Access Points and Ad Hoc Networks
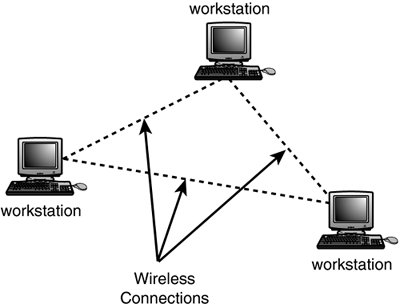
| Before getting into the specifics about IEEE standards and how data is transmitted on radio frequencies, you first should look at the topology a wireless network can take. In Chapter 2, "Overview of Network Topologies," you learned that a wireless network doesn't use a bus topology. Instead, because in some situations all nodes can hear all other nodes (within a specific area), one wireless topology can be considered a mesh topology. That is, in the simplest wireless network, all stations participating in the network can hear and talk to all other stations in the network. In a traditional wired network, this is equivalent to having a network card make a cabled connection to every other node in the network. Another topology used in wireless networks involves using an Access Point (AP) that operates much like a hub or switch but incorporates a few extra features, such as provisions for some security issues. Ad Hoc NetworksA simple peer-to-peer network, composed of computers that have compatible wireless network adapter cards, can be used to quickly set up a small network on-the-fly . This kind of workgroup LAN can be useful when only a few stations need to communicate in a small geographical area (see Figure 19.1). You can set up your own individual network at a trade show, in a conference room, or even for an entire small-business enterprise. Wireless bridges, which you'll learn about in Chapter 24, can extend the distance between wireless Access Points so that in a business you can create a network without having to pull cables at all. For a home office, where you probably don't want to drill holes in your walls and pull cables, wireless products can be the best solution possible. Figure 19.1. All you need to create a network on-the-fly are a few computers, each with a wireless network adapter. This network is referred to as an ad hoc network because it involves simple peer-to-peer connections in a wireless environment. No central hub or switch coordinates the communications that occur. Instead, any computer equipped with a compatible wireless adapter can join the ad hoc network, provided that the appropriate security mechanisms have been implemented. For example, if you are using a Windows operating system and a simple workgroup setup for network communications, any computer that uses that same workgroup name can join your small ad hoc network. If any file or print shares are offered by members of this ad hoc network, you can protect them by using a password. This is not a great way to protect files, because anyone who needs to map to a resource share will use the same password.
If you use more secure methods , such as a Unix system with each workstation requiring a username/password, you can create a more secure wireless ad hoc network. The same goes for using a Windows domain. The only difference is that the network is wireless ”there are no cables ”and the same security mechanisms you'd use for a wired network should be used for this simple peer-to-peer network.
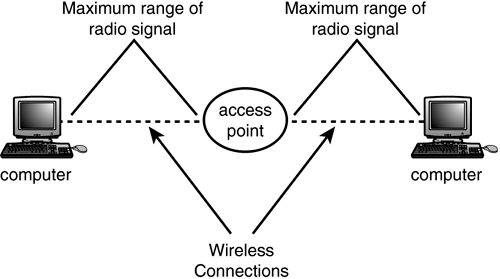
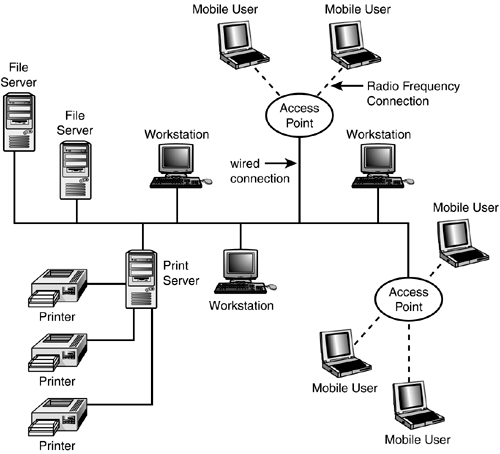
Using an Access Point to Mediate Wireless CommunicationsYou also can use a wireless AP to create a small wireless network. This device can also be attached to a wired network, which is discussed next , or as a standalone device that can effectively double the distance of the wireless network. As you can see in Figure 19.2, if the Access Point device is placed in the center of the network, each computer equipped with a wireless network adapter can be placed farther away from other computers. This is because each computer only needs to be able to communicate with the AP, which in turn relays the signals to other computers that participate in the wireless LAN. Figure 19.2. As you can see, an AP can double the range of a wireless network. You can add APs to a traditional wired network as well; the APs will serve the same purpose that hubs or switches do for your wired clients . The AP coordinates communications to and from the wireless computers and the rest of the network, whether the destination resides on copper or fiber- optic cables (see Figure 19.3) or within the range of another wireless Access Point. Figure 19.3. APs provide the connection to the wired network for mobile users. Because multiple APs can be placed throughout the network, this topology allows for a wider geographical range for mobile users. An AP is a simple and very inexpensive device that can connect to the wired network and provide a transmitter/receiver that can be used to communicate with mobile users' workstations. In addition to providing the wireless communications service, an AP typically is responsible for buffering data between the wireless clients and the wired network. Unlike an ad hoc wireless setup, the AP also is responsible for mediating communications between wireless clients that operate within range of the same AP.
Most of the consumer devices on the market today support 11 “60 wireless clients on a single AP at any given time. However, your mileage can vary depending on the manufacturer. For example, Cisco offers APs that can scale up to 200 or more wireless devices. Many tests by magazine labs, as well as others, indicate that you will not get the full bandwidth, much less close to it, when using wireless transmissions. The ballpark figure, based on several examples, is about one-third to one-half of the bandwidth the technology specifies. You may indeed get close to 90% throughput under ideal conditions. However, all wireless technologies suffer from the fact that barriers (such as large buildings ) do exist. Keep this in mind when deciding what kind of network traffic to use in the wireless part of your network. In an outdoor environment, you will probably get a much greater distance between client and AP before the bandwidth begins to degrade. APs come in all sizes and shapes . For example, D-Link (www.d-link.com) offers Access Points (called wireless routers) that can connect IEEE 802.11b, as well as 802.11a through 802.11g products. Thus you don't have to worry about your previous investments in 802.11b equipment (or sooner, 802.11a devices). If all can work together, your replacement policy can concentrate on such things as the actual client's bandwidth requirements. Another vendor for consumers or SOHO clients is NETGEAR (www. netgear .com). For enterprise networks where a large number of APs will be needed, and for which greater security is required, networking hardware is generally purchased from an existing vendor. This may result in using one vendor for all networking products, or several. For example, Cisco and Apple both offer their wireless networking options, from network cards to APs to special antennas. Cisco's main offering is a line of products named Aironet. There are many products in the different Aironet series. Apple was one of the first computer companies to bring wireless networking to market with its AirPort product line. The newest product, the 54Mbps AirPort Extreme, is based on IEEE 802.11g (see Chapter 22), supporting both 802.11b and 802.11g (11Mbps to 54Mbps). Shop around and you will find that many wireless products are now commodity items. With trade associations doing their best to nail down specifications for each new technology, you can expect to see even better hardware in the near future, and for a much lower cost than today. Someday soon you'll have that Dick Tracy watch, if you know what I mean, but it will be connected to a Star Trek computer. |
EAN: 2147483647
Pages: 434