Implicit and Explicit Tagging
| In more modern VLAN switches, the individual network devices or ports are not used to define the VLAN; the network frameseach handled on a case-by-case basis that the switch receivesare used. A modern VLAN, then, is based on frames, not on the computers that generate them or those to which they are addressed, or the ports to which either is attached. In VLAN terminology, the term tagging is used to indicate what data is used to associate a frame with a particular VLAN. There are two kinds of tagging: implicit and explicit. Implicit TaggingImplicit tagging means that the decision is based on data that is already present in the existing frame format, such as an Ethernet frame. The data is already there, and nothing has been added; so the switch simply must examine data in the frame header and implicitly decide to which VLAN it belongs. When this type of tagging is used, no additional data needs to be added to the frame by the sending computer, so the devices on the network are considered to be VLAN-unaware. That is, they operate just as they normally would and have no idea that they are on one or another VLAN. You might as well just call this "nontagging," but the writers of the specifications have chosen to call this implicit tagging. When implicit tagging is used, the frame data that typically is used to create VLAN association rules is generally one of the following:
Another method that can be used for implicit tagging involves upper-level applications. However, because this can create literally hundreds of rules, it often is not used except in large WANs. This technology is called "explicit tagging." Explicit TaggingExplicit tagging refers to actually attaching an extra few bits of data to a network frame to specify its VLAN association. For this method to work, however, the sending station must be aware that VLANs exist. The switch itself also must understand explicit tagging and know where in the frame to look for the tagging data. For example, in a VLAN-aware network adapter, it is common to place a few bytes after the source address in the Ethernet frame. These additional bytes provide the explicit VLAN tag that the switch can examine to determine which VLAN the frame belongs to. Instead of having to apply a set of rules, the VLAN-aware switch can simply examine this value and quickly switch the frame to the correct output port. Because the tag is placed inside the Ethernet frame after the source and destination address, however, a switch that is not VLAN-aware (that is, does not use explicit tagging) cannot make decisions based on protocol type or other fields. This is because additional fields will be offset a number of bytes, depending on the length of the explicit tag. This can lead to nonaware switches or computers misinterpreting the tagging data and producing unpredictable behavior. The solution to this problem is to use "edge switches" that receive explicitly tagged frames from VLAN-aware devices and remove the tags when they forward the frame to a port connected to another switch or device that is not equipped to handle explicitly tagged frames. Explicit tagging does have some advantages over implicit tagging, however. Because the switch only has to look at the tag, and it's always in the same place (for a given protocol), it's easy to implement in hardware a quick switching fabric that can handle a large number of frames in a short period. Implicit tagging must check the rule set to determine what VLAN a frame belongs to, and this can involve more processing time. Although the amount of time might be just a few milliseconds, which seems like a short time to you or me, that's a lot of time when you're switching hundreds of thousands of packets in a short period. As you'll find out in the next chapter, a similar situation occurs with routers. A switch forwards a network frame quicker than many routers because the router must spend time digging into the frame to find the protocol address, and then perform a lookup in a routing table to determine how to deal with the frame and recalculate the frame check sequence (FCS). On the downside, when a switch that uses explicit tagging has to forward a frame to a switch or device that does not, it must remove the tag. When this happens, it's necessary to recalculate the FCS value because some of the frame bits have been removed. Another drawback is that attaching an explicit tag to a large frame can cause the frame to exceed the maximum size allowed by the transport protocol, and the frame will be dropped. MAC Address VLANsIf you have a lot of mobile users, creating a VLAN that bases its membership on a list of MAC addresses can be a good idea. Because these addresses are unique, when you plug into any switch port, a quick lookup is all that's necessary for the switch to determine which VLAN your computer's MAC address belongs to. And because MAC addresses are typically the way traditional switches work, there's not much more circuitry or software that has to be tweaked to create this kind of VLAN-capable switch. The downside is that the administrator must manually assign each hardware address to the correct VLAN in the first place. However, that's not a difficult chore when you are simply adding a few new computers to a VLAN. When implementing a set of VLANs that involve hundreds or thousands of computers, you can get tired fingers! If you decide to use this type of switch, there is one thing you should check before purchasing the switch. What happens when a computer is connected to a port and the computer's address is not a member of any of your configured VLANs? Some switch manufacturers will implement a mechanism that looks into the frame further and then forwards the frame based on a higher-level protocol address. This allows anyone to connect to your switch, provided that you've not taken the necessary physical security precautions and locked your switching equipment away in a secure computer room. Check to be sure that frames which have no VLAN mapping for a MAC address are dropped before using this type of switch. Protocol Rule-Based VLANsIn a virtual LAN, a switch's decision as to whether to output a frame on a particular port can be based on a set of association rules that are based on the network protocols used on the network. Each frame received on a switch port is examined and, based on a set of rules, is output on one or more other ports. The set of rules can be based on many things, such as the IP subnet addresses. However, it's quite possible to create VLANs that subdivide even a subnet.
Other protocol-based VLANs can be created so that AppleTalk- or NetWare-based (IPX/SPX) networks all can exist on the same set of switcheseach on its own virtual LAN. In this kind of protocol-based VLAN switch, you usually can further subdivide each major protocol into smaller VLANs based on identifiers used in the protocol headers. One factor to consider about protocol-based VLANs is that if the computer is running multiple protocol stacks (such as TCP/IP and IPX/SPX), the switch can be configured to allow the device to participate in separate VLANs based on these protocols. Because this kind of switch enables you to join diverse kinds of networks, it still is quite popular, and you'll find that it is possible to buy this type of switch inexpensively. Decision trees that are used to map different protocols into separate VLANs have been implemented in hardware, which is faster than having to use software and a processor to examine frames, extract the protocol information, and then make the forwarding decisions. For the standard IP-based network, using a switch that bases VLANs on IP subnets has another advantage. If you don't choose to divide the subnet itself into further VLANs, the switch can, after you've associated an IP address with the LAN adapter card, extract the MAC address from the frame, and from then on use the hardware MAC address to make decisions. Thus, when you move a computer from one location to another on the switch (or a series of interconnected cooperating switches), you won't have to change the IP address of the computer. The new port simply looks at the IP subnet address and creates an entry in its table for the MAC address, and it's basically plug-and-play (or I guess that should be "plug-and-work"!). Using Explicit Tagging on the Network BackboneIt should be obvious by now that most of the network adapter cards that exist in the world today were not created with explicit tagging in mind. Switches that use explicit tagging are used for the most part in large WANs, such as the Internet. However, LAN switches have evolved to the point that for most small LANs, a VLAN-unaware switch will serve just fine in a small network of a few hundred computers. However, when you connect a large number of these VLAN-unaware LANs to the network backbone in a larger network, as in a college campus or a large business, the core switches that connect these LANs must handle a much larger amount of network traffic. Thus, it's typical to use explicit tagging for large, high-capacity network switches than it is in smaller LAN environments (see Figure 9.3). Figure 9.3. Explicit tagging can be employed in the network backbone to connect LANs that are not capable of using explicit tagging.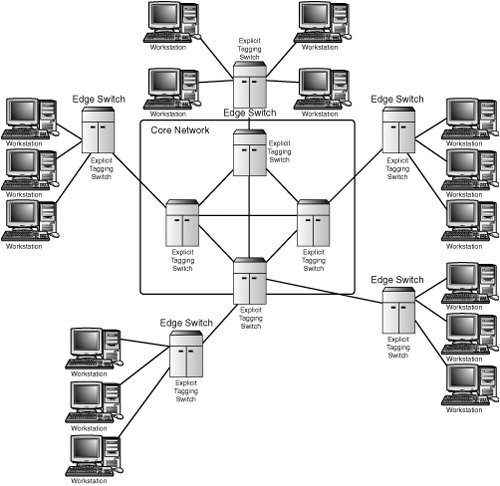 Here, the core switches that use explicit tagging are able to forward packets they receive within their switched network that understands the tags applied by the edge switches. The edge switches, however, add tags to frames they receive from the VLAN-unaware workstations, based on implicit tagging rules the administrator has set up. They remove the tags when they output frames to the individual workstations that are VLAN-unaware. Of course, these edge switches could just as easily have other switches attached to them, cascaded until you reach the end workstation or other network device. In this illustration, separate workstations are used to simplify the example. The edge switches could be connected to other switches that further subdivide the network and could use implicit tagging to forward the frames they receive from the edge switches.
Within the core of switches that do understand tagging, switching is done at a fast pace. Although some people still debate the use of MPLS, it is now used as a major protocol in the Internet core switches, due to the lack of any other standard protocol that might be used to replace it. |
EAN: 2147483647
Pages: 411