed, reads that line, closes the file, and then executes the command. The problem with this is that these steps are taken for each command line in the procedure, resulting in multiple file open/ closes that are not really necessary. This procedure for reading individual lines from a file is done by using a batch oplock whereby the client can read the data from its local read-ahead cache instead of reopening the file on the remote server to get each line. Level II oplocks were new with the NT changes to SMB. This kind of lock allows more than one client to have a file opened for reading. When a client must read from a file that is opened by another exclusively, the server informs the current client that its exclusive lock has been broken and is now a Level II oplock. No client that has a Level II oplock will buffer data to or from the file. Thus, after the lock has changed to a Level II oplock (and the first client has flushed any data in its buffers), both clients can continue reading the file. Using NET CommandsThe set of NET commands form the basis for a command-line interface that the client can use to access SMB-based file services. For server functions, the NET commands allow you to create and configure shares, manage users and groups, and more. This command, with its many command-line parameters, can be used to make a directory available for sharing, to connect or disconnect a resource, or to view resources available on a server, among other functions. Clients using operating systems such as Windows 98/Me or Windows NT/2000/XP/2003 can also use Microsoft Windows Explorer to connect to file resource shares on the network. However, the NET command provides a simple interface that also can be incorporated into command procedures, such as user login script files. You can also use these commands during troubleshooting. For example, you can establish a telnet session with a remote client who is having problems with a file share and execute the NET commands directly via the Command Prompt window. When present at the actual computer that is experiencing a problem, you will probably get more information by using commands than by using the GUI interface. The exception to this is the Event Viewer, which can give you valuable guidance by narrowing down the problem that generated an error. Reading the Event Viewer records can be confusing, and they are often easily interpreted only by experienced personnel. Yet, using the Event Viewer, you can at least determine such basic conditions as a bad password, a nonexistent user account (create it), and other simple items that often show up in day-to-day network activities.
Because the NET command can be a useful tool both for setting up users to connect to resources and for troubleshooting clients, it is worth looking at the basic functions you can perform using this command. There are several command parameters you can use with NET . For file sharing, these are the most basic commands:
NET SHAREThe NET SHARE command enables you to offer a disk or directory structure for sharing on the network. If used by itself with no other parameters, the command will show you the current shares that are being offered by the workstation or server, as in the following example: C:\>net share Share name Resource Remark ------------------------------------------------------------------------------- IPC$ Remote IPC D$ D:\ Default share print$ F:\WINNT\System32\spool\drivers Printer Drivers E$ E:\ Default share C$ C:\ Default share F$ F:\ Default share ADMIN$ F:\WINNT Remote Admin documents d:\ HPLaserJ LPT1: Spooled HP LaserJet 6L The command completed successfully.
In this example, you can see that SMB is used not only to provide network communications for file sharing, but also to provide shared printing ( HPLaserJ LPT1: ) and interprocess communications ( IPC$ ). The basic syntax for sharing is as follows : NET SHARE sharename Entering just this command will return an error message, because you haven't specified what is to be shared. To make a directory available for sharing, specify the name you want the file share to use on the network, and follow it with the path to the directory to be shared: NET SHARE sharename = drive:path You can further configure the share by using the following qualifiers:
See the following example: F:\>NET SHARE ACTFIL=D:\ACCTPAY /USERS:5 ACTFIL was shared successfully. This code offers the file share actfil on the network. It allows as many as five concurrent connections to the files contained in the directory D:\ACCTPAY and all subdirectories that fall under it. Deleting a file share on the server is also a simple matter: F:\>NET SHARE ACTFIL /DELETE ACTFIL was deleted successfully. In this example, you can also specify the pathname that is being shared: F:\>NET SHARE D:\ACCTPAY /DELETE ACTFIL was deleted successfully. D:\ACCTPAY was deleted successfully In both of these instances, the actual directory that was offered for sharing is not deleted. Only the file share is deleted. Troubleshooting Using NET VIEW and NET USEThese two commands enable you to view the resources available on the network and then make connections to them. NET VIEW returns a list of the servers it knows about on the local network. You can use NET VIEW \\ servername to get a list of services offered by any server in the list, as in the following example: F:\>NET VIEW \bcanjs1 Shared resources at \bcanjs1 Share name Type Used as Comment ------------------------------------------------------------------------------- acct Disk Accounting cdrom Disk CD Drive on BCANJS1 documents Disk dvdrom Disk DVD Drive on BCANJS1 HPLaserJ Print HP LaserJet 6L Rschlz Disk Restricted The command completed successfully. It is easy to get confused when trying to troubleshoot problems with users connecting to shared resources. If you are using a Microsoft-based network that provides file sharing through SMB mechanisms, the NET VIEW command can be extremely useful. You can determine from this command whether the remote resource server is even seen in the browsing list by the client computer. If it is, you can display the resources offered. To connect to a resource manually, you can use the NET USE command. When executed by itself with no other command-line parameters, this command displays a list of your current connections. To make a new connection, the syntax is very basic, though it has variations: NET USE device sharename Here, device can be an actual drive letter (such as D: or E: ), a device name for a printer ( LPT1: ), or the wildcard * , in which case the next available drive letter will be chosen automatically when the connection is made. Observe the following example: NET USE X: \BCANJ1\DOCUMENTS
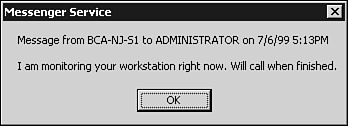
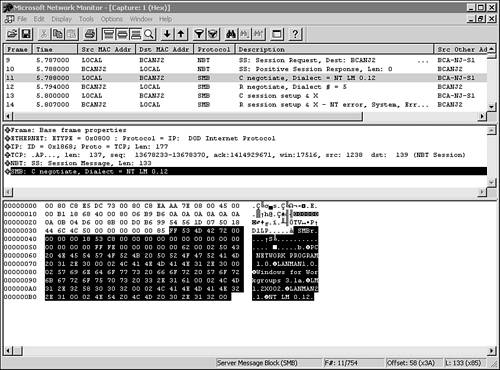
This attaches the drive letter X: to the resource documents on the server BCANJ1 . You can also specify a username that can be used to evaluate your access rights to the remote resource: NET USE X: \BCANJ1\DOCUMENTS /USER:[ domainname \] username Here, you would specify a valid username and, if it is a domain account, the name of the Windows domain. To delete a connection to a remote resource, use the /DELETE qualifier: NET USE X: /DELETE The NET USE command is most often associated with creating user logon scripts or other batch-oriented procedures that are used to interact with files offered as resources on a network. It can also be a very handy command to remember when performing a new installation or upgrading a user. For example, when installing a new application or troubleshooting a misbehaving one, you can quickly connect to a remote resource to download configuration or driver files. Monitoring and Troubleshooting SMB CommunicationsYou can use the NET STATISTICS command to obtain a quick view about statistics related to the SMB protocol. Use either WORKSTATION or SERVER as a keyword to indicate which set of statistics you would like to see, as in the following example: F:> NET STASTICS SERVER Server Statistics for \BCA-NJ-S1 Statistics since 11/09/02 05:45 PM Sessions accepted 1 Sessions timed-out 0 Sessions errored-out 0 Kilobytes sent 3 Kilobytes received 3 Mean response time (msec) 0 System errors 0 Permission violations 0 Password violations 0 Files accessed 7 Communication devices accessed 0 Print jobs spooled 0 Times buffers exhausted Big buffers 0 Request buffers 0 The command completed successfully. From this display, you can quickly see whether a server is having problems with a recent password change ”password violations will probably be excessive. A high value for permission violations can indicate that an access control list on a file or directory might have recently been changed. The other statistics shown here also can be used for many different troubleshooting scenarios. The NET command has the capability of showing you a lot of information. For example, in addition to giving SMB statistics, the NET command can be used to show the services currently running on an NT/2000 or Windows 2003 family of operating systems. Using the NET START command with other parameters on the line displays a list of the services currently running. If you are troubleshooting a client and see, for example, that the Workstation service is not running, you can use the NET START WORKSTATION command to start it. The NET command enables you to view, start, and stop services without having to use the graphical interface and can be a great help when performing remote diagnosis. When you upgrade a network or make repairs , it is often useful to send a message to users to let them know what is happening. For example, replacing a network card might require that a server be out of commission for a short time. Changing a network cable might disrupt network access for users. You might have established a telnet session with a user's workstation and want to send him a message on the screen to let him know that you are working. You can use the NET SEND command, using the following syntax, to send a message to users: NET SEND { name * /DOMAIN[: domainname ] /USERS} message Here, you can see that you can send a message to a single user or use the wildcard * character to send the message to all users. You can use the /DOMAIN: domainname variation to send the message to all users in a particular domain, for example. See the following command: NET SEND * I am monitoring your workstation right now. Will call when finished. When logged in to a server, this command produced the pop-up message on the terminal of the logged-in user shown in Figure 35.2. Figure 35.2. The NET SEND command can be used to send a message to users when you are logged in to their workstations. To carry problem diagnosis any further when using SMB for file sharing, you need to resort to a LAN analyzer of some kind. You can use this to verify that the correct SMB messages are being exchanged between the client and the server. In Figure 35.3, you can see the Microsoft Network Monitor being used for this purpose. Figure 35.3. Using Microsoft Network Monitor, or a similar LAN analyzer, you can examine the exchange of SMB packets between the client and the server. You can step from one packet to the next to discover where a problem might be occurring. For example, is a password required? Are there problems with opening a file? You can watch the sequence of commands that are used to connect to a tree, open a file, and make an attempt to read or write. The Windows 2003 family of servers offers a slightly different view of the Microsoft Network Monitor, as shown in Figure 35.4. Figure 35.4. The Windows 2003 family of servers' Network Monitor has an updated interface. In Figure 35.4 you can see a simple example of tracking network performance. You can customize this tool to further capture and display network packets just as you can in Windows 2000. Although it would be necessary to have more detailed information about the format of SMB packets to make a detailed diagnosis at this level, it is still very helpful to be able to see the types of messages being exchanged, regardless of whether you can understand every byte in the packet. Viewing the data at this level can be used to troubleshoot most problems with this protocol. You also can use the event-logging capabilities of Windows NT/2000 and the Windows 2003 family of servers (the Event Viewer) to look for problems. For example, if you have a password failure and have set the server to audit failed resource accesses, the Event Viewer will have a record showing you the failed attempt, and you can quickly resolve the problem by giving the user the correct password or by changing it. The Event Viewer can also let you know whether the network services installed on your server were started correctly, or encountered problems. The Microsoft Network Analyzer is covered in more detail in Chapter 53, "Network Testing and Analysis Tools." Using the Event Viewer is covered in Chapter 47. Using the SMB/CIFS Protocol on Non-Microsoft Clients: SambaSMB/CIFS is a protocol that is highly entrenched in the Microsoft world of operating systems and networking products. It makes sense, then, that there would be a way in which these workstations and servers could be integrated into a Unix/Linux environment without a lot of difficulty. The answer to this problem is called Samba, which is a set of products that provide for SMB conversations between SMB servers, such as Microsoft Windows operating systems, and those that do not use it natively, such as many different variants of Unix or Linux systems. In addition, Samba has been ported to several other popular operating systems, including OpenVMS.
Samba was originally developed by Andrew Tridgell and is now maintained by him and other developers (the "Samba Team") on the Internet. You can go to the home page for the Samba effort by using the URL www.samba.org. From this Web site you can choose a mirror Web site for your country, and then you can view the documentation for Samba and download the most recent version. The software is freely distributed under the GNU public license. You can configure Samba servers on your Unix boxes to enable high-performance machines to be used as file servers on the Windows network. You can still manage the servers using Unix file administration procedures, and yet to the client computers, the shares appear no different than those offered by other Windows-based file servers. Troubleshooting a Samba server can be made easier by starting the Samba server software using the -d parameter to specify a debug level (from 1 to 100), which will cause more output messages, depending on the level you specify. You can also use a LAN analyzer to view the sequence of exchange of SMB messages between server and client. Available as a download from the Samba home page is an extension to the tcpdump utility, called tcpdump-smb . You can use this to capture smb packets and decode the header information. The Common Internet File System (CIFS)CIFS is intended to be a replacement, or an upgrade, of the SMB protocol. Design considerations include making it platform-independent. While SMB resides in the NetBIOS legacy environment, CIFS runs on top of TCP. Other improvements over SMB include the following:
CIFS is basically an enhanced version of SMB and still uses server message block messaging. Better security and the use of DNS are necessary additions if the protocol is to be used on the Internet. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
EAN: 2147483647
Pages: 434
- Context Management of ERP Processes in Virtual Communities
- Distributed Data Warehouse for Geo-spatial Services
- Intrinsic and Contextual Data Quality: The Effect of Media and Personal Involvement
- Healthcare Information: From Administrative to Practice Databases
- Development of Interactive Web Sites to Enhance Police/Community Relations